Bank robbers still exist, they’ve just evolved. Instead of putting on a ski mask and grabbing money from the teller, they’re targeting credit cards in sophisticated ways from the comfort of their own homes.
In 2006, the major cardholder companies in the United States created a council and set of data security standards for the payment card industry (PCI Security Standards Council), but payment card industry data is still being surreptitiously accessed at a striking rate. If there’s been a push for companies processing credit cards to protect the data, why are we still seeing so many payment-related breaches?
There are several reasons for this seeming paradox, but there are also solutions. We can decrease the amount of consumer data compromised if businesses better understand and focus on security over compliance, the consequences of a card data breach, and best practices for PCI security.
Compliance vs. Security
There is a stark difference between being secure and being compliant. PCI has a standard set of data security practices that will help companies protect their customers’ credit card data, but if your organization doesn’t put the effort into administering proper protections, these standards are virtually meaningless.
Often, organizations lack the resources or knowledge base to distinguish between secure and compliant. They either can’t afford the efforts to improve their security measures, they simply don’t know what those efforts should be, or they put too many resources toward areas that do very little to protect the data. The tools, devices, and practices that can help these organizations secure customer data are unknown. This creates vulnerabilities in the data housed or causes companies to spend more on security than what is needed.
And, those same organizations often mistake compliance for good security. Compliance tends to only cover portions of what we consider to be good security practice. If you’re doing the bare minimum just to comply with required regulations, it’s unlikely that you are protecting data in the most effective way you possibly can—and that leaves your data (and your customers’ data) at risk.
You can learn a lot from compliance too, though. While the tendency might be to focus your initiatives based on your understanding of the requirements that PCI has established, this can lead to arguing with the auditor instead of listening to what the auditor can teach about compliant and secure configurations.
It’s important to build a culture within your business that recognizes compliance as a decent starting point to security, but not the end goal.
Consequences
Candidly, the fine for not performing an annual PCI validation is typically so small that companies will often skip the steps of following the PCI data security standard because it is difficult to understand and there is always something more important to do. But not taking efforts to secure card data significantly increases the likelihood of a breach.
The ramifications for this can be devastating, especially for small organizations.
Risk of Closure
When compromised data is discovered, payment brands may treat companies that chose to pay the penalty and not follow the PCI security compliance standard differently than they do with companies who tried to validate their compliance annually.
Because the ignorance of the company caused the compromise of customer data, the repercussions are more serious. Because of this, sometimes when small organizations get breached, there are fines that are so large that they must close their doors for good because they are unable to make up the losses.
Depending on the size of the business that’s compromised, the severity of their noncompliance, the number of times the business has been in violation, and the bank, fines can be from $10,000 to $100,000 per month and may grow with monthly compliance reassessments. A small- or medium-sized merchant is likely not able to afford those fines, and they may have to close shop with penalties this large.
Plus, if the business keeps proving incompetence and noncompliance, their privileges of taking card payments may be revoked entirely.
That’s not the only threat to a small business that gets compromised, either.
Reputation
Customer loyalty is an important factor of PCI security. When you take credit card payments from customers, they are assuming that you’re keeping their data safe. Any data compromise may also be considered a breach of confidence—especially a compromise that involves financial information.
We see this a lot in smaller communities and with older populations. We worked with a small company that had four locations in four separate small communities. One store was compromised and had to close. This incident made them nervous that their customer base and the community wouldn’t remain loyal if they allowed their card data to be compromised at any of their stores.
When your organization refuses to take payment card security seriously or doesn’t understand how to safeguard that sensitive information, you open the door to the very real possibility that your entire reputation will become tarnished. That can certainly have a greater effect than even the heftiest of fines.
Best Practices
As mentioned previously, we’re seeing improvements in the ways organizations have been able to transmit, process, or store their cardholder data. Being proactive about protection is the best way to ensure that your organization doesn’t suffer from a payment card compromise.
Segmentation
Knowing how to protect your organization and your customers first comes from getting an understanding of what people are doing to access your data. Often, businesses will open applications on internet browsers and type the credit card information into the application to make a payment, When organizations do this, attackers can use keylogger malware to track keystroke information and pull the card data as it’s being typed.
To prevent this, businesses could use a workstation on a dedicated network to create network boundaries dedicated to a particular function. Ensuring that the network rules are sufficient makes them easier to maintain.
New Technologies
The goal of PCI and card industry data security is to secure credit card data. Devaluing is one way to get closer to that goal.
Effectively, if you can make the data useless to attackers, the likelihood they are willing and able to use the card info maliciously decreases.
There are three main technologies that help businesses make their card data less valuable to attackers.
EMV Chips
You’re likely familiar with chip cards and chip readers. They hit the payment scene quickly and are now a major part of many transactions.
These chips make cards more difficult to replicate by creating a unique transaction code with every purchase. This is not something that a replica or counterfeit card would be able to achieve.
Unfortunately, chip cards only protect the cardholder on in-store purchases. The chip is ineffective online, so other methods typically need to be employed on top of simply having a chip reader in-store.
We’ve seen an influx of data incidents coming from e-commerce. Online attackers who have been successful in gathering the account number and security codes from cards are selling this information to people to make unauthorized purchases elsewhere.
Point-to-Point Encryption
There are new technologies that can also help secure credit card data. Many credit card devices contain point-to-point encryption (P2PE) software that changes the credit card information to an unreadable form before the transmission of cardholder data into the network. A math formula replaces the original card data with new values and is decrypted (the formula is solved to uncover the original information) when it gets to the receiver.
If an attacker were to gain access to this encrypted data, they would have to also figure out how to decrypt it before any of the information could be made useful to them.
Tokenization
If you’re going to store card information, tokenization can help protect what’s stored. Like encryption, tokenization replaces the card data with seemingly meaningless data, deterring attackers from stealing the data and blocking them from reading and using the data they do gain access to.
Each of these three simultaneously employed creates secure processing throughout the transaction cycle and devalues the information attackers may be able to retrieve.
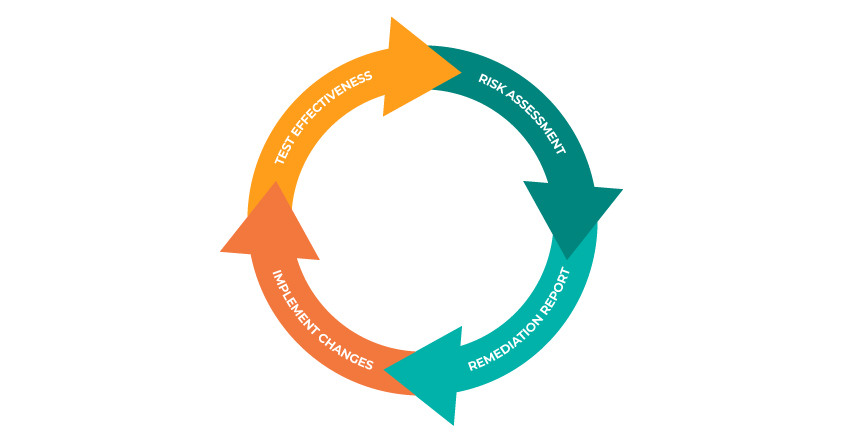
Ongoing Assessments
Security is cyclical. Ensuring you’re protecting the card data you’re entrusted with begins with assessing your efforts and uses ongoing assessments as checkpoints towards improvements and goals.
By starting with a comprehensive risk assessment, organizations get an understanding of where they are already strong and where their security leaves something to be desired. Once the business reaches an understanding of their weaknesses, they can put measures in place to bolster those areas and reassess when the measures are implemented.
In doing so, businesses can be proactive about their security, constantly being in tune with how well they’re protecting their card data—and how impactful their remediation efforts are.
Summary
We can decrease the consumer data compromised if businesses better understand and focus on security over compliance, the consequences of a card data breach, and best practices for PCI security.
Payment card security comes from recognizing that security is much more than just complying with minimum standards; it requires understanding the reputational and financial consequences of not prioritizing payment card security and putting proactive measures in place that align with that understanding.