Secure Your Business and Defense Contracts
Get backup from our team of security and compliance experts to prepare your organization for meeting CMMC standards.
CMMC
Cybersecurity Maturity Model Certification
What is the CMMC?
Prepare your security program to meet future DoD requirements
The CMMC (Cybersecurity Maturity Model Certification) outlines the information security requirements the DoD enforces on its DIB partners.
It is the defined set of requirements for any DoD contractor that receives, stores, processes, or transfers any type of CUI (Controlled Unclassified Information). The CMMC is made up of 3 different tiers according to the level of information that is used to fulfill the contract. Depending on the CMMC level that is required in the contract, third-party assessments may be required.
How can we help?
Speak with one of our CMMC registered practitioners to get started on your path to compliance.
CONTACT USHow does FRSecure approach CMMC?
It is vital for any DIB partner to know exactly where they stand on the CMMC information security requirements. Reporting false or inaccurate information in the SPRS system or while bidding can severely hinder an organization’s ability to bid on federal jobs in the future.
FRSecure uses the latest information available from the DoD and the CMMC-AB, along with several CMMC RPs (Registered Practitioners) to help its clients make sure they are ready for a CMMC assessment. We help with scoping, develop roadmaps, and walk you through each control that is required to be compliant, all while ensuring your information security program is as robust as possible in the process.
Risk Assessment
Risk Assessment
Gap Assessment
Gap Assessment
Virtual CISO
Virtual CISO
Roadmapping
Roadmapping
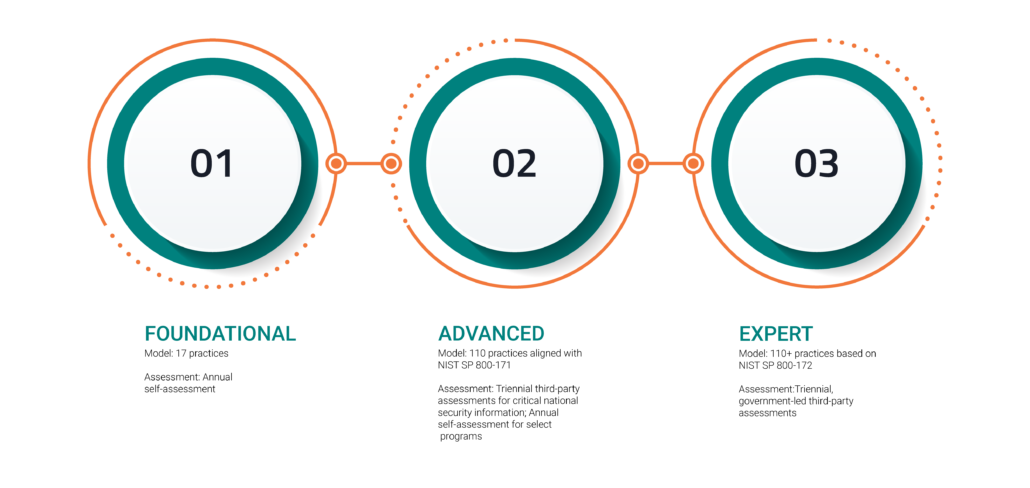
CMMC Levels
Level 1 focuses on the protection of FCI and consists of only practices that correspond to the basic safeguarding requirements specified in 48 CFR 52.204-21, commonly referred to as the FAR Clause.
Level 1 is equivalent to all of the safeguarding requirements from FAR Clause 52.204-21.
Self-assessment will be allowed at this level.
Level 2 focuses on the protection of CUI and encompasses the 110 security requirements specified in NIST SP 800-171 Rev 2.
Self Assessment may be allowed at this level as well.
Level 3 will be based on a subset of NIST SP 800-172 requirements. Details will be released at a later date.
CMMC FAQ
The CMMC was created by the US Department of Defense as a way to have more control over their vendor and contractor security.
If you’re a part of the DIB supply chain or if you’re a service provider for the DoD, this will need to be something you comply with. Every contract the DoD enters will eventually have CMMC requirements. It’s anticipated that 350,000 vendors down the supply chain of the DoD will be impacted by this.
Your CMMC requirements will depend on the type of contract you’re trying to participate in. With three levels of increasing security controls, it’s likely that the impact of the contract on the defense industry will decide which of the levels you’ll need to comply with.
The CMMC model consists of 17 domains in level one, 110 practices in level two, and 110+ in level three stemming from areas in Federal Information Processing Standards (FIPS) Publication 200, Federal Acquisition Regulation (FAR) 52.204-21., and NIST SP 800-171. CMMC also includes asset management, recovery, and situational awareness.
Specific controls are assessed based on the CMMC level that the contract requires.
The best way to ensure compliance with the CMMC model is to establish a POA&M and SSP and then determine any gaps in your existing information security program.
Based on the POA&M and SSP, an organization can establish its SPRS score and determine whether it satisfies the proposal requirements.
The FRSecure Way
Why work with FRSecure?
Expertise
FRSecure has been in business for over 10 years, and our team has more than 300 years of combined experience working in information security and boasts 30 different kinds of certifications. When it comes to growing a security program that complies with CMMC, you have the benefit of experience in your corner.
Mission
Our mission at FRSecure is to fix the broken information security industry. Not only do we help comply with the CMMC, but we also solve as many weaknesses as we can in your security environment. We are dedicated to making real, lasting, impactful changes to your security program.
Style
Our style isn’t “cookie cutter.” We recognize that each organization is different, and every security program is at a different stage of maturity. We get to know your security program intimately, use an information security risk assessment to determine what your strengths and weaknesses are, and then apply industry best practices to provide the next steps that’ll help you comply with CMMC.
Focus
Information security is all we do. We don’t do IT, sell hardware, or provide telco services. We only do security. Because of this, our team can provide unbiased recommendations that will actually make a dramatic impact to the way you do security. We work hard to be a partner—collaborating with and educating your team every step of the way.


