The United States Department of Defense (DOD) has upped its security game in a big way starting in 2020. The government agency, which provides military forces for national security, released a new certification—The Cybersecurity Maturity Model Certification (CMMC)—at the end of January 2020 that aims to decrease the impact of cybersecurity risks that threaten the defense industry.
More and more, information security and cybersecurity efforts in organizations all over the world are impacted by a growing web of connected vendors. In turn, it has become hypercritical that organizations not only understand how mature their vendors’ security programs are but also have a hand in making them better. Otherwise, they run the risk of a compromise that (on paper) was not their organization’s fault.
And that’s the basis of the CMMC cybersecurity requirements. With the CMMC, the DOD is doubling down on knowing where its vendors’ security programs stand and is using the certification as its audit framework.
If you work with the DOD as a vendor, this is on the horizon. It will change your relationship with the DOD and the way your organization needs to handle its security measures.
Here is what we know about the CMMC levels and requirements so far.
What is the Purpose of CMMC?
This is the government’s way of keeping tabs on the security of its potential defense vendors and related to Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). It provides a mechanism for the DOD to ensure their vendors and supply chain have mature enough cybersecurity practices to work with the DOD. It focuses on certifying the “maturity levels” and “capability” of each DOD vendor’s security processes, practices, and methods. It also helps set goals and priorities for them to make improvements.
The DOD will not be conducting the audits, either. A network of certified third-party assessors (C3PAOs) will be tasked with vetting the security of each of its potential vendors. Each of its 350,000 vendors will need one of these assessments. Additionally, there are Registered Provider Organizations, such as FRSecure, that employ Registered Practitioners that are certified to assist organizations in preparing for CMMC levels certification. The CMMC Accreditation Body (CMMC-AB) has also been very clear that a C3PAO cannot provide any coaching or assistance to an organization that it will be conducting the audit on. RPOs are able to provide that coaching and assist in preparation as needed.

The framework of the certification combines several known cybersecurity best practices and regulatory standards and is made up of 14 domains that align with the NIST SP 800-171 families.
- Access Control (AC)
- Awareness and Training (AT)
- Audit and Accountability (AU)
- Configuration Management (CM)
- Identification and Authentication (IA)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Personnel Security (PS)
- Physical Protection (PE)
- Risk Assessment (RA)
- Security Assessment (CA)
- System and Communications Protection (SC)
- System and Information Integrity (SI)
What are the Differences Between NIST 800-171 and CMMC?
As cybersecurity concerns grow between the DOD and its vendors and supply chain, so do the requirements the body must put on them. Until CMMC and its certification came to be, organizations working with the DOD simply self-assessed using the NIST 800-171 framework. Contractors and subcontractors will now be faced with more rigorous requirements and third-party assessments so the DOD can ensure better data safety.
Since January 2018, organizations have been required to be NIST SP 800-171 compliant if they store, transmit, or process Controlled Unclassified Information (CUI).
But, being that it’s self-assessed in many cases, compliance rates with NIST SP 800-171 are historically low.
The CMMC aims to combat the lack of adherence to cybersecurity requirements by doing two things:
- Tiering the requirements as a way to avoid applying the same standards across companies and contracts that differ greatly
- Requiring a third-party assessment of cybersecurity practices within two of the three tiers, the US Government can ensure and verify the implementation of these practices.
With the adjustment to CMMC 2.0, the CMMC and NIST frameworks are much more aligned. However, CMMC does specify additional requirements beyond the NIST SP 800-171 security requirements, such as incident reporting. At its core, CMMC is designed to provide assurance to the DoD that a contractor can adequately protect CUI.
What are the Differences Between CMMC and CMMI?
The Capability Maturity Model Integration, or CMMI framework, is designed to help organizations build and improve cybersecurity processes over time. The US Department of Defense helped develop the CMMI framework, and it was used as a precursor to CMMC.
Much like the original CMMC, CMMI puts organizations into five levels—typically through an appraisal process. These appraisals evaluate process and service development, service establishment and management, and product and service acquisition. Ultimately, it helps identify issues, mitigate risk, and gives organizations an established maturity level they can provide to clients.
It intends to identify gaps with the following:
- National Institute of Standards and Technology Cybersecurity Framework (NIST CSF, 800-171)
- ISO/IEC (27001, 27002)
- Threat Kill Cycle
- Federal Financial Institutions Examination Council (FFIEC)
- CMMC
But it’s not necessarily a certification. CMMI is a process model, guiding programs through improvements and changes. CMMC is more or less an audit standard. The key difference there is a requirement. Despite being developed in part by the DOD, CMMI is not a requirement for Department contracts.
Because of this, businesses will not have a designated level that it needs to reach to be able to take on DOD contracts. This also means the goal of CMMI is to make the most improvements possible (achieve the highest level) rather than to meet a specific level.
Basically, CMMI is a set of best practices. CMMC is a requirement built in part from those best practices.
Who Needs CMMC?
The DOD will add CMMC levels to each RFP. Any vendor that is bidding on the RFP must possess the appropriate level certification at the time the contract is awarded. This does not mean that if an RFP states CMMC Level 3 and you do not have that level that you cannot be a subcontractor for the RFP—it means you will only have access to information that corresponds with the CMMC level you are certified at.
The potential does exist that if you are providing Commercial-Off-The-Shelf (COTS) solutions, as defined by FAR 2.101, you will not be required to obtain a CMMC levels certification.
COTS include any item of supply (including construction material) that is:
- A commercial item (item that can be sold, leased, or licensed to the general public);
- Sold in substantial quantities in the commercial marketplace; and
- Offered to the government, under a contract or subcontract at any tier, without modification, in the same form in which it is sold in the commercial marketplace.
What are the 3 CMMC Levels?
There are three CMMC levels. For all CMMC levels, your organization must be able to show sufficiency based on a least two of the forms of objective evidence from:
- Interviews – a written or spoken interview with the person implementing, performing, or supporting the function or process related to the CMMC practice.
- Evidence Review (preferred method is demonstration) – this could include documentation such as policies or it could be actual procedures conducted that support the function or process related to the CMMC practice. The evidence must be produced by people that implement or perform the process.
- Testing – any testing/demonstration must pass the requirements and criteria for the function or process related to the CMMC practice. All testing/demonstrations must be observed by the Certified Assessor (CA) and the assessment team.
A reminder that the requirements for each ML are simply the minimum to achieve certification for that ML. Organizations can, and should, do more to properly secure their data than what their CMMC levels require. Most organizations will need either an ML1 or ML2 certification.
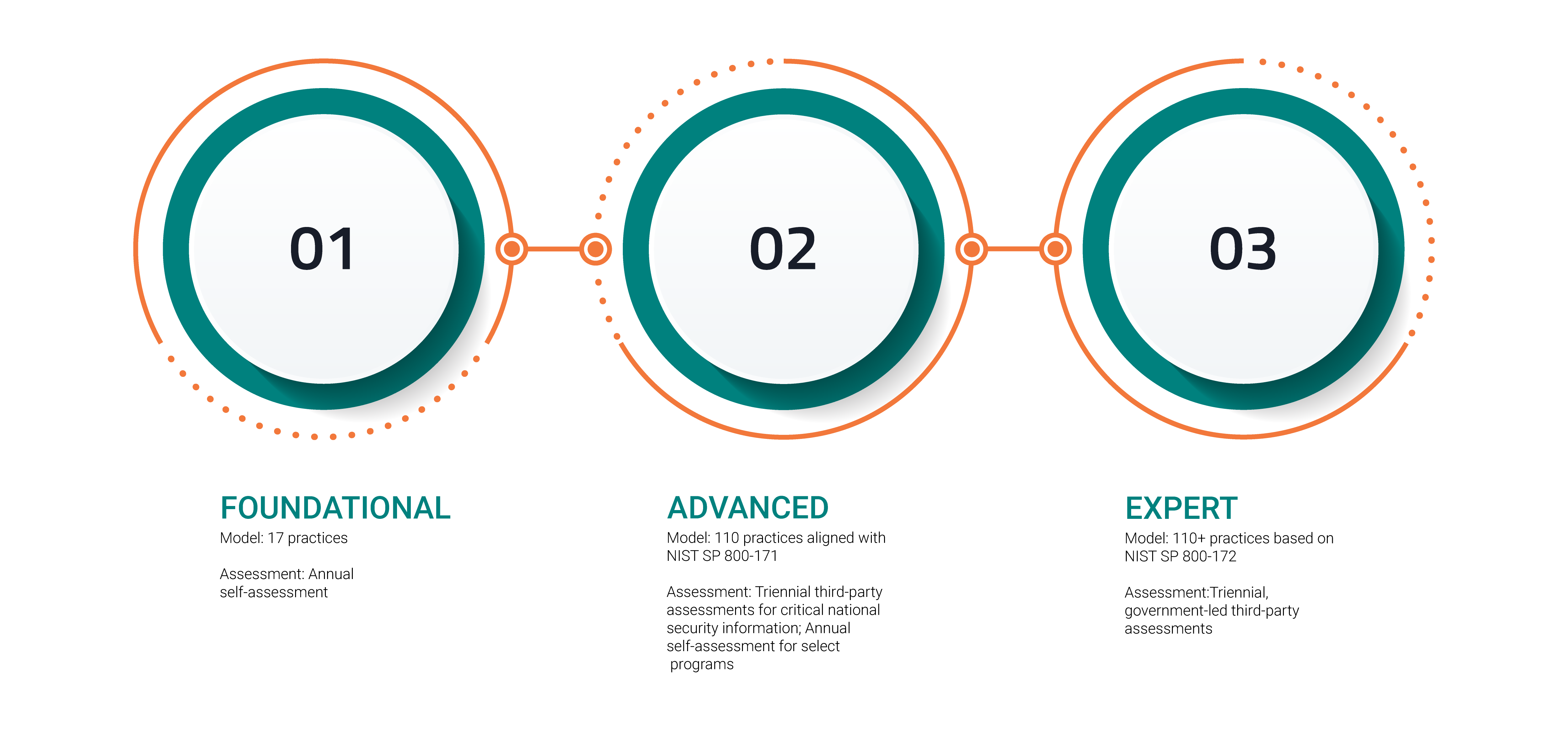
CMMC Level 1: Foundational
Level 1 focuses on the protection of FCI and consists of only practices that correspond to the basic safeguarding requirements specified in 48 CFR 52.204-21, commonly referred to as the FAR Clause.
Level 1 is equivalent to all of the safeguarding requirements from FAR Clause 52.204-21.
Self-assessment will be allowed at this level.
CMMC Level 2: Advanced
Level 2 focuses on the protection of CUI and encompasses the 110 security requirements specified in NIST SP 800-171 Rev 2.
CMMC Level 3: Expert
Level 3 will be based on a subset of NIST SP 800-172 requirements. Details will be released at a later date.
How Will My Organization be Impacted by CMMC?
Effectively, if you are a manufacturer, farmer, or any other organization working with the DOD, this needs to be on your radar. It is anticipated that 350,000 vendors down the supply chain of the DOD will be impacted by these security requirements.
While none of the current requests for proposal with the DOD contain CMMC levels requirements, the DOD is expected to include CMMC levels requirements in 15 in 2021—slowly increasing the number of contracts that contain CMMC levels requirements over the next five years. By 2026, every request for proposal the DOD initiates will have some level of CMMC requirement.
What Do I Need to Do from a Security Standpoint?
Get Ahead of It
If you want to work with the DOD moving forward, this needs to be something your organization proactively considers.
The actual CMMC levels requirement will not begin for quite some time for a lot of organizations, however, it is important to remember that good security practices are all about being prepared. So is audit prep.
More importantly, though, major changes in security programs often require changes in thinking and behavior at the organizational level. This is not something that happens overnight. To create a culture where security becomes the focus, you will need time.
While time feels like a luxury now, the sooner you begin making these changes, the easier it will be when the time for compliance comes. And remember, certification requires evidence that practices and procedures have been implemented for a “significant” period of time.
Do not think you can purchase a policy deck a month before the CA is set to arrive and pass the assessment? Not likely.
Asset Management
At the end of the day, good security practices come with doing the basics right. No fancy technology or software alone can get your program where it needs to be. A risk assessment is a great start to helping guide your practices, but it is not a silver bullet. Asset management is another important security practice that can help you prepare for the CMMC requirements long-term.
Do the basics right first.
You can’t secure what you don’t know you have, and your security measures should directly impact your most valuable assets (as well as the risk associated with them). Asset management is one of the most basic things you can do to improve your security program. It sets the stage for everything moving forward—including your risk assessment.
Start by tracking and categorizing resources within your organization. A good asset management practice gives businesses an understanding of the existence, access, location, and function of their important assets.
There are three types of assets that organizations need to keep tabs on.

Hardware
Think of the things you would put a label on. This may include computers, printers, tablets, hard drives, servers, and more.
Software
Software is an asset, and it is important to manage the purchase, licensing, implementation, maintenance, and disposal of software applications.
Data
A lot of organizations fail to realize that data is an important asset that needs the same (if not more) management as the more tangible ones. Imagine if all the data in your organization were to suddenly disappear. Would it put you out of business? Data is an incredibly powerful asset that should be managed accordingly.
Conduct a Risk Assessment
After you understand what your most important assets are, measuring the risk of compromise to those assets is the next step. The most efficient way to be proactive about your organization’s security is to perform a risk assessment, which is required to be conducted annually for CMMC Level 2 and CMMC Level 3.
Risk assessments give you a baseline of your security program—a snapshot of your current state. Understanding this baseline is important because it tells you what gaps you have and how you can mend them, particularly as you look to enter into RFPs with the DOD that might require you to level up.
Risk assessments are meant to be barometers of change. Implementing new practices and procedures into your security program helps improve your ability to avoid and mitigate risk. And, ultimately, that is what the DOD is trying to do with the CMMC, too.
So, get out in front of these new requirements by getting a risk assessment (especially one mapped to similar or the same controls that the CMMC assessment contains). You may not know what level you will need to be for the kinds of contracts you will apply for with the DOD yet. However, the more you understand the strengths and weaknesses of your own organization’s security and where the most room for improvement is, the more likely it will be that you will be prepared when the C3PAO assessment comes.
Plus, it will help you build stronger security practices and policies in the meantime, which is never a bad thing.
Conclusion
By 2026, every request for proposal the DOD puts out will have a CMMC levels requirement.
So, yes, you likely have quite a bit of time before the CMMC requirements are implemented into the contracts you will submit a bid for. But, if you can get an early understanding of what assets your organization has, and how well (or not-so-well) you secure them, it should give you time to make the adjustments that will get you on the right track to the CMMC level you need to achieve. A good asset management practice and a comprehensive, regulation-mapped risk assessment are the best ways to get that jump-start.
The easiest way to prepare for these new requirements is to be proactive about your security. Start with understanding what your most critical hardware, software, and data assets are. Then, conduct a risk assessment so you know what the likelihood of something bad happening to those assets are, and work to change and implement practices that can help minimize that likelihood.
By doing those things, you will be able to consistently work towards making noticeable improvements to your organization’s overall security practice and put yourself in a good position to level up in the CMMC framework for when the time it becomes required rolls around.
If you’d like to learn more about building a strong security program, asset management practices, risk assessments, or just improving your overall security posture in advance of CMMC requirements, reach out to us by visiting frsecure.com.







