Build Your Security Program
Whether you’re starting from scratch or looking to improve, we can help.
Who needs this solution?
When you don’t know which security efforts to prioritize
Many organizations understand they need to do something around information security and data protection, but don’t know which risks pose the biggest threat and don’t know where to begin combatting them. If you need assistance in understanding where your most impactful risks are and where you can get the most bang for your security buck, learn more about how FRSecure helps organizations like yours build security programs.
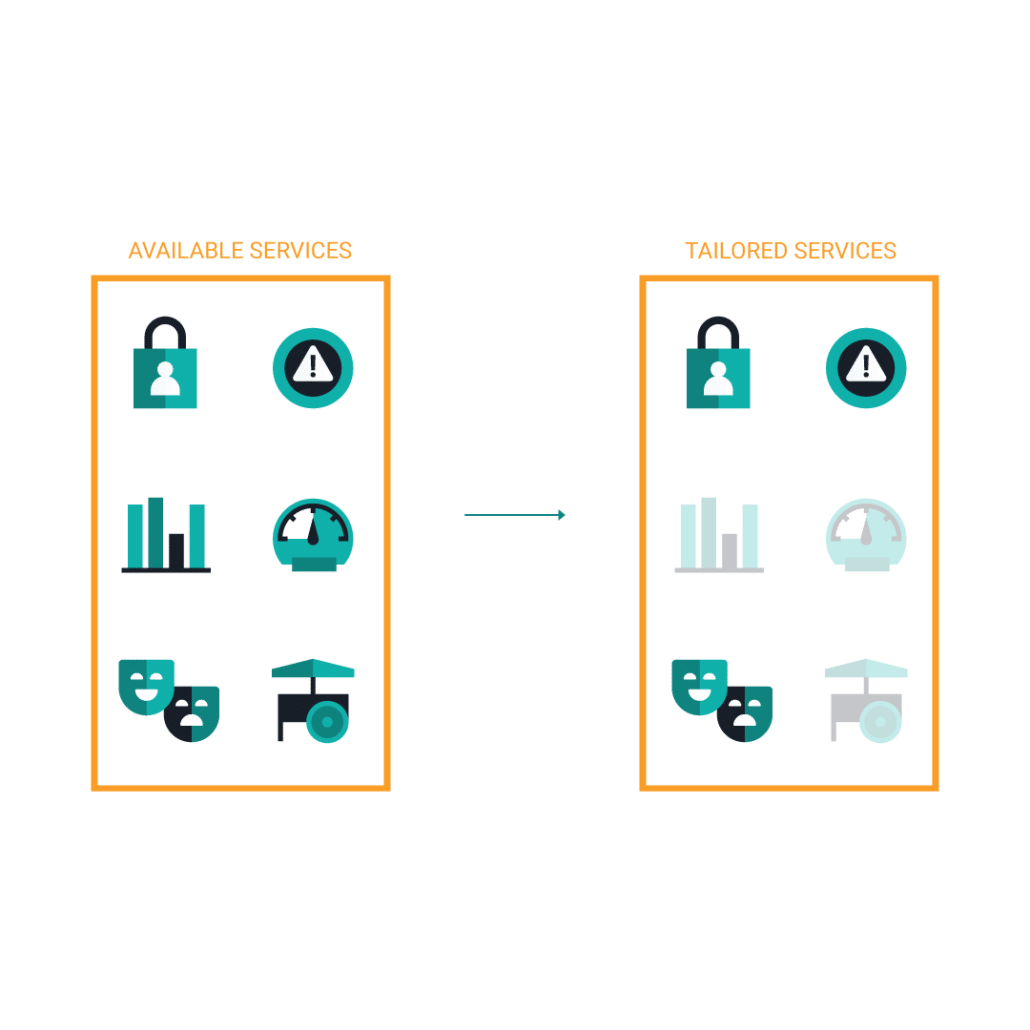
Our Approach
Only the relevant services for your business needs
While we offer many services that are relevant to building a security program they may not all be appropriate for your business needs. We’ll work with you to understand your security goals and provide the services that help you achieve them.
Services to Help Build Your Security Program
Tailored for your business, not one-size-fits-all.
Virtual CISO
Virtual CISO is a service designed to make top-tier security experts available to organizations who need security expertise and guidance. Our team of experts has decades of experience; building information security programs that work WITH business objectives and show measurable improvement to security posture.
Learn more
Incident Response
Incident response is an organized approach to rapidly responding to the aftermath of a security breach, incident, or cyberattack. The goal of incident response is to quickly identify an attack, minimize its effects, contain the damage, and identify the root cause of the incident to reduce the risk of future incidents. When security threats arise, quick incident response is critical for proper identification and containment..
Learn more
Risk Assessments
FRSecure offers a comprehensive information security risk assessment designed to discover and quantify information security risk. An industry-standard used by security practitioners around the country, our methodology helps inform effective information security programs and allows organizations to prioritize and maximize information security investments.
Learn more
Gap Assessment
Gap assessments are conducted with regulatory requirements in mind. We’ll take a look at where your security program is relative to the requirements, and then provide you with the appropriate adjustments needed for you to become compliant.
Learn more
Tabletops
Table-topping is an exercise designed to practice and find weaknesses in plans like disaster recovery, incident response, and more. Our team of experts will guide you through a simulated scenario where that plan will need to be enacted with the intent of gathering information on how to improve it—making sure the right people are doing the right things at the right time.
Learn more
Vendor Risk Management
More than half of all security breaches result from third-party vendors hired by your organization. So, it’s critical that you identify the vendors working for you and determine the level of risk they bring. Our VRM services help you to pinpoint the vendors that present the most risk to your organization—equally evaluating all third-party vendors and bringing your weakest links to the surface.
Learn more