The number of cybersecurity breaches has consistently grown.
This year, Verizon analyzed a record total of 157,525 incidents in their infamous data breach report.
This adds further credibility to warnings from many cybersecurity professionals that it’s not a matter of if your organization will be breached—but when.
With this in mind, I want to point out that HOW your organization handles their response to a breach (known as incident response) makes a huge difference.
Here are a few organizations that I’ve found that handled their breach disclosure well.
Disqus Breach Disclosure
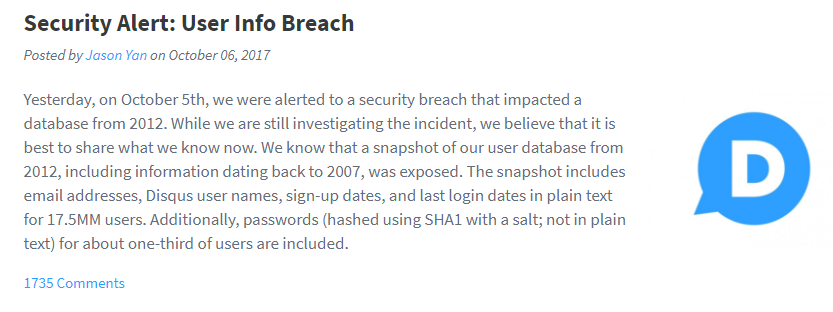
Disqus was the first organization to come on my radar for a well-handled security breach notification, per mention on the Smashing Security podcast, hosted by Graham Clueley and Carole Theriault.
Within 24 hours of discovery, Discus disclosed their breach to the public and began contacting users and forcing password resets for all affected accounts. According to Carole on Smashing Security, when the breach was first announced on their website, the announcement even held a prominent position on their home page, ensuring that frequent customers would see it and act accordingly.
Their public announcement was posted to their blog, and clearly lays out the information about the breach, including:
• Discovery of a breach, when they were alerted, by whom, and a timeline of events thereafter
• What data existed in the leaked database
• How many users were potentially impacted
• A description of the potential impact to personally identifiable information for users, and
• An outline of the steps Disqus has and is taking to protect the data moving forwards
• A link for customers to follow to gain more information about protecting themselves from identity theft
• An apology
Despite the large count of potentially impacted users, 17.5 million according to Disqus, the reaction to their public disclosure was largely positive due to their quick response to the incident, in some cases even receiving praise for it.
<blockquote class="twitter-tweet"><p lang="en" dir="ltr">Yes, <a href="https://twitter.com/disqus?ref_src=twsrc%5Etfw">@disqus</a> was fantastic: <a href="https://t.co/hZIEPXIW4s">https://t.co/hZIEPXIW4s</a></p>— Troy Hunt (@troyhunt) <a href="https://twitter.com/troyhunt/status/924802497646010368?ref_src=twsrc%5Etfw">October 30, 2017</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script>
We ♥ It Breach Disclosure
We Heart It similarly appears to have made a quick and effective response to a breach they learned about from Troy Hunt earlier this year. They posted a notice about the data security breach within two days of being alerted and, according to the notice, began investigating the leak immediately. The public notice is posted in their help center and similarly aims to share relevant information with the public, such as:
• Roughly how many user accounts were impacted
• Confirms the leak and the timeframe of the leak
• Confirms the potentially leaked information
• Addresses weaknesses of the encryption algorithm used and their approach to dealing with the leak
• Recommends that customers change their password
• Offers an apology
Additionally, We Heart It sent emails out to affected users over the weekend immediately following the notification to alert them and recommend that they change their password. Unfortunately, they did not automatically reset users’ passwords on their behalf, leaving the burden on the users themselves. Overall, however, their quick response and notification were well received.
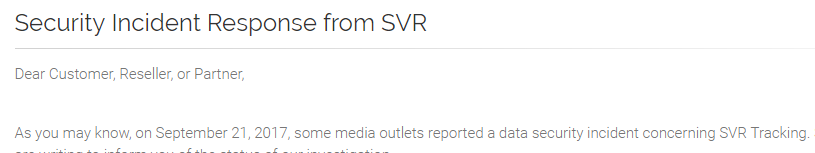
SVR Tracking Breach Disclosure
Although SVR Tracking was quick to lock down their leaked data when Kromtech Security Center notified them on September 20th, 2017, their lack of a response either publicly or to Kromtech and other media outlets soon lead to reports that the leaked passwords were encrypted with an outdated encryption algorithm, SHA-1.
As a result, SVR was compelled to respond and explain in their announcement that their encryption algorithms had been updated to the modern encryption algorithm, SHA-256.
The lack of an actual apology to customers and partners is disappointing; however, I applaud that the alert is now present on the home page of their website and I’m sure this response will undoubtedly help to restore the narrative and their customer’s good faith in the company if additional information is not extracted from them over time.
Report the News or Let the News Report on You
I think one of the clearest messages here is that when your organization becomes aware of a breach you need to act fast and be open about it; especially if you are notified by a third-party.
Having an incident response plan is invaluable at high-stress, fast-response times such as these. Clear communication channels need to be established within your organization prior to an event to provide a focused and effective response.
Breach notification requirements are gradually spreading across the US, but as I hope I’ve demonstrated here, you WANT to notify your customers quickly, effectively, and accurately. One of the big takeaways from this year’s Equifax breach should be just how BADLY they handled their public response. If you want customers to trust you with their data, you need to be open and honest with them, and you need to back it up with effective action.
Incident Response is not something you can buy a fix for; your plan needs to have a customized approach encompassing the culture of your organization. So, if you don’t yet have an Incident Response plan for your organization, reach out to us here at FRSecure. Our incident response team and security analysts are helping organizations prepare for the inevitable every day.
Helpful Resource
Lastly, I want to refer everyone to this great article by Troy Hunt on preparing for an inevitable breach.
Have any stories of organizations handling breach disclosure exceptionally well? Share them with us in the comments section, on Twitter, or LinkedIn.