Whenever there’s a large or well-publicized breach such as this one, I usually wait a week or so before writing an opinion. This is because I prefer facts (as opposed to speculation) and I prefer logic (as opposed to emotion). If you were expecting a response from me sooner regarding the Equifax breach, now you have a reason why you didn’t get one until now.
I’ve been involved in hundreds of incidents and/or breaches over the past 25 years. When I consider a breach, I understand that there’s always an emotional response and always a logical response. Emotional responses drive us to seek answers to questions like:
- Who do I blame?
- Who should I be mad at?
- How angry should I be?
- Who’s got to pay for this (punitively)?
Some of the emotional questions are helpful, some are not. It’s the human side of us that demands these answers.
Logical responses overlap with the emotional ones, but logic forces us to step back and think things through. In our incident investigation processes, FRSecure clients appreciate the logical approach, and our ability to consider emotion. Logically, we approach investigations holistically from four different perspectives; the company itself, what was in place for prevention, what was in place for detection, and how well is the response handled?
My take on the Equifax breach revolves around these four perspectives. We’ll look at each one, but first some of the latest information about the breach.
The Breach
What do we know, or what do we think we know?
- An estimated 143 million American consumers are at risk
- 57% of US adult population; est. 250 million adults
- Equifax maintains data on more than 820 million customers people worldwide
- Breach lasted from mid-May through July (first detected on July 29th)
- Days after the breach was detected, three senior managers sold nearly $1.8 million of stock @ $146+/share
- Compromised data includes:
- Names
- Social Security numbers
- Birth dates
- Addresses
- Driver’s license numbers (in some instances).
- Credit card numbers for approximately 209,000 people were stolen
- Dispute documents with personal identifying information for approximately 182,000 people were stolen.
- Breach was blamed on a “US website application vulnerability”
- Suspected to be a bug in Apache Struts (CVE-2017-9805), by some reports
- “At this point in time it is not clear which Struts vulnerability would have been utilized, if any,” said René Gielen, VP for Apache Struts.
- A majority of the Fortune 100 & Fortune 500 companies are suspected to use Apache Struts.
- According to the Apache Struts website, “Apache Struts is a free, open-source, MVC framework for creating elegant, modern Java web applications. It favors convention over configuration, is extensible using a plugin architecture, and ships with plugins to support REST, AJAX, and JSON.
- The Equifax Data Breach: What to Do (FTC Consumer Website):
- Visit Equifax’s website, https://www.equifaxsecurity2017.com
- Find out if your information was exposed
- Enroll in free credit monitoring
- You also can access frequently asked questions at the site
- Check your credit reports from Equifax, Experian, and TransUnion — for free — by visiting annualcreditreport.com or creditkarma.com
- Consider placing a credit freeze on your files.
- Monitor your existing credit card and bank accounts closely
- If you decide against a credit freeze, consider placing a fraud alert on your files.
- File your taxes early
- Visit Equifax’s website, https://www.equifaxsecurity2017.com
- At least two class-action lawsuits have been filed; more than 20 have been reported. One suit in Portland, Oregon is seeking more than $70 billion in damages.
- Attorney Generals in at least five states have announced formal breach investigations.
- Several Congressional Committees are launching (or have already launched) hearings; with bi-partisan support
- Brian Krebs has put together a great (as always) FAQ blog post – https://krebsonsecurity.com/2017/09/the-equifax-breach-what-you-should-know/
The Company – Equifax
Some facts about Equifax from Wikipedia:
Equifax Inc. is a consumer credit reporting agency. Equifax collects and aggregates information on over 800 million individual consumers and more than 88 million businesses worldwide. Founded in 1899 and based in Atlanta, Georgia, it is the oldest of the three largest American credit agencies along with Experian and TransUnion. Equifax has US$ 3.1 billion in annual revenue and 9,000+ employees in 14 countries. It is listed on the NYSE as EFX.
I don’t take issue with Equifax as a business per se, but I do have issues with seemingly significant portions of the Equifax business model. Some of the troubling issues about Equifax’s business model are:
- Permission to gather data – I don’t recall ever giving permission to Equifax for gathering information about me.
- Personal data use – I am not clear about all the ways in which Equifax uses the information about me.
- Data ownership – I am not clear about who the owner of the data is, which leads to many other questions, some of which are:
- If it’s me, shouldn’t I have more say about how my data is used?
- If it’s me, shouldn’t I have more say about how my data is protected?
- If it’s me, shouldn’t I be able to choose not to do business with Equifax?*
- If it’s Equifax, then why do I personally pay the price for their mishap(s)?
- If it’s Equifax, then why do I have to pay for them to make sure the data is accurate (e.g. credit monitoring)?
- If it’s Equifax, then why do I pay the price when the data isn’t accurate (e.g. credit issues)?
*In the case of many other breaches, as a consumer, I have the discretion to stop doing business with the at fault organization. For instance, when the Target breach happened in 2013, I could choose to stop doing business with Target; or at least change my relationship with Target (pay cash instead). In the case of Equifax, I feel powerless. Can I stop my relationship with them?
As you can see, I have some issues with Equifax in general.
Prevention
No matter what, I cannot prevent all bad things from happening. You cannot prevent all breaches.
Two primary questions about prevention:
- What do we know about how Equifax tried to prevent the breach?
- Were Equifax’s preventative measures adequate?
There is plenty of speculation about both points; however, the fact of the matter is that no matter what you do, you will never be able to prevent all bad things from happening (breaches).
I won’t speculate much about the preventative measures that Equifax had in place at the time of the breach. To do so would probably be counterproductive. We do know that the breach was blamed on a “US website application vulnerability”. This leads us to speculate on lots of things:
- Was it a Struts vulnerability and if so which one?
- Was it a vulnerability in some other part of the application?
- Should Equifax have known about the vulnerability?
- Was there a missing patch?
- Is Equifax’s vulnerability management program deficient?
We could speculate all day. Again, keep in mind that no matter what we do, we will never be able to prevent all bad things from happening.
Some people have called Equifax’s Chief Information Security Officer (CISO) into question. The Equifax CISO is/was Susan Mauldin. According to reports, she has been with Equifax since 2013 and was previously the CSO at First Data Corporation and before that was with SunTrust Banks’ Group. On the surface, Susan Mauldin is well-qualified to lead information security at Equifax.
I don’t know much more about her, so I’m cautious in speculating about her competency. This doesn’t stop other people however. She’s under a lot of scrutiny, and people are even calling into question her college degree choice!
A college degree will never make you a good information security professional and most experts in our field don’t have information security degrees. I feel a little bad for Susan Mauldin.
Anyway, I don’t know enough about Equifax’s preventative measures or prevention techniques to offer a definitive opinion. 100% prevention should never be the focus anyway, managing risk is.
Detection
Where I can’t prevent bad things from happening, I should be able to detect them.
Again, we can only speculate about all the detective measures that Equifax had in place. We do know that the breach started in mid-May and it was first detected on July 29th. I haven’t heard specifically about how the organization detected the breach, so again we are left to speculate.
If this was a sophisticated attack (which it might well be), then 2 – 2-1/2 months to detect might be reasonable. According to Gartner, the average time to detect a breach is 99 days. The average time vs. what the time should be is debatable. We do know that the time to detect in this case seems reasonable when compared with the rest of the world.
Response
When I detect bad things, I need to have an effective response.
Perception is reality. This is the part of the breach that we all have the most visibility into, at least as it relates to our perception. The general perception of the response is summed up in one word; terrible. You could also apply words like inept, horrendous, abysmal, etc. It was/and has been bad.
The poor response is summarized in the following sections.
Insiders Should Not Trade Stocks
I don’t get this one at all. In a breach that affects a public company, General Counsel should be involved very early on. One of the critical instructions given by General Counsel to executive management and/or other insiders is “do not buy or sell any securities related to our organization until further notice”. This should be a mandatory part of their response.
The facts:
- Equifax detected the response on July 29th.
- Days later, three senior managers sold nearly $1.8 million of stock @ $146+/share
- According to Ines Gutzmer, a spokeswoman for Equifax, they “sold a small percentage” of their stock
- John Gamble, Chief Financial Officer – sold 13% of his holdings for $946,374
- Joseph Loughran, President of U.S. Information Solutions – 9%/$584,099
- Rodolfo Ploder, President of Workforce Solutions – 4%/$250,458
- Also, according to Ines Gutzmer, they “had no knowledge that an intrusion had occurred at the time”
- On September 7th (the day of the breach announcement) the Equifax share price was $142.72. At the time of this writing, the share price is $104.88.
For the purposes of public relations and reputation, it doesn’t matter if these senior managers knew about the breach or not. Whether these senior managers are guilty of insider trading doesn’t matter to the public’s perception.
Bad move.
The URL – equifaxsecurity2017.com
The site was launched shortly after the announcement of the breach, and it was setup to give consumers information about the incident. Seemed like a pretty good choice for a website, at least on the surface.
Equifax failed miserably on considering the public’s perception.
Play this out:
- You get an urgent email from Equifax
- The email tells you that you may be a victim of a breach.
- Click this link to learn more.
- You click the link and it looks legitimate, but the sites URL is one that you don’t recognize.
- “equifaxsecurity2017.com” looks sort of phishy.
- On this phishy-looking website, I am directed to
- Click a red “CHECK POTENTIAL IMPACT” button
- Enter my last name
- Enter the last six digits of my SSN
At what point does it register that this is a probable phishing attempt? Haven’t we been beating it into our users to not do these things?!
To make matters worse, there were numerous anti-phishing/anti-fraud technologies that were blocking access to this site as a malicious site. Do you think we should test the URL and process before going public with it?
We can only speculate about what Equifax did to test this site beforehand, but it doesn’t really matter. Public perception is already set, and Equifax screwed up (again).
Another bad move.
Be Careful Offering Your Own Services After a Breach
Equifax is offering free credit monitoring to all consumers affected by the breach. Consumers are offered free enrollment in their TrustedID Premier product. Offering credit monitoring and identity theft protection after a breach is standard fare, and is usually a good idea. The problem again is perception.
The perception in this case:
- Let me get this straight, you just lost my information.
- You failed in protecting my information.
- In return for your failure to protect my information, you’re going to offer me something to protect my information.
- The thing that you’re offering me to protect my information is your thing.
- After a year of using this new thing, you’re going to make me pay for this new thing.
- Why didn’t I have this second thing in the first place, and why can I trust you with this second thing if you failed at the first thing?
Probably a bad move, especially given the rest of the response.
License Agreement
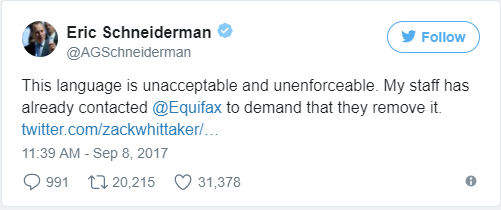
For the majority, perception early on is that Equifax can’t be trusted. This is founded in the fact that they just lost a bunch of really sensitive information about a bunch of people. To compound the lack of trust, Equifax missed the fact (or it was intentional) that their “Terms of Use” on the new equifaxsecurity2017.com website states in bold uppercase letters:
“AGREEMENT TO RESOLVE ALL DISPUTES BY BINDING INDIVIDUAL ARBITRATION. PLEASE READ THIS ENTIRE SECTION CAREFULLY BECAUSE IT AFFECTS YOUR LEGAL RIGHTS BY REQUIRING ARBITRATION OF DISPUTES (EXCEPT AS SET FORTH BELOW) AND A WAIVER OF THE ABILITY TO BRING OR PARTICIPATE IN A CLASS ACTION, CLASS ARBITRATION, OR OTHER REPRESENTATIVE ACTION. ARBITRATION PROVIDES A QUICK AND COST EFFECTIVE MECHANISM FOR RESOLVING DISPUTES, BUT YOU SHOULD BE AWARE THAT IT ALSO LIMITS YOUR RIGHTS TO DISCOVERY AND APPEAL.”
What’s this “waiver of the ability to bring or participate in a class action, class arbitration, or other representative action” stuff?! Are you saying that a person is giving up their rights to sue or participate in a lawsuit? This didn’t sit well with many people, including the New York Attorney General Eric Schneiderman who tweeted the following to his Twitter followers.
Enforceable or not, the perception is terrible (again).
Another bad move.
Summary
In closing, I can’t say much (authoritatively) about Equifax’s preventative or detective measures related to this breach. The details just aren’t available or aren’t credible (yet).
As far as Equifax’s response, it would be hard for Equifax to have messed up any worse than it did, at least as it relates to public perception. Like most breaches, we’ll look for lessons that we can all learn.
In my opinion, Equifax’s (and the other two credit bureau’s – TransUnion and Experian) business model is not at all good for security (or consumers). This is a topic that requires more elaboration for another article and another day.








I don’t think the problem is protecting private information. Nearly everyone’s “private” information is already out of the bag. We need to stop defining SSNs and birthdays as passwords, rather than identifiers. Debit and credit cards are easy to reissue with new numbers, but we can’t get new SSNs. It feels like we won’t change until everyone is certain their private information is no longer private. It won’t take long at this rate.
Thanks for the comment Derrick! I couldn’t agree more. This is likely the topic for my next article/post.