With the popularity of shopping online and digital payment methods continuing to grow and shift, online transactions have quickly become the most common type of payment worldwide. In fact, ACI predicts that by 2024, over 80% of all transactions will be electronic.
New technology is constantly being introduced, and more consumers adopt mobile wallets and pay bills online with debit cards, credit lines, or electronic transfers.
Unfortunately, financial scams and payment fraud have grown alongside these new and oh-so-convenient payment methods, becoming rampant worldwide.
What is payment fraud, and how can we protect ourselves as digitally connected consumers?
What is Payment Fraud?
Payment fraud occurs when someone illicitly obtains your payment details and uses them to make an unauthorized purchase on your account. There’s a good chance you’re among the 127 million Americans who have been a victim at one point or another, so you may already be familiar with the headache of reporting an unauthorized charge on your account.
It’s what happens after one of these charges is reported where businesses today are concerned.
How Bad Is It?
Once a dispute has been filed, the merchant must then settle the charge and pay penalties such as chargeback and investigative fees.
If worse comes to worst, and your business fails to implement security measures to prevent false charges from clearing, your merchant provider can even deem your organization too risky to do business with and shut down your account permanently.
How Does Payment Fraud Occur in the First Place?
Across all businesses, business email compromise has become both the most common and most financially detrimental vehicle for payment fraud.
Business Email Compromise (BEC) scams have been reported in all 50 states and 177 countries, with over 140 countries receiving fraudulent transfers. There were 241,206 BEC incidents reported to the FBI Internet Crime Complaint Center (IC3) between June 2016 and December 2021, resulting in $43,312,749,946 in losses.
Yes, you read that last part right: forty-three TRILLION dollars in losses from June 2016 to December 2021.
Some more stats to chew on:
Banks located in Thailand and Hong Kong were the primary international destinations for fraudulent funds.
- The IC3 has received an increased number of BEC complaints involving the use of cryptocurrency.
- Most business-related financial scams and/or fraud are not reported.
- In 2021, IC3 reported BEC attacks as the biggest contributor to cybercrime losses, with victims losing $2.4 billion from 19,954 complaints.
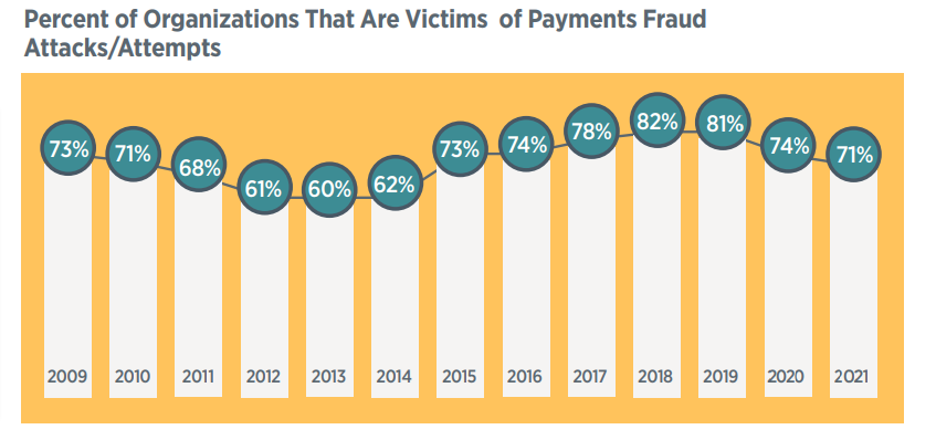
- 71% of organizations have been victims of payment fraud attacks in 2021.
- 63% of financial professionals reported that payment fraud in 2021 was unchanged from that in 2020.
- 29% indicate there had been an increase.
- Just 8% reported a decline.
The Bright Side
There is a bit of a silver lining in that financial professionals reporting an increase in payment fraud has begun to steadily decline since its peak in 2018—from 34% in 2019 to 30% in 2020 and to 29% in 2021.
While we certainly hope to see this downward trend continue, fraud remains a widespread issue, and there’s no telling if or when we could see another dramatic spike in incidents as we did in 2015.
Source: 2022 Association for Financial Professionals (AFP) Payments Fraud and Control Survey
How to Prevent Payment Fraud
Now that we’ve broken down what payment fraud is and established just how commonplace the threat has become, let’s discuss how you can protect your organization and yourself from fraud.
1. Protect Your Organization Against BEC
As we mentioned, Business Email Compromise (BEC) attacks are one of the most common ways for fraudsters to harvest payment credentials. In these attacks, the threat actor uses a combination of phishing techniques to fool the email recipient. The goal is to get the recipient to punch their payment or account details into a lookalike site where they are stored for later use by the attacker.
We have a separate article all about phishing attacks and how to prevent them, so we’ll spare you the details for now, but consider the following tactics to protect you and your team from phishing attempts going forward:
- Train your team to recognize phishing attempts.
- Use MFA on everything.
- Add an ‘external email’ notification to all messages originating from outside the organization.
- Configure Sender Policy Framework (SPF) records.
2. Use a Dedicated Computer for Banking
If your business isn’t already using a separate computer for financial purposes, now would be a great time to start. This machine should be used for no purpose other than banking. That means no checking email, no internet browsing, no video calls… you get the picture.
Ask your IT department to restrict the banking computer network connections to only those systems that are required for operation and be sure that the machine in question is hardened. This would include disabling unnecessary services, restricting privileged access, changing the password regularly, and so on. As a further precaution, you might also consider using a non-Windows system as the banking computer.
3. Be Wary of Communications You Didn’t Initiate
To some, this may seem obvious, but it’s important to refresh ourselves on the basics—especially as phishing and vishing attempts become more and more convincing.
The best practice to implement is simply refusing to give any information to anyone contacting you unprompted. Sensitive information should only be disclosed on calls that you made using known phone numbers.
If you receive a request via email that you believe to be legitimate, take the extra precaution of verifying the message by reaching out to the sender directly. Placing a call to the sender may seem paranoid, but you’re always better safe than sorry.
Another way to put your mind at ease is to log into websites and apps directly instead of following links provided in an email. Navigate directly to the login page and input your credentials there. This way you’ll avoid falling for a lookalike URL or fake login page.
Once you’re in, check and see if you have the same notification within the site or application. If the notification you received via email isn’t reflected there, you can be pretty sure the message was malicious.
4. Employ Dual Control
Dual control is a common practice in banking, but it’s one that is not always implemented by other kinds of organizations. If you’re not aware, a dual control practice is one where transactions require two different people to complete them.
You might have one employee who can initiate a transfer, and another who can approve it, but neither person should be able to handle both steps. Without it, you create a single failure point in the process which can cause a higher rate of fraudulent transactions to slip through.
- Consider setting up dual control on all financial transactions, or even on transactions that exceed a certain amount.
- Consider dual control on all changes to payment accounts.
- Consider dual control on all payment account setups.
- Consider where other sensitive (or critical) processes may benefit from the added security of dual control.
5. Use Multifactor Authentication (MFA)
At this point, MFA should be used wherever possible. Any and all accounts containing even a whiff of sensitive information should have some form of strong two-factor authentication required to gain entry.
Skipping this step is a bit like laying down a welcome mat for would-be attackers, and once an account is compromised, the possibility for lateral movement within your network and other accounts is greatly increased.
Consider performing an audit within your organization to determine which accounts already have MFA set up, and be sure to enforce MFA on all accounts that do not yet have it applied. Ensure that it’s woven into the fabric of your organization.
Know that to a non-security person, MFA can be inconvenient and cumbersome. For this reason, it’s crucial to implement training that educates everyone on the importance of going through these extra steps. If your staff understands how important these measures can be to the security of the people your business supports, they’re far more likely to take personal responsibility for securing access to their own accounts.
6. Monitor and Balance Financial Accounts Daily
Daily monitoring will not stop payment fraud. It is not a foolproof method of identifying all unauthorized activity. However, it can help identify key signs and patterns, and the practice will greatly improve the number of fraudulent payments caught before it’s too late.
If regular payments are made to certain vendors or customers, take those trends in payment history over long periods of time to help identify indicators to flag suspicious payments.
Additionally, be sure to keep these practices up to date. The signs you’ve been monitoring for months or years may not be as reliable as they were when they were designated originally.
How to Detect Fraud in Online Purchases
If you’re not sure what to look out for, let’s go over some common indicators of payment fraud for businesses accepting online payments.
- A customer places an extremely large order or otherwise diverges significantly from typical sales trends.
- A customer places several small orders back-to-back, or a customer orders the same thing multiple times.
- Mismatched shipping and billing addresses.
- Shipping information varies using the same payment method.
- There are a lot of reasons these might not match but exercise caution if a customer who ordered last month as Lisa from Los Angeles, is using their saved payment method to place an order as Mike in Montreal.
- Clearly fake contact information. Made-up email addresses like can be an indicator that a fraudster wants to avoid giving out any real information.
- Messages from the customer that seem scripted or are written poorly. Look out for a large number of grammar or spelling mistakes.
- Another indicator is correspondence that sounds scripted or is worded unusually.
- A request to split a charge over multiple payment methods.
7. Consider Employee Background Checks
A background check should be conducted on all personnel, but these checks are especially important for personnel working with financial systems.
Background checks should be conducted at the time of hire and periodically thereafter. Be sure that your staff understands that these will be a mandatory part of their role before onboarding. As with all company policies, ensure that your team understands why the practice has been implemented, and what it aims to solve.
BONUS TIP: Report Immediately!
All unusual activity should be reported to information security personnel immediately upon witnessing it in case it turns out to be an indication of something more serious.
Nothing is too small or insignificant to report.
If you have fallen for a phishing attack or suspect that you may be a victim of an attack, report the event to your security personnel immediately.
Be sure to communicate to your staff that the most important thing is to address any security concerns as soon as possible. Encourage this, even. Your team should not fail to disclose any incidents due to fear of repercussions or disciplinary action.
Closing Thoughts
As the world favors online payments more and more each year, payment fraud prevention has become a critical issue for nearly every business. And with business email compromise and other forms of phishing and vishing becoming more advanced, payment safeguards are no longer an option.
For the security of your customers and the protection of your business, implementing these best practices around payment fraud identification and protection is pivotal!
Securing all the moving parts of any business is no easy feat, so if you find yourself in need of assistance with payment fraud protection, or any other element of your security program, don’t hesitate to get in touch with us here at FRSecure.