It’s Not If, But When
When it comes to information security incidents, it’s not a matter of if, but when.
It’s impossible to protect yourself from every single incident and attack vector that can occur, so it’s important to put a focus on risk management rather than risk elimination. When risks occur, you’ll want the proper policies and procedures in place to ensure the effects of the incident are diluted.
Security Incident Classification: The Basics of Managing Incidents
When risk happens, the initial reaction is often to call for assistance from an information security expert immediately. Before doing so, however, there are steps we recommend the organization takes on its own.
Much like a tech support help desk, it’s difficult for information security experts to assist with the issue without initial troubleshooting measures already in place. Understanding the basics of incident management is the simplest and most critical way to improve your response to risks.
Incidents vs. Events
Understanding the basics of incident management begins with understanding what an incident is.
Events happen constantly throughout each day, but very few of them should be considered incidents. We define information security incidents as a suspected, attempted, successful or imminent threat of unauthorized access, use, disclosure, breach, modification, or destruction of information; interference with information technology operations and computer networks; or significant violation of policy.
Before responding to an incident, make sure that it is something that needs a response.
Security Incident Classification
Not all events are incidents, and not all incidents are the same. There are numerous variations of incidents. Once an incident has been identified, the next step is to investigate and classify the incident in question.
Your organization can handle incidents however they see fit, but we’ve developed a methodology for classifying information security incidents that can be used as a starting point that you can tweak for your organization. We rate each incident based on its type, criticality, and sensitivity.
Type is broken out into three separate classifications and includes both the type of breach and the number of people it affected. We use a scale from one to three with one being the most severe. A category one incident type would typically involve system access or data loss affecting five or more people or user accounts.
Criticality reflects the systems that the incident has affected. Again, we give this a number on a scale of one to three with one being the most severe. A one in criticality is a confirmed incident that affects critical systems.
Sensitivity involves the information collected or impacted. This category also gets a rating from one to three. The most critical information that an incident can impact is extremely sensitive and confidential information, such as patient records at a hospital.
It’s imperative that as your organization works through categorizing the incident, you document as much as you can and as early as you can. This will ensure everyone remembers facts and can clearly explain events as necessary.
Determine the Severity
Once classified, a response to the incident needs to take place.
Take the time to understand what your previous categorizations mean to your organization. How impactful is the incident to your organization, your partners, your customers, or civilians?
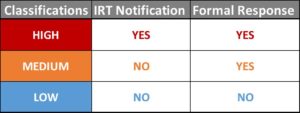
Measuring the impact or severity of the incident sets the framework for communicating a given incident: who to communicate the incident to, and how rapid their response must be. Manage expectations, responses, and ownership of incidents within your organization by classifying the incident as high, medium or low risk.
Control Communication
Once the security incident classification, impact, and severity have been determined, how will it be communicated?
Is it something that can be kept internal and handled over time? Should it be escalated up to your internal Incident Response Team (IRT) and shared immediately? Now, do we call for an external information security expert to help resolve the issue?
The answers to these questions will all be determined by how your organization feels it’s appropriate to handle each of the classifications of incidents.
External communication is an added element and part of the communication process that an organization must develop when managing risk. As consumers and civilians, we typically don’t see what goes on behind the scenes of an incident. We often only see what is communicated through various news outlets. You can learn a lot about ways you think an organization should handle its external communication by studying and familiarizing yourself with the incident responses of high-profile organizations like Target, Chipotle, Equifax, Uber, etc.
When risks occur, you’ll want the proper policies and procedures in place to ensure the effects of the incident are minimized. Use these four basic steps of incident response and management as a framework for ensuring your organization is prepared to handle incidents that occur. Remember, not a matter of if, but when.
If you have any questions about how you can help improve your organization’s incident response, please contact us or check out what FRSecure can do for you.