I am addicted to fishing.
Saturdays come, and I am up at 4:30 am heading out to get on the water with my buddy. We make it an intensive effort, and if we could get paid for it, we would take that job in a heartbeat—all the cool gear, being paid well, wearing cool clothes, and driving a new truck and boat would be the coolest things ever. We aren’t paid for our efforts, but that doesn’t stop us from treating it like we do.
The whole way there we chat about the upcoming day. We share what we have learned about the water temp, the barometric pressure, the clarity of the water, the wind, and many other things. I spend hours studying tactics, learning about new lures, tackle, technique, and studying how my intended targets think and react.

A Different Kind of Fishing
There is another activity that takes a similar approach but has much more dire consequences—phishing. Phishing is an email-based cyber-attack that can expose networks, lead to ransom attacks, and become a giant pain in the dorsal fin.
Cyber attackers who phish use a seemingly innocuous email to get your employees to click on a link that looks like it comes from a reputable entity. This is the
The phisher’s communication looks simple and innocent. It hides mayhem behind an email from the HR department, or the boss, or a vendor that you do business with. It might ask you for sensitive information, to confirm your account, to log in somewhere, etc.
In a rush to complete whatever task was asked of you by the higher-ups, you’re quick to comply. That’s just what the attacker is hoping for. The email may contain a link or an executable file that can take over your network, install ransomware, or begin copying and exporting sensitive data. Soon after, your company is on the hook.
Phishing happens every day and the attackers behind them are becoming more and more sophisticated. The days of the poorly worded Nigerian prince email are waning, and now phishing attackers are making it difficult to quickly distinguish between a valid email request or one that will allow them to gain access to your network.
Urgency is the critical breaking point.
When people are in a hurry, are trying to make sure that they have a high level of performance, and are trying to please everyone, they stop thinking critically.
Phishing scams can run the gamut from a broadly cast net sent to your entire company with the hopes that someone won’t exercise wise judgment and just clicks on something, to the very directed “spear phishing” and “whaling,” where specific individuals are targeted.
Phishing
You get an email from your boss, Ellen Simonsen asking you to evaluate a new app she wants your department touse. In an effort to be timely and helpful employee, you don’t notice her name was spelled Ellen Simonson on the email.
You follow the link.
The link installs a piece of malware onto your computer and then begins working its way into the corporate network. The result could be that the installed software is now soaking up proprietary data or is about to launch a piece of ransomware that locks everything up until the ransom is paid.
People rarely notice subtle differences when they are in a rush—and attackers feed on this.
Spear Phishing
A senior vice president of your company, we’ll call him Steve, is active on social media and is a well-known classic car nut. There are pictures of him at many events and car rallies with beautiful classic cars and cars he’s purchased to restore. This one piece of information can be a great vector of attack.
Because Steve is likely to open an email about classic cars, that is what he is sent—an email inviting him to enter one of his sweet cars in a well-known car show that is coming up in a few months. The link to register looks like it should go to the actual car show. But it doesn’t. Instead, it unleashes hell into the company network and takes the system hostage.
Tantalized by something that he was known to be interested in, Steve was an easy target. And with Steve’s stake in the company, he likely has access to important documents, financial information, sensitive employee data, and administrative-level accounts that an attacker could certainly use to their advantage.
The attackers chose him specifically, researched and played to his weaknesses, and compromised him accordingly.
How to Spot a Phishing Attempt
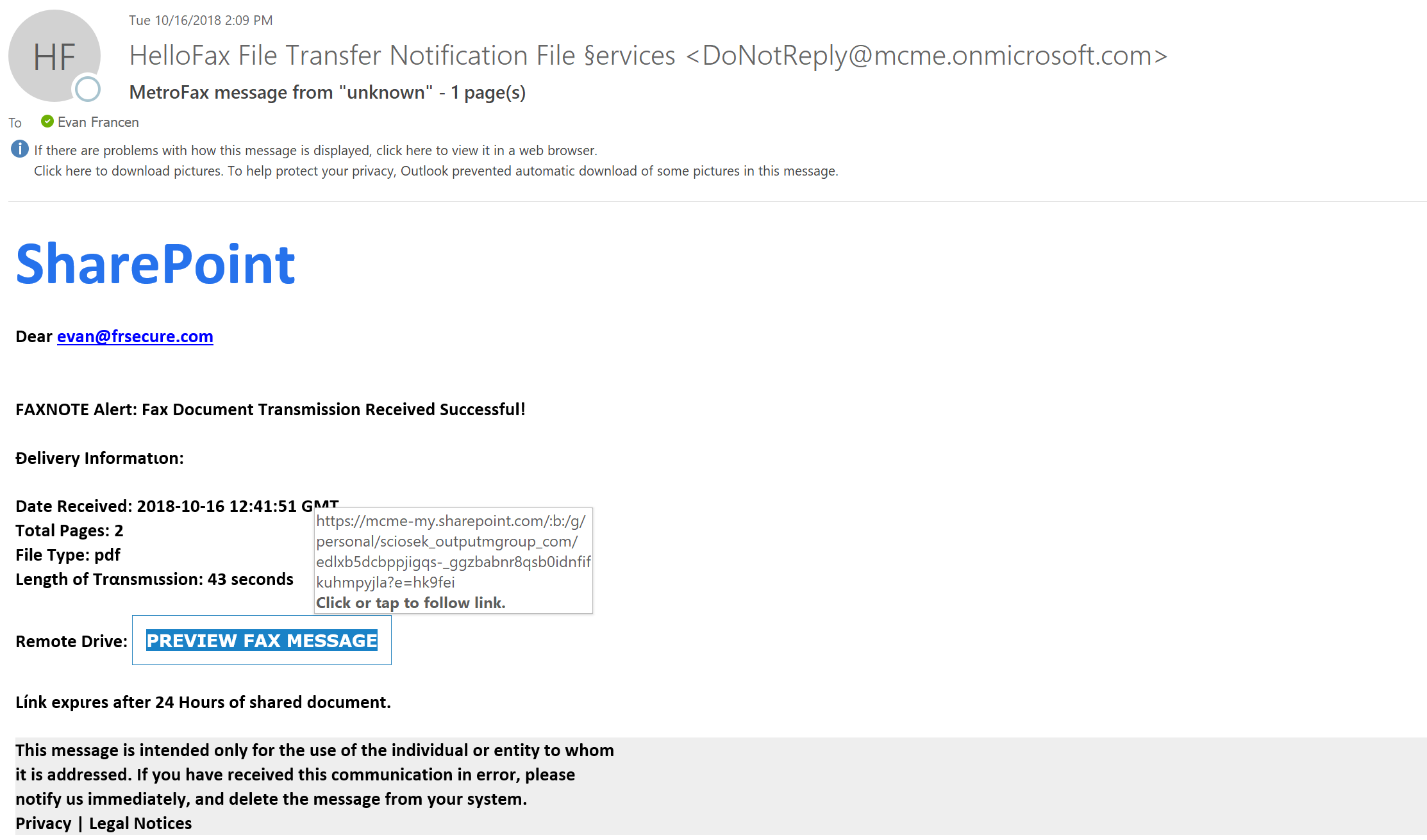
Examples like these are not farfetched at all. Every day, phishing campaigns like these are launched across the globe. They can be challenging to detect, especially in a rushed state. Thankfully, taking a few steps with your emails can go a long way. Here are some ways you can avoid falling victim to one of these attacks and compromising you and your company’s sensitive data.
Slow Down and Be Skeptical
Email attacks are often predicated on you being in a hurry and being a trusting individual. Stop that! Take your time when reading emails that ask you to click on anything.
Check the Credentials
Hovering your mouse over the email address, or expand the sender line on the email. If the email is not in the same configuration as your own email, it is not from your company. Delete.
Hover Over That Link
Take your mouse, hover over the link, and see if it goes to the right domain or if it is going so some long drawn out URL that takes you to some malicious site. The organization’s name should be in the domain. If there’s too much more than that, you should be skeptical.
Don’t Fill Out Anything Asking for Your Password
This is probably the most important advice I can give you about phishing.
PayPal, Visa, your bank, an airline, or anyone else will not be sending you an email asking you to confirm your password. They will not send you a link asking you to re-enter your username and password. They just won’t.
If you think that there is an action-item for you in that email, go directly to the sender’s legitimate site instead of taking action from the email link. If there is something you need to do, you can ensure you’ll be putting your personal details into the correct site.
Assume Every Email is Infected
Your company is getting probed every day via email and other vectors of attack. Even with logging, monitoring, antivirus, and other prevention programs in place, stuff can slip through.
With email, you are the last line of defense. If you understand that these risks are out there and go through the proper precautions before acting, you can make sure your company’s data stays safe.
While people continue to be the greatest weaknesses in security at an organizational level, they can also be a great strength. With proper training and making simple tips like the ones above well-known, it’s much easier to curb the risk from phishing attempts and other similar attacks.
If you’d like to see how your employees would handle a real phishing







