Part 1
In a previous article on Information Security and Compliance Explained I presented a good workable definition for information security. In The Top 10 Things Every CEO Needs to Do I demonstrated that all CEOs have a role to fulfill, and that there are specific actions required of CEOs.
In this article within the CEO Information Security Training Series, I’ll cover how to start building a solid information security program.
A solid information security program will lay the foundation that will ensure that your business information and the information belonging to your customers will be adequately protected.
I will also present an example and contrast two organizations: one organization that has chosen to start and manage security program development the right (and maybe the only) way, and another that is still struggling to get it right.
I have said this before, but I’ll remind you again—CEOs don’t need to be information security experts, but they do need to be involved through leadership, governance, and communication.
Leadership
Everything lasting and meaningful in business starts with leadership—and leadership starts with you.
I have built enough information security programs over the past 20 years to know that there is one thing that is more important than any other, and that is leadership. Without leadership, buy-in, and active endorsement from executive management, any legitimate efforts to secure information are doomed to failure. Leaders who take information security seriously can, and do, speak about information security within their organizations. Leaders who take information security seriously:
- know what their most significant risks are.
- know how much information security costs them.
- know how information security helps them retain customers and attract new ones.
- know that information security goals and objectives are aligned with the organization’s goals and objectives.
- lead by example through compliance with policies and involvement in key initiatives.
Starting an information security program starts with you. As the CEO of your organization, if you are not prepared and willing to participate in information security, then your organization probably isn’t ready to start an information security program; at least not in a way that will be most effective for your organization or its customers.
Effective information security leadership begins with commitment. The commitment must be:
- Documented
- Your commitment to information security must be documented in policy, but should also be documented in marketing materials and customer agreements.
- Verbally communicated internally and (on occasion) externally
- Internal communications can include mentioning information security in corporate meetings and gatherings.
- Demonstrated through action
- Actions can include the establishment of the information security program, setting a dedicated information security budget, enforcement of policy provisions, and many others.
If you feel that you are ready, then what’s next?
Establish Governance
As the CEO of your organization, you don’t have time to run the day-to-day functions of an information security program. The first step to building an information security program is to establish governance. Who will be responsible for which processes and technology?
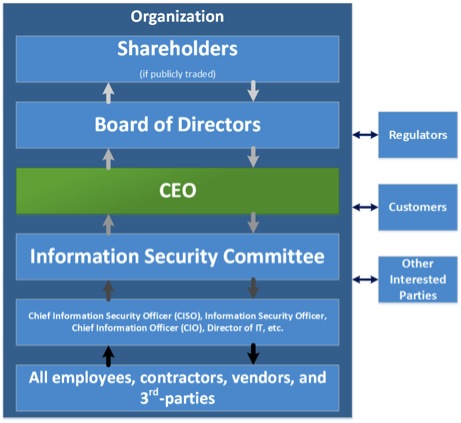
Information security governance consists of determining who within your organization will be responsible for what. Start with defining how information will flow for the information security program; both strategically and tactically.
In Figure 1 (above), the arrows depict how information flows through a typical information security program. The darker the arrow is, the more tactical the information is. Each level of governance within the information security program should be associated with a specific set of responsibilities.
We could devote an entire book to the topic of information security governance, but the focus for this series is on you, the CEO. In this article, we’ll concentrate on the roles below yours because these are the roles that you are most responsible for filling:
- Information Security Committee
- CISO, ISO, CIO, etc.
- All employees, contractors, vendors, and third parties
It’s important to note that the governance for your information security program may differ slightly from the one depicted here, but the concepts are identical. It doesn’t matter if there are additional layers in your information security governance or less. What matters is that there is a governance structure and it defines roles, assigned responsibilities, accountability, and communication for your information security program.
Communication
Arguably the most important feature of effective information security governance is communication. Communication between all roles must be regular and transparent.
According to a recent study by the Ponemon Institute, nearly one third of IT security teams never speak with company executives about information security. Equally as bad, only 23 percent of those who have spoken to company executives, only do so once per year. Jeff Debrosse, director of security research at Websense, predicted that the “31 percent will, at some point, find themselves on the front page”.
Mr. Debrosse’s prediction is spot on. Good governance results in good communication.
Information Security Committee
Committees have a bad rap. Most committees get a bad rap because they have been poorly organized, poorly attended, and poorly directed. The Information Security Committee must buck this trend through:
A documented charter containing:
- Purpose
- Scope
- Membership
- Responsibilities
- Schedule
- Documented meeting agendas
- Documented meeting minutes
Common responsibilities for the Information Security Committee could include:
- Formulate, review, and recommend information security policy
- Review the effectiveness of policy implementation
- Provide clear direction and visible management support for security initiatives
- Initiate plans and programs to maintain information security awareness
- Ensure that security activities are executed in compliance with policy
- Identify and recommend how to handle non-compliance
- Approve methodologies and processes for information security
- Identify significant threat changes and vulnerabilities
- Assess the adequacy and coordinate the implementation of information security controls
- Promote information security education, training and awareness throughout the organization
- Evaluate information received from monitoring processes
- Review information security incident information and recommend follow-up actions
The Committee communicates regularly and periodically with the CEO, and with the person who has many of the day-to-day responsibilities (CISO, ISO, CIO, etc.).
The sommittee must be staffed with personnel who can speak for parts of the organization with authority and personnel who can serve as advocates for information security initiatives. Ideal personnel for committee membership are business unit leaders, and an ideal size for the committee is 6–8 members.
CISO, ISO, CIO, etc.
This is the person with day-to-day security management responsibilities.
It doesn’t matter is this person’s title is Chief Information Security Officer, Information Security Officer, Chief Information Officer, or Director of Information Technology.
This is the person who is responsible for ensuring that management’s (ultimately yours as CEO) direction with respect to information security is carried out in compliance with policy and business processes. The responsibilities must be documented, communicated, and measured.
Some typical responsibilities may include:
- Ensure compliance with applicable information security requirements
- Ensure preparation and maintenance of plans and procedures to address continuity of operations for information systems that support the operations and assets of the organization
- Ensure that the organization has trained its personnel to support compliance with information security policies, processes, standards, and guidelines
- Report annually, in coordination with the senior managers, to the Information Security Committee on the effectiveness of the Information Security Program, including progress of remedial actions
- Head an office tasked with the mission and resources to assist in ensuring organization’s compliance with information security requirements
- Assess risk and magnitude of the harm resulting from unauthorized access, use, disclosure, disruption, modification, or destruction of information and information systems that support the operations and assets of the organization
- Develop and maintain information security policies, procedures, and control techniques to address all applicable requirements throughout the life cycle of each organizational information system
- Facilitate development of subordinate plans for providing adequate information security for networks, facilities, and systems or groups of information systems
- Ensure that company personnel, including contractors, receive appropriate information security awareness training—including incident response and incident management
- Train and oversee personnel with significant responsibilities for information security with respect to such responsibilities
- Implement and maintain a process for planning, implementing, evaluating, and documenting remedial action to address any deficiencies in the information security policies, procedures, and practices of the organization
- Develop and implement procedures for testing and evaluating the effectiveness of the Information Security Program in accordance with stated objectives
- Review and manage the information security policy waiver request process
In essence, this person takes the direction from the CEO and Information Security Committee and implements it.
All Employees, Contractors, Vendors and Third Parties
Everyone has a role and responsibilities with respect to information security. Information security is not and IT issue and participation is not limited to IT personnel. Initially, responsibilities may be as simple as:
- Understand all of the information security policies that make up the information security program
- Use organizational information and other information-related resources in compliance with all Information Security Policies
- Seek guidance from the information security committee on information security related matters that are not clear
- Communicate with the members of the information security committee regularly by providing feedback
These responsibilities may seem like common sense, but then again, there is no common sense in information security.
Part 2
The Jigsaw Puzzle
An analogy that I often use for putting together an information security program is that it’s like putting together a jigsaw puzzle. Each piece of the information security program should fit nicely with all the other pieces in order to create a picture of what information security looks like. Now that governance is defined, we can begin with putting the puzzle together.
Choose a Standard
An information security standard is like the picture on the box of your jigsaw puzzle. Once the puzzle/information security program is completely built (which it never really is), it should look like the picture/standard. There are numerous standards to choose from, and you (as the CEO) don’t necessarily need to be involved in choosing one. This is a task that can be delegated to the Information Security Committee and/or tactical security person. What you do need to know is that a standard has been chosen and which one it is. Some good standards to reference:
- ISO/IEC 27002:2013 – An international standard titled “Information technology – Security techniques — Code of practice for information security controls”
- NIST SP 800-53 – A Special Publication (SP) and standard developed by the National Institute of Standards and Technology (NIST) titled “Security and Privacy Controls for Federal Information Systems and Organization”
- COBIT – Control Objectives for Information and Related Technology (COBIT) is a framework created by ISACA for information technology (IT) management and IT governance.
- NIST Cybersecurity Framework – A security framework released by NIST in early 2014 that contains references to multiple well-known information security standards.
A standard gives your organization a baseline of controls to draw from and measure yourself against.
Policies
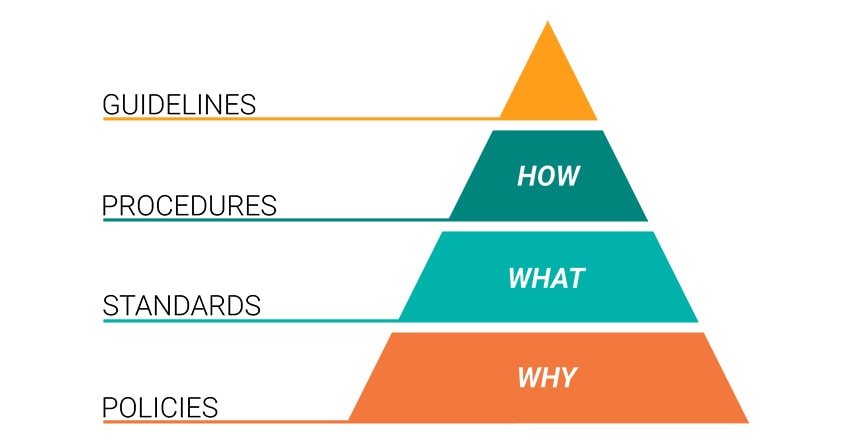
Now that we have chosen which jigsaw puzzle we want to build from, we start putting it together. Most people begin putting together their jigsaw puzzle by starting with the edge and corner pieces. In our analogy, the edge and corner pieces for our information security program are the information security policies. The information security policies provide the framework for all information security initiatives within the organization and hold everything together. You don’t have to worry. Rarely do CEOs write policy, but they do need to read them and approve them. There are three things that should be done at this point:
- Develop and document a policy approval process
- Determine which policies should be written
- Write, approve, and adopt (enforce) policies
Policy Approval Process
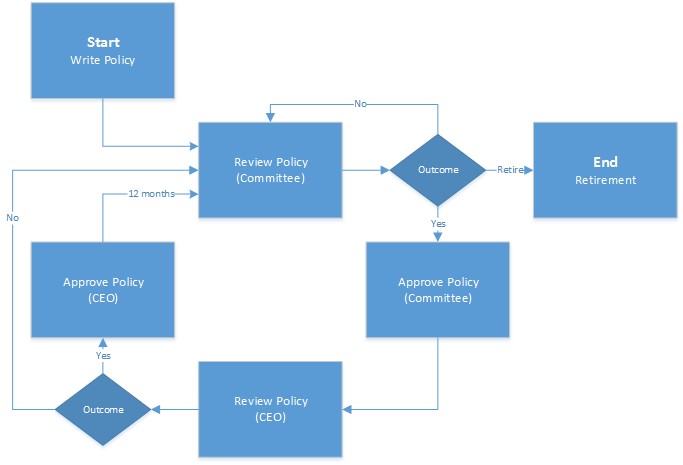
The policy approval process varies from organization to organization. The process you choose (or that your Information Security Committee chooses) should fit with your governance (see above) and your culture. Figure 2 depicts a simple and effective policy approval process.
Ensure that all information security policies are formally reviewed on no less than an annual basis and that you (as CEO) are willing and able to enforce the requirements listed in them.
Write and Approve Policies
How does your Information Security Committee (or tactical security person) determine which policies should be written? There are four things to keep in mind:
- The picture on the box. The standard that was chosen earlier will help determine which policies should be developed.
- Everything that we do with respect to information security must find its root somewhere in policy. Information security policies provide the authorization for all personnel to do their jobs as they relate to information security. Without authorization, there can be no real enforcement. Without enforcement, we have no real security.
- Policy structure. Information security policies must be structured in a manner that makes them easily referenced. Far too many organizations write their policies as books when they should be written like dictionaries. Nobody reads policies, so we need to make them easily referenced.
- Develop one charter information security policy that drives the entire program and support this policy with many issue or topic-specific policies. This will help with referenceability.
Every policy requires CEO approval and compliance is mandatory (even for you).
Adopt and Enforce Policies
Now that we have the edge pieces (policies) of our jigsaw puzzle (Information Security Program) in place, we can begin to locate and place the inner pieces. Inner pieces include the standards, guidelines, procedures and technologies that enable your organization to comply with policy provisions. It’s important to note three things during the adoption and enforcement of policies:
- An approved policy does not mean an adopted policy. An approved policy is one that contains statements of management direction. There will be a period of time between policy approval and full policy adoption. In some cases it takes more than a year to design and implement the inner pieces of your jigsaw puzzle.
- Policies are worth nothing if there is no intention to enforce them. At this point, it is assumed that you have read the policies and have the intention to enforce each of their provisions.
- There are always exceptions. Exceptions usually come in the form of extenuating business circumstances. For those policy provisions that, for whatever reason, cannot be complied with, there should be a documented exception process that must be followed. Policy exceptions can/should be handled by the Information Security Committee and should be reviewed on no less than an annual basis.
At this point, a manageable and effective Information Security Program lifecycle has begun.
Regular Reporting
A CEO of an organization should receive updates to the Information Security Program and significant events on no less than a quarterly basis. The updates don’t need to be exhaustive and full of detail, but they should aid you in addressing the points that I posed early in this post. Leaders who take information security seriously:
- know what their most significant risks are
- know how much information security costs them
- know how information security helps them retain customers and attract new ones
- know that information security goals and objectives are aligned with the organization’s goals and objectives
- lead by example through compliance with policies and involvement in key initiatives

A Tale of Two Companies
This is an example of two real companies in the printing industry.
The printing industry is very competitive with constant pricing pressure from clients and shrinking margins. In this example, I will contrast two real printing companies and the approach each CEO has taken to information security.
One company has a CEO and leadership team that takes information security seriously and the other is content with going through the motions. We’ll call these real companies Get It Right Printing and Only the Motions Printing.
Get It Right Printing
Get It Right is a 450+ employee strong printing company that has invested the time and effort required to build a formal information security program. For this company, information security starts with the top. The CEO of the company sets an example for the other employees to follow.
Get It Right Printing has established an information security committee comprised of leaders from the company’s business units and meets on no less than a monthly basis. The CEO gets regular updates from his information security committee and regularly provides feedback to the information security committee.
Get It Right has written and approved (by the CEO) thirty information security policies; each one written with a specific topic/issue addresses.
The company has written their policies this way in order to assist employees with being able to quickly find what they need in their policies rather than forcing each employee to read one large policy.
Each policy that has been written and approved is enforced.
The Get It Right Printing information security program has been established and now the company works on tweaking and maturing the program over time.
The Results
Get It Right Printing takes information security seriously and has real evidence to support their claim.
Customers feel confident in the company’s ability to protect their information, and the company is able to conduct business with a clientele that other printing companies cannot. This is especially true for large, heavily-regulated customers like banks, finance companies, health insurance companies, and others.
Get It Right has an information security program that attracts customers. Get It Right Printing is now running at capacity for three shifts in two locations and looking for additional expansion. Business is good at Get It Right and the CEO knows two things:
- They have found a return on investment with information security.
- It all started with his involvement and endorsement.
Only the Motions Printing
Only the Motions Printing is a 300+ employee printing company that competes directly in the same space as Get It Right.
The company CEO states that information security is important to his organization, but clearly doesn’t participate or demonstrate commitment. The company is constantly struggling to satisfy a few key customers and it’s a never-ending reactionary cycle to meeting customer information security demands.
There is no formal information security program at Only the Motions Printing.
The Results
One of the few key customers is no longer satisfied with the reactionary approach to information security and is now demanding that Only the Motions obtain an independent audit report (SOC 2).
If this key customer decides that it’s too risky to do business with the company, there is a significant and real risk that that customer will go elsewhere. Only the Motions is not prepared for an independent audit report because there are too many deficiencies in their information security program. There is no foundation for their information security program. The company is at a crossroads. Invest thousands to build the information security program that they should have already built (see there never really was a choice at the beginning) and try to rescue this existing customer relationship, or continue down this existing path and lose this existing customer. Keep in mind that losing this existing customer will cost Only the Motions Printing 30% of their existing revenue.
Summary
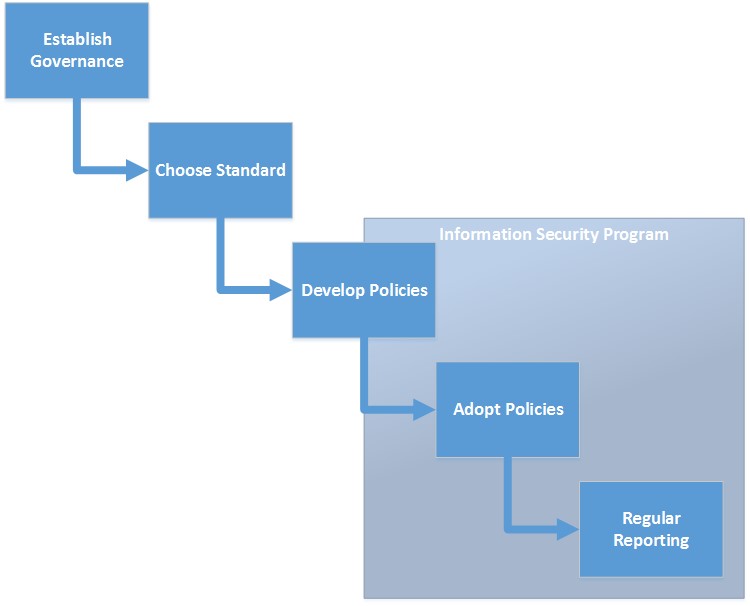
Which company would you rather be? Which company would you rather invest in? As the CEO of your organization, it is imperative that you participate in the development and adoption of your organization’s Information Security Program. The degree to which you participate has a direct impact on how well your organization protects sensitive information. Many of the tasks associated with building your Information Security Program can be delegated, but ultimate responsibility cannot. At a high-level, the Information Security Program development process is depicted below in Figure 3.
Now that an Information Security Program is firmly in place, the organization can safely transition into the ongoing management and refinement of the program, and hopefully you can sleep a little better each night.
For assistance with building or developing your security program, risk management efforts, policies, training, and more, check out our vCISO offerings at frsecure.com.