Now you know about benefits of using a timeline on technological and intellectual levels.
But how can you create a file system forensic analysis timeline? There are some open-source timelining tools that are available to anyone looking to conduct a digital investigation.
Here are some examples of these tools and how you can use them for yourself.
The Process
From a high level, generating a system timeline is just a two-step process.
Gathering Data
In the first step, we gather data from a suspect host and save it as a file in raw data format.
For this, I’ll use Eric Zimmerman’s MFTECmd.exe tool.
It is important to note that we will use MFTECmd.exe to pull data from a system’s $MFT, or “Master File Table,” which is a database that contains information on every single file and folder in an NTFS volume.
NTFS is a Windows-specific file system, but drives that use NTFS can be attached to other systems and read in Mac OS, Linux, and even mobile operating systems like iOS or Android.
If you’re working with a volume that is not using the NTFS structure, FLS is a good alternative that is included in TSK, or “The Sleuth Kit.”
FLS will work on Mac OS, Solaris, Linux, as well as other file systems including NTFS and FAT—the original Windows file system that NTFS replaced.
Building the Timeline
The second step in building a timeline is for us to sort that raw data and arrange it into a single readable file.
Thankfully, there are free tools to achieve such a task. For this article, I will use a tool called Mactime, which is also a part of TSK.
As a prerequisite for Mactime, if you are performing your timelining on a Windows machine, you’ll need to have a Linux subsystem installed and activated. If you have a 64-bit version of Windows 10 or Windows Server 2019, a Linux subsystem is included and can be turned on by going to Control Panel > Programs and Features > Turn Windows Features On or Off > and activating ‘Windows Subsystem For Linux.’
This action will require a reboot.
You can then search for “Ubuntu” or “Kali Linux” in the Microsoft store and click “Get” to install it automatically for free.
Now that I’ve got MFTECmd.exe and Mactime downloaded to my C: drive, I’m using a Windows 10 workstation so I’ve got my Linux subsystem turned on, and an image of a system believed to have been compromised is mounted as my local E: drive; I’m ready to start timelining.
Open a Command Prompt
The first step is to open a command prompt and navigate to the folder containing MFTECmd.exe. To start, here is an output of options for the command we will use:
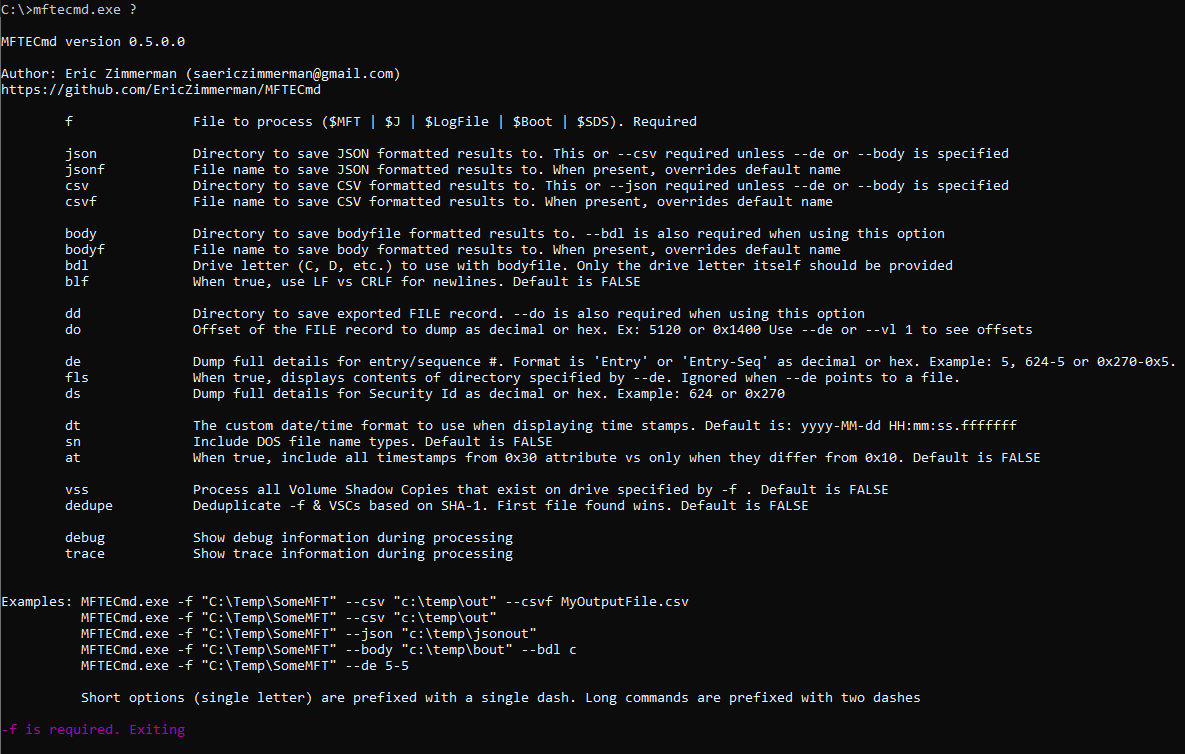
The command syntax I will use is:
“MFTECmd.exe -f E:\C\$MFT –body {directory where I want the output} –bodyf {name of the output} –blf –bdl {drive letter to be used in the new bodyfile}”
The file “E:\C\$MFT” is expressed this way because we’re searching the Master File Table ($MFT) on the C: drive of our suspect system (C\)—the image for which is mounted on my local E: drive (E:\). It’s recommended to include “–blf” for readability.
My final command is:
MFTECmd.exe -f “E:\C\$MFT” –body “\Users\AMBUSH\Documents\” –bodyf BodyFile.body –blf –bdl C:
With this, step one is complete. I now have a body file called “BodyFile.body” that I’ll take on to the next step.
Mactime Tool
For this next step, we’ll use the Mactime tool in Linux bash or in your Linux subsystem if you’re using a Windows workstation like me.
Mactime is a Perl script that takes a body file and parses its contents into a format that we can make sense of with our human eyes. We can specify a date range and the time zone that we want events presented in.
Here is the command syntax I will be using, from the folder containing the Mactime tool:
“ mactime -z {timezone I want output represented in} -b {file body location and name} -y -d {start date} {end date} > {output file location and name, ending with extension .csv}”
For timezone, specified by the -z tag, UTC is recommended for clarity and uniformity.
The file we want parsed is specified by the -b tag.
From our earlier step, we know that my body file is located here: \Users\AMBUSH\Documents\BodyFile.body.
The -y tag is to display dates in ISO 8601 format, and the -d tag puts the output in comma delimited format. Both of these are necessary for the output we want.
After these tags, we specify our date range in the format, yyyy-mm-dd. When the starting and end date are specified, use “>” to put the output in a new file. Be sure to specify where you want this new file, and make sure it has the .csv extension.
My final output for looking over MFT records for the full month of September 2020 looks like this:
mactime -z UTC -b /mnt/c/Users/AMBUSH/Documents/BodyFile.body -y -d 2020-09-01 2020-09-30 > /mnt/c/users/AMBUSH/Documents/Sept2020Timeline.csv
And there we have it—a fresh master file table timeline covering one month of events on the host suspected of being compromised.
.CSV files can be viewed in many tools, including Microsoft Excel, but I prefer Timeline Explorer, another Eric Zimmerman tool that I have linked at the end of this post.
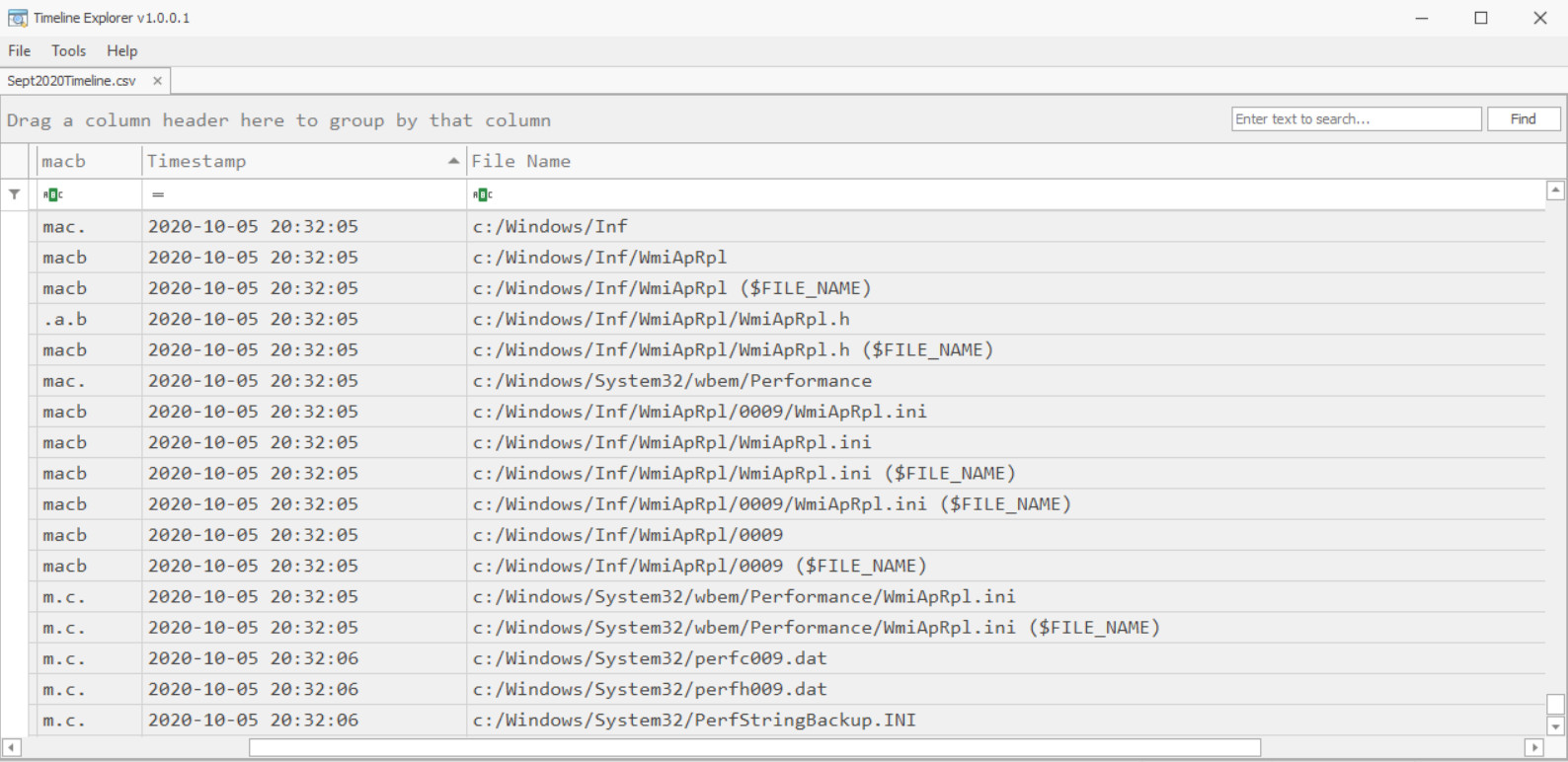
You can see a small portion of the output below as it appears in the Timeline Explorer GUI.
What This Means
The “macb” field, often expressed as “MAC(b),” gives us details regarding the action that took place on a file or directory.
The four characters stand for:
- Modified
- Accessed
- Changed ($MFT Modified)
- Birth (initial file creation, often in parentheses because not all file systems record a birth time)
As simple as these four properties may seem, it is important to keep in mind that each line in our timeline gets their macb characters from one of two different file attributes within the Master File Table.
These attributes are called “%STANDARD_INFO” and “$FILE_NAME.”
$STANDARD_INFO
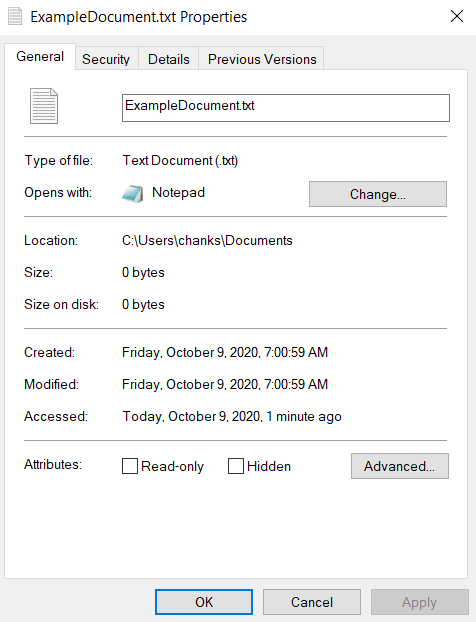
$STANDARD_INFO displays these properties and timestamps like created date, modified date, or accessed date as we would see them if we were to right-click on a file in Windows and check the properties.
These properties can be easily modified by using a technique called Timestomping.
Malicious attackers may change these properties to mimic other files in the same directory so that they do not appear suspicious to forensic investigators or our analysis tools.
$FILE_NAME
The $FILE_NAME attribute is different, and its timestamps are much more difficult to manipulate.
Changes to this attribute must come from the Master File Table itself, not a user. As a result, these entries show us when a file was created, copied, or moved.
Entries with timestamps pulled from the $FILE_NAME attribute will display the text “($FILE_NAME)” at the end of the file name field in our timeline (See example 1.2 for six entries matching this output). It is useful to have timestamps for both attributes included in our timeline because we can compare and contrast to determine if $STANDARD_INFO properties have been modified.
For example, if a file says it was birthed at 10am on January 5, 2020—the same time as 100 other wholesome files in the same directory—it may appear that the file is innocuous. However, if we see another timeline entry for the same file showing it was birthed on September 15 and that entry contains ($FILE_NAME) at the end of it, we know that the file was actually created on September 15.
Therefore, the “b” attribute was modified in order to deceive us.
Threat Hunting
With such a clean, chronological presentation, easy-to-use time and word filters available, combined with our knowledge of modification times and the ways to verify them, we’re ready to begin threat hunting.
You can start with a time of compromise, suspicious user account directories, a filename or folder that may have been used in the attack. With Timeline Explorer, you can filter, group, and sort events, files, and directories by name, location, date, or the type of modification you’re interested.
Are you looking for when a folder was created in the system’s Syswow64 folder? Maybe you want to see when a particular document was moved to the recycle bin?
As powerful as this information is to a digital forensic investigator, it is still limited to what the host’s Master File Table contains. Even though we can see files and directories as they were manipulated, it is still only part of the history of this system.
In the third and final part of my timelining series, I will be discussing how to take what we’ve learned here and apply it to create a Super Timeline, a timeline of timelines, so to speak. A Super Timeline does not mean slapping a big ‘S’ and a cape on a timeline, it is the result of combining multiple timelines like this one and correlating them so that the events of each are represented with accurate, sequential timestamps and events that we can investigate, all in one file.
File System Forensic Analysis Resources
- MFTECmd.exe download: https://github.com/EricZimmerman/MFTECmd
- SleuthKit/Mactime/FLS download: http://sleuthkit.org/sleuthkit/download.php
- Mactime Output: https://wiki.sleuthkit.org/index.php?title=Mactime_output
- Timeline Explorer: https://ericzimmerman.github.io/#!index.md
- MFT Timestamp properties: https://www.sans.org/blog/windows-7-mft-entry-timestamp-properties/
This article was written by Cory of Team Ambush
In the meantime, if you have questions about forensic analysis, timelining, or threat hunting, please do not hesitate to leave a comment or reach out to us at frsecure.com.







