With all the fake news and security threats out there today it’s important to know how to tell if a website is trustworthy or not. Generally-speaking if you have any doubts it would be in your best interest to not believe the contents of or engage with any given website. If you want to investigate though there are several things you can look out for that will give you a better sense of the safety and reputation of any given website. The following are several website trust signals to look for next time you question the authenticity and/or safety of any given website.
Alexa Rank
How much traffic does Alexa think their website receives? An Alexa Rank less than 100,000 overall or in your country is a good sign. Just because a website receives lots of visitors doesn’t ensure that it’s reputable, but it does make it more likely.
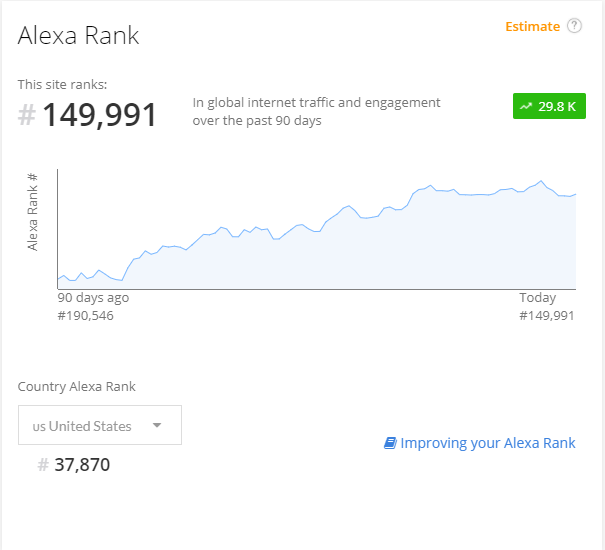
You can check any website’s Alex Rank via the Alexa website or the Chrome Extension.
Website Encryption
Is their website encrypted using an SSL certificate? Many malicious websites have SSL certificates installed too, but nonetheless it’s a good sign when a website is using one.
Ensure your visit is encrypted by looking for the following green lock and green https:// on every page visited in Google Chrome:
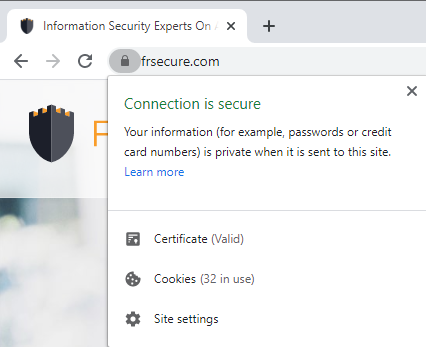
You can check for an SSL certificate on any website using this SSL Checker.
Archive.org History
Take a look at what the website used to look like. If there’s no history it’s probably a newer website, which is a bad sign. If the site used to be used for a wildly different purpose than it is now it could also be a bad sign.
You can lookup historical versions of any website using the Wayback Machine.
Link To Website Uses A Generic Short URL
If the link to the website uses a generic short URL service such as bit.ly ,goo.gl or t.co it’s a good idea to be cautious. Rather than immediately clicking on the shortened link you can find out where it will take you before doing so.
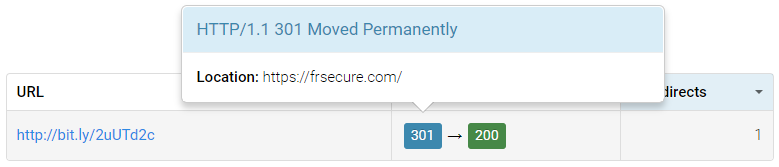
You can copy and paste any shortened URL into the HTTP Status Code Checker and it will tell you what URL it ultimately redirects to as follows:
Otherwise if it’s a bit.ly link you can simply add + to the end of the URL to see where it goes. For example this bit.ly link (http://bit.ly/2uUTd2c) goes to the frsecure.com home page and when you add a + to the end (https://bitly.com/2uUTd2c+) it shows you it links to https://frsecure.com/ and tells you how many clicks it has received.
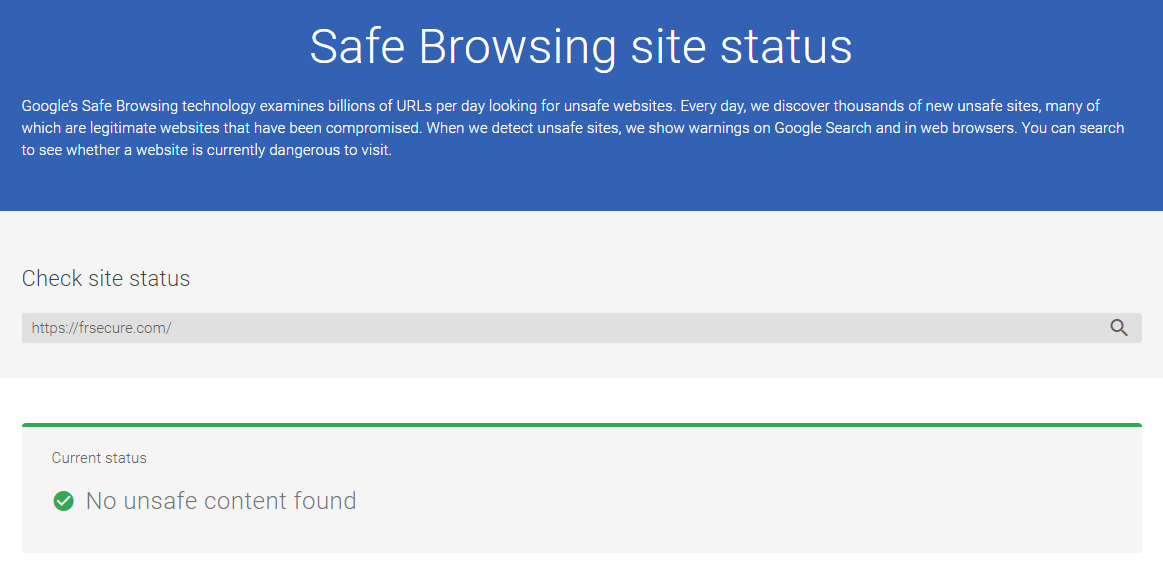
Google Transparency Report
Scan the website with Google’s Transparency Report Safe Browsing site status tool to see if Google has detected any unsafe content on the domain.
Physical Address
Do they list a physical address on their website? Is it a real address? With Google Maps street view it’s pretty easy to verify the address is real. This is a very good sign of authenticity.
The People
If the people behind the website are not listed or referenced anywhere on the website that is a very bad sign. If they are some quick Google research on them may be in order if you’re still unsure about any given website’s authenticity.
Non-Branded Email Addresses
If there are email addresses listed that don’t share the domain of the website it’s not a very good sign. Authentic websites are more likely to utilize branded email addresses.
WHOIS Record
Look at the domain WHOIS record.
- If they are hiding their registrant contact information the reason may not be an innocent one.
- If the creation date is very recent it’s not a good sign because the website hasn’t existed very long.
- If the expiration date is in a year or less it’s also not a good sign since it implies they aren’t necessarily planning on sticking around.
frsecure.com WHOIS RECORD
Domain Name: frsecure.com Registry Domain ID: 1406799585_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.godaddy.com Registrar URL: http://www.godaddy.com Update Date: 2017-05-18T19:22:07Z Creation Date: 2008-02-20T20:59:37Z Registrar Registration Expiration Date: 2026-02-20T20:59:37Z Registrar: GoDaddy.com, LLC Registrar IANA ID: 146 Registrar Abuse Contact Email: Registrar Abuse Contact Phone: +1.4806242505 Domain Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited Domain Status: clientUpdateProhibited http://www.icann.org/epp#clientUpdateProhibited Domain Status: clientRenewProhibited http://www.icann.org/epp#clientRenewProhibited Domain Status: clientDeleteProhibited http://www.icann.org/epp#clientDeleteProhibited Registry Registrant ID: Not Available From Registry Registrant Name: Kevin Orth Registrant Organization: FRSecure Registrant Street: 5909 Baker Road Suite 500 Registrant City: Minnetonka Registrant State/Province: Minnesota Registrant Postal Code: 55345 Registrant Country: US Registrant Phone: +1.9524421709 Registrant Phone Ext: Registrant Fax: Registrant Fax Ext: Registrant Email:
You can check any website’s WHOIS record with who.is.
Other Website Trust Signals To Look For?
What other signals do you look for when you do your website trust check? What did I miss? Please share your wisdom.