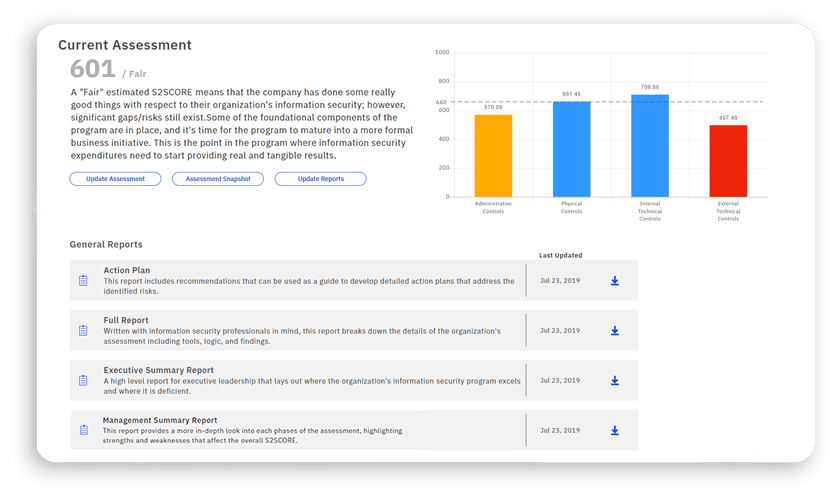
If your information security program is like most, everything you do is predicated on the results of your risk assessment. A risk assessment is effectively a review of your entire information security program, and it tells you which areas you’re risk-averse and which areas need TLC.
The context of risk is important here. Risk is the likelihood of something bad (compromise) happening and the impact if it did.
The likelihood is almost never zero.
If your information is connected to a network, there’s a chance it can be commandeered.
So, instead of trying to eliminate all risk, security teams must work with their business leaders (see executive leadership team, C-suite, or board of directors) to determine what’s an acceptable level of risk for the organization.
What happens when you get there?
You Can’t “Achieve” Security
Our information security risk assessment scoring is on a scale of 300 to 850. While acceptable risk will vary from organization to organization, 660 is a risk assessment score we shoot for with most of our clients.
But you can’t just get to 660 and stop making strides.
First of all, an acceptable level of risk is no easy task. With our virtual chief information security officer (vCISO) clients, building a security program from scratch to meet its acceptable risk level is usually a three-to-five-year endeavor. Doing this requires a change in culture and a change in how the organization works.
That’s going to take time.
Not every organization will take that long, and not every organization needs to start from scratch. Whether you’re working with a vCISO, or you have an incredible team of internal security experts and information technology gurus, you may be finding yourself in a position where you’ve reached your acceptable risk threshold.
This is not the time to become complacent with or cut back your security efforts. This is when you recalibrate.
Optimizing Efficiencies
There’s a shift in mentality that needs to occur when you reach your acceptable risk level organizationally. Constant improvement is a centerpiece of good security programs, and like I already mentioned, you can’t “achieve” security.
During the three-to-five-year building period, clients typically spend more on information security than they ever have on new tech, employee hours for documentation, and more.
Once you’ve gotten to an acceptable level of risk within the organization, the focus should naturally start to shift from implementing things to manage your most significant risks to increasing efficiency and reducing those operational costs and becoming more cost-effective.
This can be done in a number of ways, but typically can be boiled down to the automation of manual processes and auditing or improving processes and plans.
Automation
Part of optimization is driving down costs. Many organizations tend to think of information security as a cost center, but done well, this shouldn’t be the case. Automating the systems and processes you have in place is going to help reduce the operational overhead of the department.
With automating systems, the first step is always to look at how many hours your team is spending doing manual tasks like creating reports, filtering data, cleaning lists, etc. This will allow you to get a bigger picture of what the cost savings of automating these tasks will look like. Then, determine what to automate based on those savings.
Some common things to automate include:
User Account Audits
Often, someone on the security team or IT team is in charge of sifting through all the users in accounts like your sales tools, online file storage systems, and anything else that might contain critical business information.
To determine user access levels are correct, which accounts have been dormant for some time, and who needs to be removed due to employee turnover, this certainly takes some time.
Now that you have a process to review this in place and your risk assessment score is at a place your organization is comfortable with, this is something that can and should be automated.
Figure out who the control owner should be, and see if you can automatically send these to the control owner. For example, if you create a user account for a team member and they haven’t logged in to their account in the last 60 days, can the system automatically send you an alert to suspend their account (or do it for you)?
This both limits the security concern of dormant accounts and saves your team lead time and energy in determining who needs access and to what level.
Asset Inventory
Asset inventory is paramount to good security practice. Without knowing what you need to secure, it’s impossible to guard the sensitive information associated with it.
It’s easy to recognize that devices need to be accounted for. Anything connected to the network poses risk to the organization. But software and data should also be inventoried. Software is virtually always connected to the internet, and most companies would find themselves shutting doors for good if all of their data suddenly disappeared.
Knowing this, how can you reduce the friction in your asset management strategy?
Often, that means automating in the inventory process. Tools exist today that can help organizations track equipment, which is especially pertinent with today’s work from home and remote learning climate. Not only does something like this reduce the time it would take for an IT employee to log and track who devices are being loaned to and where they’re going, but it also improves the accuracy.
The same is true of your software and data. To track licenses, review network assets, add or remove licenses, monitor installs, and scan everything for security gaps would take a monumental amount of employee time and effort to do manually.
This is where the effort analysis (hours of work for tasks) comes in handy. Even with the cost to purchase and implement inventory systems like this, it’ll likely still save money considering the time it would take an IT employee to do this manually (and well).
SIEM
The combination of logging and alerting is a practice that has extremely tangible security benefits. Having automation in place to log possible security events and then alert the appropriate party of any potential threats can snuff out a possible security incident before it even occurs—or allow you to retrace steps if one does happen.
As a program matures, it’s common to implement a SIEM solution.
Security Information and Event Management (SIEM) solutions aggregate data, search, and report. SIEM gathers data from an organization’s network environment and consolidates it into a digestible format for human consumption. With reporting and forensics data about security incidents and alerts, it allows organizations to research any data security breaches with as much detail as needed.
Mainly, this move levels up security programs by limiting noise from false positives and by helping maintain data integrity in the face of denial-of-service attacks, brute-force attacks, and other data breaches.
Internal Auditing
Internal audits are practices that companies who have reached an acceptable risk threshold may not always have. Aligning closely with asset management, an internal audit (on the IT and security side) typically looks at all things from finances, ethics, controls, networks, threats, opportunities, and more.
While departments will often do this organically, it’s not uncommon to have no formal process in place. We’ve found that among our vCISO and risk assessment clients, it’s reasonable for you to achieve a 700 without having a formal internal audit process in place.
As most of us recognize the credit score scale, it might come as a surprise that an organization with that impressive of a score could be missing such a large driver of success. If you stop and think about it, though, it actually makes sense. You can’t audit things that don’t exist. At a 700, the organization will now have the processes and artifacts in place to be able to conduct an audit against.
So, passing the risk assessment threshold you set for your organization is a good time to put this practice in place—or to automate the one you have.
Do some research on tools that can help you conduct internal audits (not spreadsheets), but also be mindful of how you might be able to use the tools you already have in place to help you conduct your audits.
Plan Improvements
Remember, this stage of the game is about constant improvement—taking what we’ve implemented already and making consistent tweaks as new contributing factors arise.
Planning may be the constant improvement poster child of the security world.
As new technologies, new employees, new ways of doing business, new sets of data, new devices, new threats, and more enter our environment, the plans should be designed and implemented to accommodate them. Renewing plans and keeping them relevant is something that should be ongoing for any organization. And reaching your target risk assessment score breathes new life into this.
IR, BCP, and DR
Incident Response (IR) plans, Business Continuity Plans (BCPs), and Disaster Recovery (DR) plans are critically important to the success of the business and require significant input from the security and IT teams internally.
- Incident Response Plan: What do we do in the event of a data compromise?
- Business Continuity Plan: How do we continue to operate as a business despite crises?
- Disaster Recovery Plan: In the event of a disaster, how do we reclaim what was lost?
It’s not likely your organization is missing these if you have a high risk assessment score. Remember, the impact to the business if something bad were to happen is part of risk, and not having these plans would drastically increase the impact.
Since you should (and probably do) have these in place, we circle back to this idea of constant improvement. And the best way to improve plans is to see how they perform in action.
Often, plans simply check a compliance box. Compliance tends to be a minimum requirement and not an approach that will always satisfy your acceptable risk level. So, you’ll need to practice how they’d hold up in a real-life situation— starting with tabletop exercises and then moving to actual testing of your plans.
A tabletop exercise puts your IR plan, DR plan, or BCP up against a likely scenario so that you can see its effectiveness. This will show your organization which staff is missing from the execution of your plan, and where the plan itself falls short.
It’s not often we advocate for complexity in security, but when it comes to dealing with an incident, crisis, or disaster, it’s important to consider every angle. Plans need to be all-encompassing, and table-topping will ensure they are.
- Incident Response: Simulate an incident. Ensure that your most current plan weathers the storm. This is a difficult plan to test beyond the tabletop so ensure that after any incident you conduct a “lessons learned” session and update your plan accordingly.
- Business Continuity: While harder to test, ensure that all the working parts are in place to keep the business running while crisis strikes. Draw on what you learned from COVID-19.
- Disaster Recovery: Start by considering the need of failing-over your data center. Walk through the process with the required staff. When you feel comfortable, back it up. Then, test the recovery process in a test/DR location, and include user acceptance testing of the recovered systems. The highest level of testing, done during off-hours, could be to pull the internet connection on your production site, ensure everything fails over as expected, and still works.
Testing and adjusting these plans are necessary components to your security program post-risk-assessment.
How Your vCISO Can Assist After an Acceptable Risk Threshold
With risk at an acceptable level, it’s easy to feel like you can take your foot off the gas. It’s not uncommon for organizations who use a vCISO to get to this point reconsider their relationship with their provider. You’d be doing your organization a disservice if you cut ties with your vCISO just because your risk assessment score is high enough, though.
Squash Complacency
Complacency is the enemy of progress. Again, security is not a point-in-time exercise, rather something that needs to be built, rebuilt, tweaked, updated, and constantly scrutinized on an ongoing basis.
It’s natural for organizations to make security an afterthought or pump the breaks once they reach their risk goal. A “goal” in and of itself typically indicates a finish or stopping point.
But, when security is woven into the fabric of your daily life (and when you get paid to make that the case), complacency doesn’t exist. It’s a vCISO’s job to help build and/or improve your information security program—not just to pass a test with your leadership.
A good vCISO will work with you to help you be aware of how your cyber security efforts are impacted by industry changes, threat landscape changes, regulatory changes, and organizational changes (restructuring) so you don’t stop gaining momentum.
Plan Improvement and Testing
I touched on the importance of plan improvements and testing already. Adjusting and testing policies, procedures, and plans is no easy task.
Without a keen understanding of the current industry, threat, and regulation landscapes, it’s challenging to adjust them in a way that minimizes risk and satisfies all requirements. Without the right tools, knowledge, and real-world experience, it’s challenging to test plans based on scenarios that may happen in real life.
vCISOs are equipped with the things needed to successfully build plans, adjust plans, and push plans to their limits. Doing these exercises without vCISO services may be more difficult and less encompassing than it would with their assistance.
Tool Recommendations
A good virtual CISO service won’t sell you products. But they do have an intimate knowledge of the market, your security program, and your network environment, which gives them the ability to recommend products and solutions that will satisfy your needs as an organization.
As you look to build upon hitting your initial risk assessment goal and consider implementing SIEM, internal auditing tools, new controls, and things that will help you eliminate manual processes, have your vCISO team provide recommendations based on their knowledge of your organization and security.
Build Culture and Executive Buy-In
A secure culture and buy-in from your executive leadership take time to achieve. This ties into complacency a bit, but the last thing you want is to build all of this momentum for your program and organization only to have it wither away because leadership thinks you’ve “achieved” your goal.
vCISOs are trained to have hard conversations with boards and executive leadership groups about the current state of their information security management, the plan for improvement, and the effort and cost to get there.
Sometimes it can take a trusted third party to spark positive change, and it’s a change that any invested vCISO is going to want to help you make. If anyone is going to be able to prove to your leadership group that your security measures need to evolve beyond the scope of your target risk assessment score, it’ll be your vCISO.
Final Thoughts About Acceptable Risk
Many organizations and security teams use the results of their risk assessments as their barometer for success and the playbook for improvement. Setting risk threshold goals is an important exercise in gauging where your organization is, but it cannot be a stopping point.
Use hitting your risk assessment goal as an opportunity to reframe your program and its efforts.
Shift from building to optimizing. Shift from adding bodies to improving the efficiencies of the ones you have. Shift to tools that can help you level up.
And let your vCISO help you along the way.
For more info on risk assessments, building strong security programs, and vCISO offerings, visit frsecure.com.