The concept of insurance can be a tricky one to navigate. At its core, insurance is meant to provide us with a safety net in case something bad happens—kind of like an incident response plan. Hopefully you never need to use it, but making the investment ahead of time can help you recover from any losses or damage more quickly.
This blanket concept is a simple one, but its practice is anything but. Despite all types of insurance effectively doing the same thing, they all have their nuances. Some insurances are required by law (auto insurance), some are optional and are meant more for monetary recovery in the event of loss (renter’s insurance), and some are a convoluted combination of both (like health insurance).
So, what do the providers look for in the people or companies they provide for, and how can we as businesses ensure that we’re covered appropriately?
Of course, we’ll discuss all of this with cyber insurance in mind—the current state of the industry and how we got there, what cyber insurance companies do, what your company can do to prepare, and what to do if your organization is deemed unfavorable for coverage.
What Cyber Insurance Looks Like Today
Naturally, the cyber insurance industry has evolved to coincide with the state of cyber threats and information security. Early cyber insurance was used as a risk management tool, but despite it gaining some prominence, events like the Y2K scare and 9/11 halted its momentum.
Eventually, the worry that companies could be held liable for inadvertently transmitting a virus to another company motivated the creation of policies.
Since, the idea of cyber insurance has shifted almost completely to protecting the business itself—payment of fines, credit monitoring, data restoration cost coverage, public relations costs, and more.
The Cyber Insurance Market is Rapidly Growing
Likely, this is because of the onslaught of ransomware and the ensuing damage it causes. A recent Fitch Ratings report says ransomware losses have contributed to an increase in U.S. (stand-alone) cyber loss ratios from 34% in 2018 to 73% in 2020. A related Hiscox report shows insured cyber losses of $1.8 billion in 2019—up an eye-popping 50% year over year.
And because of this, coverage costs and premiums are growing with it.
Premiums have more than doubled since 2015, totaling $3.15B last year. Plus, customers paid 35% more for cyber coverage in the first quarter of 2021 than they did in Q1 of 2020.
Maybe a testament to the combination of the confusing nature of insurance, the challenges the industry faced early on, and the numbers listed above, the number of organizations opting for cyber insurance coverage seems low.
Of Lockton Companies’ (a partner of FRSecure) 65,000 clients, around 250 companies buy at least $200M in protection and only 40 of them have $500M in protection. It would only take five and two insured losses respectively to wipe out an entire year’s premium.
It appears part of the hesitations or challenges surrounding cyber insurance may be a result of a lack of confidence or understanding in both cyber policies/insurance companies and their internal security capabilities.
So, what does the relationship between your organization and a cyber insurance company look like, and what can you do to ensure that you’re getting the most out of the combination of your security practices and insurance?
What to Expect from a Cyber Insurance Provider
Look, insurance companies are businesses too. While they are meant to aid businesses, there needs to be a positive outcome for them too. If they’re consistently paying off the results of compromises of their covered companies, they’re not going to make money.
Because of this, you can expect some vetting of your network environment and your security practices. There are three things most cyber insurers will look at.
Non-Invasive Assessments
These assessments look at fundamental controls, technologies, and practices that make an immediate impact in reducing the chances of compromise against your environment:
- Port and vulnerability scanning
- Exposed credential checks
- SSL credential validation
- Certain control checks
- Secure-email gateway
- DDoS protection
Cyber Risk Quantification
Cyber risk quantification looks at certain categories of security concerns and then evaluates the potential financial damage they would do to the insured organization. This evaluation includes “Estimated Aggregated (Max) Loss” and “Estimated Probably Loss.”
- A data breach
- Ransomware
- Distributed Denial of Service (DDoS)
- Etc.
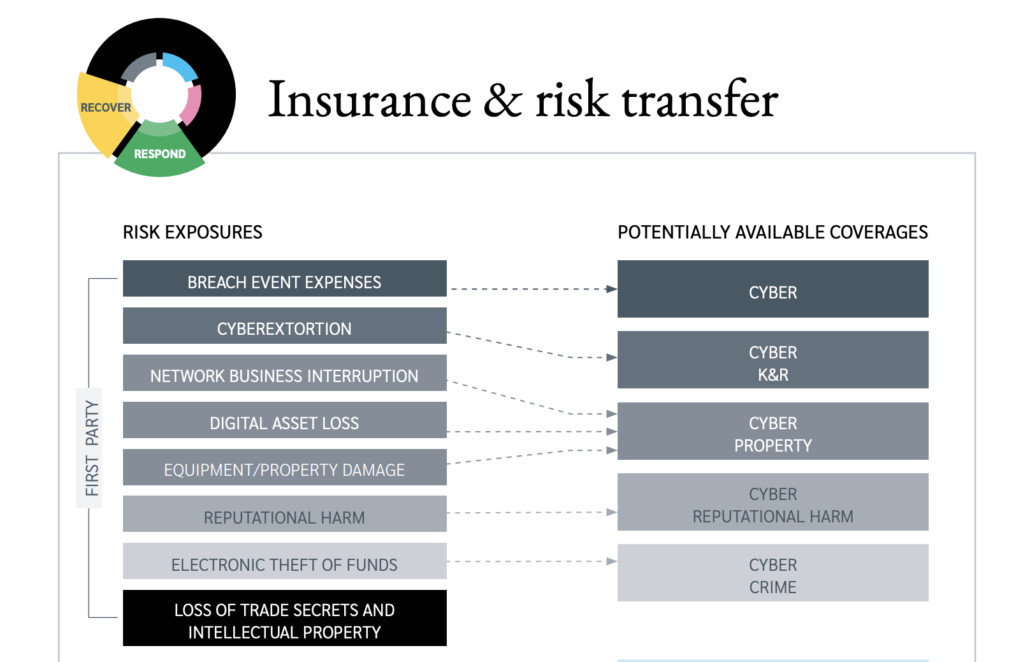
Benchmarking
In part, insurance policy costs are determined by trends in the activity of the policyholders. You likely saw an example of this with your health insurance this year.
Because of the Covid-19 pandemic, more people needed hospitals, pharmacies, mental health services, etc. in 2020. This led to increased medical costs among policyholders, insurance companies paying more as a result, and more expensive plans in 2021. But the reverse would also be true. Had medical spending been trending down significantly, policies would have likely decreased in cost to match.
Cyber insurance is not dissimilar.
In conducting the non-invasive assessments mentioned previously, cyber insurers can quantify the risk that their potential policyholders pose in relation to like organizations.
Essentially—if your organization is less likely to suffer a loss (or would lose less) in the event of a major incident compared to companies like yours, insurance companies will look more favorably upon you. You’ll be more likely to get coverage, and the cost will be less.
What Should We Expect Moving Forward?
Now that you understand how cyber insurance providers determine coverage, let’s look ahead to what the industry is trending towards and how you can prepare your organization.
A Shift into Must-Have Controls
We discussed the types of assessments that cyber insurance providers will administer to determine favorability for coverage. As the policies and the organizations providing them mature alongside the current state of the information security industry, the required controls are going to follow suit.
Some of the must-have controls organizations should implement to improve their insurability are:
- Multifactor Authentication—either for all access or for remote or privileged access
- A recent Microsoft study shows that enabling MFA blocks 99.9% of identity-based attacks. In terms of “bang for your buck,” MFA might be the best thing you can implement. Use it on all the systems, applications, and accounts you possibly can.
- Backups—frequent backups and protected backup storage
- Disabled or protected Remote Desktop Protocol (RDP)
- Confirm no end-of-life operating systems are used
- No shared user accounts
- Supplemental questionnaires—be prepared to answer these.
- Ransomware
- Network business interruption
What Organizations Can Do to Prepare
Knowing the above controls and practices are being looked at as required by cyber insurance providers, there are some things your organization can do to prepare and ensure favorability with the providers.
- Implement MFA on every external access point.
- Some insurers will also require this on internal access points.
- Limit the number of admin accounts in your environment.
- Implement third-party risk management. Insurers want to know what you’re doing to vet your vendors.
- Identify deficiencies (read: conduct a risk assessment) and create a plan to address them.
- Questionnaires:
- Never say “no” on questionnaires.
- A no is an automatic knock. Instead, mark “see below” and describe what your organization is currently doing. This puts the onus on the underwriter to determine if it satisfies the requirements—rather than an automatic disqualification.
- Do not expect one person to be able to complete them.
- These questionnaires require a level of information that will require multiple subject matter experts across a variety of internal teams. You’re doing your company a disservice if one person oversees answering the whole thing.
- Never say “no” on questionnaires.
You’ll notice that a lot of these suggestions are synonymous with good foundational security practices. Nailing the fundamentals of security will pay dividends in qualifying for insurance, as well as all other key components of your business.
If We’re Deemed Unfavorable?
We also recognize that the above tasks and practices are not easy to implement. They take time and concerted effort to enact. With that in mind, there’s a chance that your organization is still working on implementing those things. Therefore, your organization may not be favorable to insurance companies today.
What can happen if this is the case?
- Insurance companies may deny your organization cyber insurance.
- The scope of the policy may be limited—excluding or including specific coverage grants
- E.g., you may only be able to get coverage for secure failure or system failure but not both.
- A sublimit may be put on a particular coverage.
- This may only be 10-50% of the total policy limit.
- Your organization may be charged additional premiums.
- E.g., if you don’t qualify for system failure coverage, they may charge you 10-20% to cover the business interruption for it.
The moral of the story—whether you’re looking for complete cyber insurance coverage for your organization or not, it’s important to implement fundamental security practices. Not only will it help you protect information within your business, but it will also improve your chances of being covered under a cyber insurance policy, should you seek to obtain one.
Wrapping Up
Hopefully this article can serve as a resource in understanding how the cyber insurance industry has evolved, what insurers assess when considering covering organizations, what practices can help your case as someone seeking coverage, and what happens if you find yourself in an unfavorable position.
With the assessed practices and controls in mind, recognize that these are important information security and business practices regardless of whether you decide to pursue cyber insurance coverage or not.
And, as always, if you need help implementing those controls or practices within your information security team or business, please don’t hesitate to reach out. We’re happy to help.







