Our team has been BUSY of late responding to calls regarding ransomware. We’ve seen a few success cases but not enough, so I thought it would be useful to review three of the common scenarios we are encountering, what the outcome has typically been and what you can do to prepare and protect yourself from this nasty attack.
But First, What Is Ransomware?
“Ransomware?” you say. “What’s that?” Well, if you are lucky enough to not have been either directly or indirectly affected by ransomware, let me give you a brief rundown:
Ransomware attacks utilize a type of malware (malicious software) that attempts to block access to assets belonging to a victim (i.e. your files) and only unblock in exchange for a ransom payment.
The variant of ransomware running rampant today infects your device and encrypts (or locks) all the files you have access to, making them completely unusable to you unless you get the key to decrypt (or unlock) the files. The malware searches for and encrypts all applicable file types (including Word and Excel documents and PDFs) both on your device and on any shares you are mapped to, meaning the more access your device has, the more damage the malware can do.
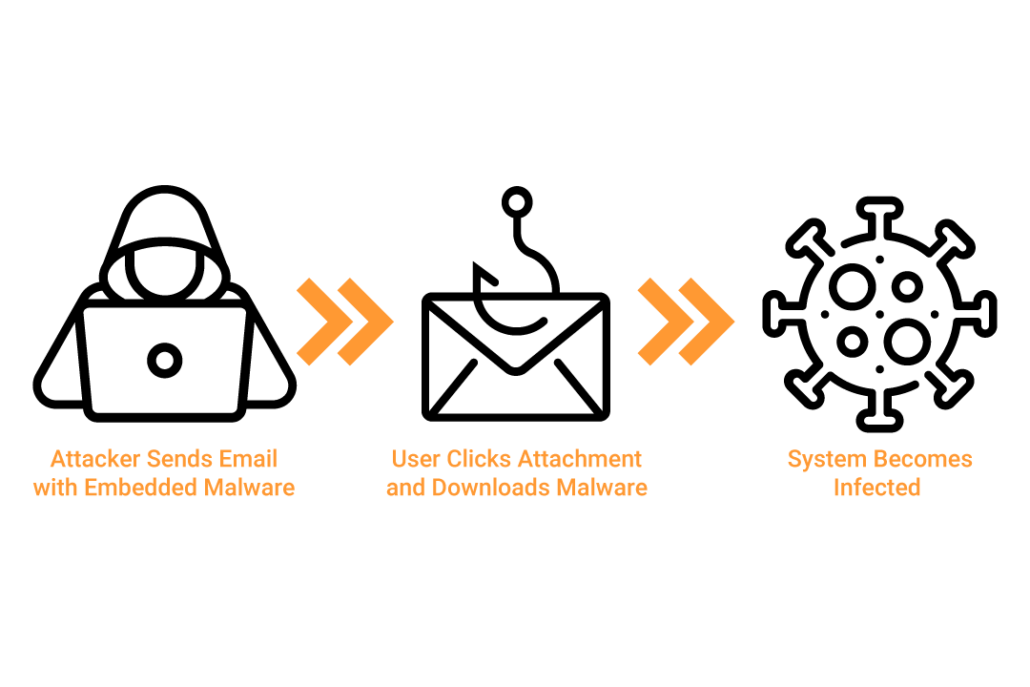
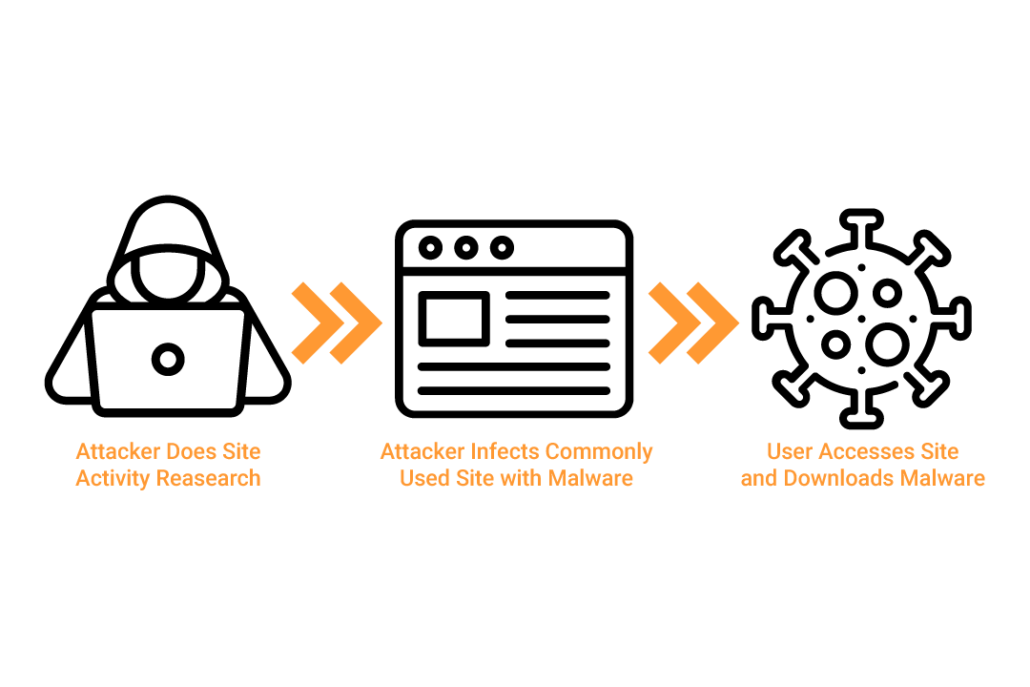
While there are many ways your system can be infected, ransomware is typically delivered through phishing emails or website drive-by-download attack.
Email Phishing
Drive-by-Download
In order to decrypt the files, you have to get the key from the attacker who distributed the malware, which costs money, typically in the form of Bitcoin. Up until recently, the attackers were demanding basically the same amount of ransom regardless of who they infected—typically between $500-1000, but they’ve now discovered that some targets are willing to pay much more and have started demanding ransom payments more proportional to the information they are holding hostage.
What We’re Seeing
I’m lumping the companies we are hearing from, both in the field and from incident response calls, into three broad categories. Read along and see which group your organization most closely aligns with and take away some action items to better prepare yourself!
Company 1: The Not-So-Lucky One
Company 1 calls shortly after getting that gut-wrenching pop-up notifying them about an infected system, unsure of what to do or where to start.
They haven’t really been good about consistently backing up their data so they don’t have a viable backup to restore from.
These are usually painfully quick and unsatisfying conversations. While we always recommend doing some research on the particular malware strain to see if a key has been obtained and shared, odds are, if you don’t have a backup of your data, your only real option to get your data back is to pay up.
For Company 1, this is exactly the outcome and after learning the ins and outs of Bitcoin, they are back up and running, less $500, and working diligently on formalizing their backup strategy.
For the record, we do not support paying the ransom as the best solution to this problem.
Paying only encourages this type of activity to continue to grow and makes you a bigger target for future attacks.
Additionally, we’ve seen many instances where the decryption process and system restore hasn’t gone smoothly and not all files are recovered. However, if there is no other way to get the information that’s been ransomed and it’s necessary for operations then sometimes this is the only solution.
Company 2: The Oh-So-Close-But-Not-Quite One
Company 2 got the same pop-up notification with ransom-payment instructions, but threw high-fives all around because they’ve got good backups and regularly test them, so they knew that this was but a blip in the road.
They restored the systems they determined to be impacted by the malware from backup and resumed operations as normal—until they got a call from a user freaking out because their data was no longer usable.
Turns out there was a small subset of the organization that was supposed to be segmented off (but wasn’t) and for all intents and purposes was thought to be no longer in use (but was) so the share wasn’t being backed up regularly. And the data stored on this share was pretty important.
So, while Company 2 was able to successfully restore most of their files from backup, because they didn’t have an updated inventory of their data resources, they still ended up paying a ransom to get the files from the not-so-segmented share back.
And now they are focused on a top-to-bottom user access review and data mapping exercise to make sure they know where all their data lives and who has (and who should have) access to it.
Company 3: The Ready-For-Your-Stupid-Virus One
Company 3 called in advance of getting the ubiquitous pop-up. They noticed some files they were working on were changing, becoming inaccessible and suspected they might be in process of being infected by ransomware. With a little digging we were able to confirm their suspicions and set about containing the malware.

The one nice thing about ransomware is that it’s pretty easy to determine where the attack started because the device where the infection initiated will be the device that provides the notification and instructions on how to pay up.
But, on the flip side, once the pop-up shows up, it’s too late to contain the malware. So, you have to do some work while it’s in process of spreading to find the source and contain in.
For Company 3, there was some suspicion around a particular attachment and a particular user (based on internal conversations and where the file changes were taking place) so it was relatively easy to pinpoint the source. With that knowledge, we were able to isolate the system (disconnect it from the network and internet) and work on replacing the infected files.
Company 3 not only had replication of data to the cloud but also maintained regular offsite backups.
The data being replicated in the cloud had already uploaded the encrypted versions of the files so we had to pinpoint when the ransomware was downloaded so we could revert back to the clean files, but after about four hours, Company 3 was back up and running with no ransom paid.
Even so, Company 3 is not resting on their laurels, they used this close call to conduct additional user training on the perils of email and phishing attacks.
How To Protect Against Ransomware
One thing I like to point out when talking about ransomware is that this virus does not discriminate.
It will hit you at home and take your $500 just as readily as it will at the office.
So, my advice is advice that can be implemented in both environments and should be strongly considered if you place any value on the personal information residing on whatever device you use (PC, Mac, smartphone, tablet… all devices are fair game for this bugger).
What You Can Do:
- Inventory your data
- This is Information Security 101, but we aren’t generally that great about it. Do you know where all of your information is stored? Map out all of your data repositories and then audit regularly to make sure it’s still appropriate.
- Back it up
- This is your best defense against ransomware. Determine how long is acceptable for you to be out of commission (1 hour, 1 day, 1 week?) and build out an appropriate backup strategy that ensures you can meet that acceptable level. Consider multiple types of backups in the event one gets compromised and regularly test the effectiveness of the backups.
- Side note: many versions of the ransomware either destroy your shadow copy or encrypt it before notifying you that you’ve been ransomed so do not let your shadow copy be your only backup solution.
- Implement need-to-know access
- Do you know, with certainty, who has access to what information? Or do you take a “everyone needs access to everything” approach? Play out a few table top exercises with ransomware and you may be re-thinking that approach. Use user access to data as a strategy to protect you from attacks to limit the exposure to information impacted from any one user. And like data inventory, review this access periodically and audit users to ensure nothing is changing.
- Continue to train users
- Make sure your user base knows what the current risks are to them so they are better able to protect both themselves and your organization. Train them on the signs of ransomware so they can report it before the pop-up does, which can help mitigate the damage done. Remember that your users are computing at home so they have a vested interested in being a bit more technical – teach them about disconnecting from the internet, unplugging from the network, and the importance of controlling access to information.
- Strengthen technical controls
- There are some pretty easy solutions that you can implement that can help protect you from installing ransomware, including:
- Block EXE file attachments so users cannot directly run executable files from emails.
- Disable macros in Office applications, where malicious code is often embedded.
- Implement web filtering for malicious sites to block known security risks sites.
- Remove local admin rights so users are forced to enter in a privileged username and password to run new software.
- Develop and implement a patch and vulnerability management program; many variants use vulnerabilities in applications to infiltrate your system.
- Implement group policies and other restrictions on common payload entry points, such as the %AppData% folder.
- There are some pretty easy solutions that you can implement that can help protect you from installing ransomware, including:
- Check online for solutions
- If you don’t have a good backup to restore from, before you give in and pay the ransom, do some research to see if a key has been uncovered. Great sources to consider include Malwarebytes, Kaspersky Ransomware Decryptor, and BleepingComputer.
- Do not remove the malware until you are sure all of your files have been successfully recovered.
There’s no doubt about it, ransomware stinks. But it is a good reminder of how a strong information security program can protect you and how sticking to the basics (asset management, access control, backup management, user training) will continue to pay off.
As always, we welcome any questions or comments and are at the ready to help your organization continue to build and protect your information. Keep fighting the good infosec fight!