One of the most powerful pieces of technology many of us own is our cell phone. Once only a device for placing a call from anywhere, phones today are capable of almost anything a desktop computer can do. This can be empowering, but it can also make you vulnerable.
It can be hard to know how to secure your phone or how to look for signs that someone may be using it against you. When someone with malicious intent gets hold of your device, here are some tips for how to tell if your phone is hacked.
Quick Tip: You can close out of this browser window quickly by hitting Alt+F4 on a PC or Command+Option+Esc on a Mac.
Your Mobile Phone Basics
Before we can get into the specifics of how your phone can be hijacked, you need to know some basics of how it works and what it does. Your phone is capable of quite a bit that you may not be aware of and therefore would never think to check.
Permissions
You have likely seen requests for permissions on your phone before. When you download and install a new app from the Appstore or Google Play, the app will ask you if it can use certain parts of your phone. These include access to things like your contacts, your microphone or camera, and your location.
There are limitations you can place on apps if you do not want to allow those permissions. You can also elect not to use an app if its required permissions are too intrusive for your comfort.
It is important to be aware of what permissions which apps currently have and make sure that you were the one who allowed those permissions. To view which apps have which permissions, follow these instructions for an Apple device and these instructions for an Android device. From there, you can also revoke any permissions that you did not intend to allow.
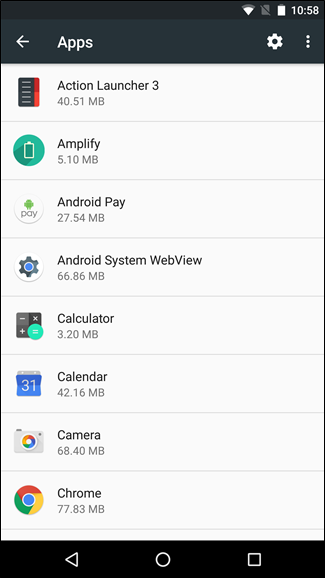
Standard Apps
It’s important to know what apps you have installed on your phone; this helps with both updating permissions and catching apps you didn’t install (as long as they aren’t hidden—more about that next). While you can see most of your apps on your home screen or in the folders you would normally use, there is a better way to view them.
Your phone will have a list of all installed apps and their permissions in your settings, which you may have already accessed if you’re following along. This will give you a full picture of your installed apps all in one place, and if you see any you don’t remember installing, no longer use, or don’t want anymore, uninstall them.
Note: there may be a lot of installed apps in this list that you do not recognize. Although it can, this does not necessarily mean that your device has been compromised. All new phones come with a certain set of pre-loaded apps. Some run in the background to make your phone run smoother, and some are games or other apps that sponsors paid to have installed on new devices. When in doubt, search the application in either Google (or your search engine of choice) or in your app store.
Here is how to access your apps list via settings on an Android phone (scroll about 75% down the page to the “Managing Your Applications from the Apps Settings Screen” section). For iPhone users, this information will be helpful.
Hidden Apps
Now you know how to access your apps on your phone. However, it is possible for installed apps to be hidden from that view. If someone had access to your phone, they could easily install a hidden app—much the same as you would install a legitimate one.
These hidden apps may not show up in your normal app list at all, or they may have names that do not match their function. Often, these apps are named innocuous things like “Calculator.”
The purposes of these hidden apps are numerous. Depending on the app and permissions, it may be used to track your location. It also could listen in on your conversations, view your text messages, or spy on your browser activity. They are sometimes called spy apps.
Unfortunately, you may have no obvious indicators that a hidden app is installed on your phone. Fortunately, you can check. For iPhone users, use this guide. Android users can use this one.
Privacy and Preventing Unwanted Access and Use
All smartphones are capable of some basic security features. Taking the time to familiarize yourself with and enable these features can help you keep your phone private. It may feel daunting at first, but once you get the hang of these fundamentals, you will hopefully have much greater peace of mind.
Note: If you want a deeper dive than what we cover here, Apple has a comprehensive privacy controls document here. There is not a comparable official document for Android because the devices vary, but ComputerWorld put together this useful guide.
Passcodes and Patterns
One of the simplest and easiest ways to secure your device is to add a passcode or pattern to unlock it. This can be a number, usually 4-6 digits, or a pattern you draw.
These features themselves also often have different levels within them. For example, if you select a pattern to unlock, you can set your device to hide the pattern as you’re drawing it. This prevents anyone from spying over your shoulder and easily learning your pattern.

To set up a passcode or pattern, Apple users can use this guide, and Android users can use this one.
Once you get the basics of how to set up a passcode or pattern, play around with the related settings to access the more complex features.
Biometrics
A step up in security from a standard passcode or pattern, many phones can use biometrics to unlock them. This includes both fingerprint scanning and facial recognition. There are pros and cons to both passcodes/patterns and biometrics.
One reason you may prefer biometrics is that you can give someone else access to your device if you choose to, but you don’t have to share a code that would let anyone in.
For example, if you wanted to let your child play games on your phone, you could program in their fingerprint or face. But, they wouldn’t be able to give anyone else access unless that person was physically present with the child.
You can access the biometric unlock settings from the same place you would set up a passcode or pattern–those instructions are linked in the section above.
Secure Folders and Other Hiding Places
A lesser-known feature for phones, the secure folder and other ways to hide data and apps can be useful. If you have photos or files that you do not want anyone else to see, this feature may help. A secure folder allows you to put files and apps you don’t want prying eyes (or anyone else with access to your phone) to see.
Note: Samsung’s secure folder has more options and is more versatile than Apple’s; with Samsung, you can put photos, videos, apps, and other files in your secure folder. With Apple, you’re a little more limited.
You can find more information on Samsung’s secure folder here. If you have an iPhone, use this guide.
Private Browsing on Mobile
As we explained in the first part of this series, private browsing is possible on your phone. This means that your web activity will not be tracked in your history, nor will it be tied to your account (unless you sign into your account while in private browsing mode). All of the major mobile browsers, including Chrome and Safari, allow for this option.
You can find resources for whatever browser you’re using on your phone, but here are guides for Android (Chrome) users and iPhone users.
Note: while your browser itself will not retain any information about the sites you visit, if you are connected to WiFi, a tech-savvy user will still be able to see which sites you visit. To avoid this, switch off WiFi during your private browsing session and use your cell network (data coverage) instead.
Conclusion
There are unfortunately many ways that a person with access to your phone could use it against you. The good news is that there are ways to detect malicious use and ways to guard yourself against further misuse of your mobile technology. There are also tons of free resources online that can help you learn about the capabilities of your phone. When in doubt, contact your cell phone carrier (Verizon, T-Mobile, AT&T, etc.) and set up a meeting with them to learn more about your device.
This post is part of a series. The first post covered the basics of digital abuse. If you haven’t yet, we highly recommend you check it out.
In future posts, we will share tips for financial data security, home and physical security, and other information for empowering you to keep yourself secure. Let us know if there is something specific you want to know, and we’ll talk about that, too.
If you want to join a group of supportive folks chatting, check out our CEO Evan Francen’s daily inSANITY check-in meetings.







