I have to tell you about my friend – we will call her “Jane.” She writes down passwords on a yellow piece of sticky note paper, and has that paper stuck up on her monitor for easy reference. The passwords for the sites and services she uses are the same or very similar:
- TwinsWin2011
- Twins2012
- Vikings2013
- Timberwolves2014!
On one site that appears to force Jane to change her password quarterly, the password history is written out chronologically:
- 09/13: fall2013!
- 12/13: winter2013!
- 3/14: spring2014!
- 6/14: (can you guess what the password was changed to?)
As you might be thinking, there are several dangers in the way Jane is handling her passwords. First of all, writing passwords down is a risky practice. If a coworker, the building cleaning crew, or any casual observer was to catch a glance of those passwords, Jane’s accounts could be at high risk. Secondly, Jane is using a fairly predictable – and easily guessable – password scheme. These weaknesses make Jane a pretty easy target if a malicious user wanted to break into her accounts. Even worse, if a site Jane used was susceptible to the Heartbleed bug and someone retrieved the password she uses on it, it is a pretty safe bet that Jane uses that same password elsewhere.
Password123 = not a good password
A general best practice is to use a long, complicated password for every account – and almost more important, use a unique password for each site. However, when most users hear this, they respond with an answer that we at FRSecure hear all too often: “Remembering complicated passwords is too hard!”
The good news is it does not have to be. There are several products and solutions that will store your strong passwords for you securely, yet provide easy access to them when needed. Before choosing one, some important questions need to be considered:
- Do you need to share the passwords with others in your department or company?
- Do you want to store the passwords internally on your servers, or host them in the cloud?
- Does the solution need to work on PCs as well as Macs, mobile devices, other operating systems, etc.?
- Is an open-source (free) or paid solution the right fit?
Finding the right solution should be done slowly and carefully, taking time to evaluate each product in your environment. Also, I recommend giving it a dry run with a subset of users and listen to their feedback. The bottom line is that if the solution is too complicated or confusing, users will give up on it.
Example: managing passwords with LastPass
One tool I use personally to manage passwords is called LastPass (www.lastpass.com). LastPass has a free version, but I have the paid ($12/year) version, which gets me access to the mobile version of the app, multifactor authentication options, and more.
When LastPass installs, it integrates into any Web browsers you currently have on your machine. You will then be prompted to create an account using your email address and a strong password. This is going to be the “master” password to protect the rest of your passwords. Thus, this master password should not be something like Vikings2014, but rather an extremely long combination of upper and lowercase characters, numbers and special characters. To create a truly random password, you can use sites such as GRC’s Perfect Passwords. Or, LastPass has a built-in tool to generate a strong password for you:
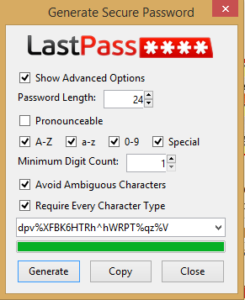
Once your account is setup, you can login to it at any time by clicking the LastPass icon in your browser:
I also use two-factor authentication to better protect my account. Two-factor authentication, also written as 2FA, provides an extra layer of security to your account in addition to your username and password. In this example, I have to provide LastPass with my username and password (something I know) and then also provide a password from my Google Authenticator application (something I have):
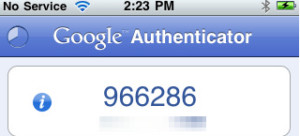
Then, as you browse sites and log into them, LastPass will ask if the provided credentials should be stored in your password vault. Once saved there, you can open the vault at any time and either search for a password you want to use, or click a LastPass entry to automatically open your Web browser and log into it:
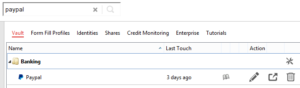
As seen above, passwords can be saved in logical groups for easy reference. Additionally, LastPass has fields to store other important information such as wireless passwords and software licenses. You can even attach files and upload them into the vault.
Once you have all your critical passwords saved in LastPass, one of the best password managers, you can run a security check to see if you have re-used passwords in more than one place, and if any of the sites you log into are vulnerable to Heartbleed or other widespread risks. Additionally, LastPass will check if any sites you use may have been involved in data/account breaches.
This solution also has some sharing features. I’m able to share individual (or all) passwords with my wife for accounts we both use. On the corporate side, LastPass offers an enterprise option to share passwords between groups of users or departments.
To wrap this up, I wanted to share one final note in regards to how LastPass stores information. Their site explains the process in detail, but essentially the LastPass servers only store an encrypted “blob” of your password vault information. This means that the master password you create is never sent across the Internet. And presumably, if someone were to hack the LastPass service and download the user password vaults, the data would be essentially useless. Check out this Lifehacker article to see this specific question answered in more detail.
Conclusion
Until someone comes up with a better option, passwords are the bread and butter of securing online accounts. These passwords need to be long, strong, and unique for each and every site you use. The argument of passwords being too hard to remember is not a valid one. Not only that, but using weak passwords – or reusing them – makes it all the more simple for an attacker to pilfer sensitive company or financial data from right under your nose.
If you have questions about password management, I would welcome the chance to talk with you. I can be reached at 952-467-6385 or at .
Coming up next
In October, we will talk about a particularly spooky topic: online privacy. Yes, your boss can really read some of your email and sites you’re visiting. And your Internet Service Provider? Yep, they can see just about everything you do too. So how can you get back some of your privacy?
In November, we will discuss patching as it relates to your workstations, servers, and network equipment. Yes, it will get a bit geeky, but I’ll make sure the topics are covered in a way that’s easy to digest.






