In a world that has abruptly turned uncertain, chaotic, and fearsome, the world of data security remains constant. Despite the COVID-19 virus wreaking havoc on the service industry, entertainment businesses, and the stock market, many businesses in today’s technological age have the flexibility to remain open despite literally closing their physical doors.
As long as businesses remain open, attackers will continue to find ways to exploit them, especially in this heightened state of confusion and atypical working conditions.
So, data security must stay top of mind. Businesses must continue to plan, act, guide, enforce, and train as their workforce landscape changes—and as the landscape of the world changes with the virus.
The good news is that strong security practices remain constant, too. If you know the important assets that exist in your business, the likelihood of those assets being compromised, and the risk associated with the assets going down, you’re well on your way to knowing how to secure them.
Amidst the unforeseen circumstances surrounding this global pandemic, calm is key. The organizations that continue to protect their data (and the people behind that data) despite the chaos will be the ones who continue doing the fundamentals well and modify their plans as the environments change.
There are three main things you should consider as this COVID-19 pandemic rages on.
1. Remote Worker Security
Obviously, as the United States and other parts of the world continue social distancing and businesses send their employees home for weeks at a time, the assets within your environment will change while you continue operations. The ways that you protect those assets will need to be modified as well.
Especially if your employees are not traditionally allowed to work remotely, there are measures you should take to ensure your business’s information stays secure.
Policies and Procedures
It first goes back to the fundamentals.
Do your employees know what office policies extend into the walls of their home? Have you adjusted your policies and procedures to account for situations that are unique to your employees working remotely?
General Network Practices
First and foremost, opening up your network to remote work means you are opening it to your employees’ home networks. It’s critical that you provide guidance to your employees on how to properly secure their home network. This includes changing default configurations, updating software regularly, running antivirus, having a guest network, connecting IoT devices to a separate network, and much, much more.
While those suggestions tend to be common sense for most businesses and their IT or security team, some guidance is less obvious.
Paper Record and Printing
Paper records contain sensitive information the same way your server does. Offices are usually pretty good at designating storage options and requiring proper disposal, but what does that look like at your employees’ homes?

Improper storage and disposal of paper records could be exposing extremely sensitive data to those who definitely should not have it. And before you discredit the chances of that, know that it does happen. We’ve found sensitive information on paper records thrown in dumpsters in our engagements before.
Ensure you have a plan for printing, paper storage, and paper disposal while your employees are remote, and ensure that it’s communicated to everyone.
Social Media
Social media is an aspect of security that is often overlooked. Posting on social media can pose security threats, and traditionally speaking, employees have a tendency to loosen up when they’re at home.
It’s necessary to remind your employees what the policies are around posting about the company on social media and reinforce good social media habits. Things like privacy settings, what is in the photos posted (nothing like a “my new office for the time being #socialdistancing” Instagram post with their computer screen in it—who knows what information someone could zoom in and see), and how your employees mention and talk about the company in times of hardship could all have lasting impacts on the business.
Because it’ll be harder to enforce while your employees are home, make sure they know the guidelines early and that you know how to communicate those guidelines.
Acceptable Use
Psychologically, we’re more relaxed at home. It’s the most consistent place for employees to wind down, and the brain doesn’t just shake that now that we’re suddenly working from home.
Because of the comfortability factor and the physical separation from authority figures, the chances that employees let their guard down increases. Again, it’s vital that your business leaders communicate rules early on so that this doesn’t negatively impact the organization.
It’s not uncommon for employees to use workstations for personal purposes at the office, but that personal use may spike when employees are home. Ensure your employees understand what is acceptable for them to access on their company-provided workstation, and, regardless of convenience, discourage employees from letting other members of the household use their devices.
Again, providing employees with policies, procedures, and guidelines early (better yet, ahead of time) will limit the amount of people-related security concerns.
Clearly, there are more than just people-related vulnerabilities, though.
Tech
With a remote workforce, technology can be your best friend or your worst enemy.
We want to be able to use technology that exists to make our workforce more secure when they work from home. There are a few key considerations that can help us do so.

Virtual Private Network (VPN)
A virtual private network (VPN) will allow your employees to connect to their home internet connection from their work devices, but it will mask the internet protocol (IP) address. This creates a secure and encrypted connection that will help protect information.
VPNs are used frequently when connecting to public Wi-Fi like those at airports, coffee shops, etc., but can also be an easy solution for secure remote work for your employees.
Don’t Stop There
Split Tunneling
It’s common for companies that use VPNs to split tunnel. What is split tunneling?
Split tunneling allows a remote employee to access the internet directly while being on the VPN at the same time. While organizations like Microsoft actually recommend this, doing so can pose a serious security concern.
The reason for this is that you’re hair-pinning your network and the employee’s. All their web traffic would go through their internet connection, and you don’t know what they’re going to.
The controls you have at the office, the web filtering you may have, and the IPS/IDS you may have on your internet connection are almost certainly not what your employee has on their home network. If you split tunnel, you’re opening new connections into the heart of your sensitive information multiplied by all the remote employees that are connecting.
If you can force the internet traffic through your controls, your IPS/IDS, and your firewall, that’s likely the most secure way to go about it—especially considering most technical attacks originate through the internet.
Multifactor Authentication (MFA)
If you have a VPN that doesn’t have multifactor authentication enabled, turn it on. If you don’t have a VPN that supports multifactor authentication, you shouldn’t trust that VPN anyway.
Effectively a confirmation step after logging in, multifactor authentication forces a user to prove their identity with a second step. This is often a text message with a code to the account’s phone number, a code sent to the email address on the account, or a third-party code-generating app like LastPass or Google Authenticator.

This is important because if an attacker does get a username and password combo correct on the VPN, they (in theory) wouldn’t have access to the confirmation method. We’re not often without our phones these days.
Double Down on MFA
Don’t stop at your VPN. As we mentioned, most of the attacks on networks and devices stem from the internet.
For that reason, every system you access should have MFA enabled.
Now, admittedly, not every platform or web app is going to have MFA available. We strongly recommend that you consider multifactor authentication a requirement when you go through the process of selecting your vendors and platforms. If nothing else, at least ensure any programs you do use have MFA enabled when possible.
These tools and tips will certainly help you as you move your employees remote during this outbreak, but it takes more than policies and technology.
2. Recognizing COVID-19 Phishing Scams
It’s no secret that we’re collectively in a state of uncertainty around the globe. It’s hard to focus on what’s going on immediately around us as we continue to see this all shake out. It’s also no secret that because of our lack of focus, black hat hackers (those are the bad guys) will utilize this time to strike.
Be a Barracuda and Not a Bass
Our information security awareness cannot wane. The second we stop being vigilant to scams is the second we open ourselves up to our sensitive data and money being commandeered.
As our attentiveness to attacks declines with the COVID-19 virus at the forefront of our brain, the attacks will increase.
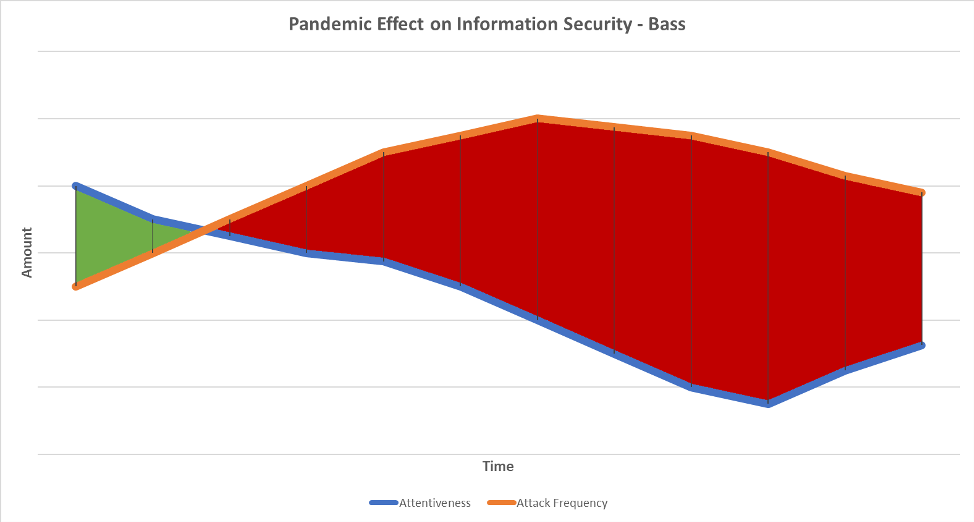
If we continue to remain vigilant and attentive to potential scams and attacks, we decrease the chances of compromise.
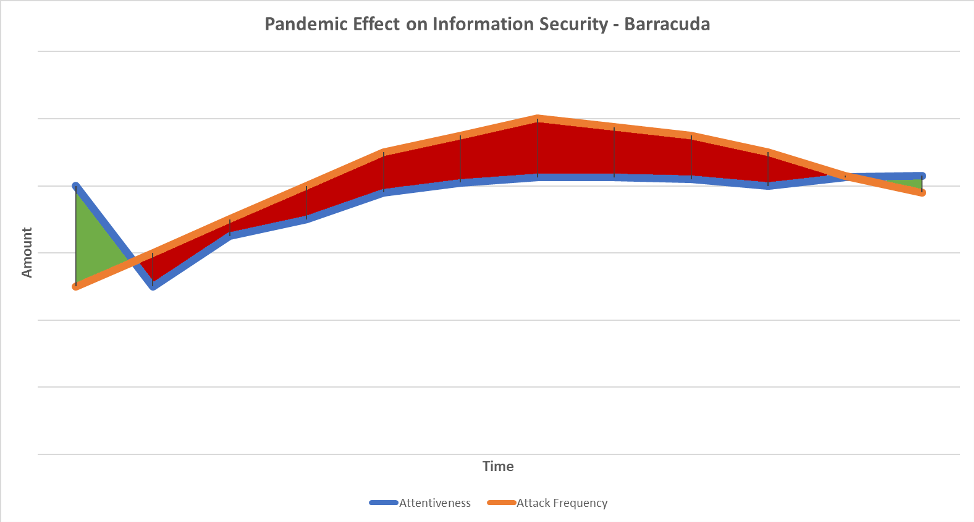
One of the best ways to stay attentive is to understand what common scams are out there. That way, you increase your odds of recognizing a scam before falling prey to it and doling out sensitive information.
Here are some common scams we’ve seen using the pandemic as a way to compromise information.
Mobile Tracking App
Are you an Android user? If so, look out for this one.
An app called CovidLock posed as a real-time outbreak tracker with a map of all the known cases in the United States. Armed with ransomware, users that download the app receive a ransomware note suggesting it’ll erase your contacts, pictures, and videos, as well as your phone’s memory if $100 in bitcoin is not sent within 48 hours.
If you’re looking to actually track the outbreak cases, Johns Hopkins has a useful tool.
Moral of the story: be sure to research and vet the legitimacy of apps before you download them.
Email Scams
There are very few sources that people trust regarding the COVID-19 virus during this time of uncertainty. One of those happens to be the Center for Disease Control and Prevention (CDC).
So, naturally and unfortunately, attackers are going to use that to their advantage.
Health officials have shared that they’ve seen email scams where attackers pretend to be the CDC and ask recipients to go to a malware-deploying link posing as something urgent about the virus, infection control, public health, etc.
One of the first scams discovered pertaining to the virus involved a malicious Word document that hid behind a facade of prevention measures for the disease.
Commonly, these scams rely on urgency. They pose as something critically important and implore you to take immediate action. That quick, emotional response often is enough to get a recipient to let their guard down.
As you receive emails pertaining to the outbreak, check to make sure the sender is legitimate and always vet links before opening them.
In-Person Attacks

A Canadian police department published notice that they have been seeing people scamming residents by going door-to-door and posing as healthcare officials providing COVID-19 testing for a fee.
Again, preying on emotion and urgency, this scam (and those like it) are often attempts to gain access to your financial accounts.
Stop and think before providing your bank account, identification, or other sensitive information to strangers coming to your door and report any suspicious activity you see to your local authorities.
More Scams
The Federal Trade Commission (FTC) usually does a good job at reporting known scams.
Consider checking there if you’ve identified something you think may be fishy. The scams above are not all-encompassing, and things will continue evolve as the days go on. It’s important to have a resource you can look to.
3. Disaster Recovery Planning and Incident Response
Despite our best efforts to know common scams and how to avoid them, compromise can still happen. In fact, data loss often occurs in ways you wouldn’t expect. Ultimately, organizations need to have a plan in place for when this loss happens. Prepare for the worst, hope for the best.
What would happen if you could never get into your server room again?
Imagine if you were suddenly unable to access all of the data in your organization. We’ve posed that question many times to potential clients—not to scare them, but to get them thinking about what is possible. Most of them shared they’d probably have to close shop for good if all of their data was suddenly gone.
A disaster recovery plan is not atypical for established organizations, but it must include data and security planning or else it’s useless.
Communication
The landscape of our workforce is changing. If your company has already shifted to remote work, your employees won’t be able to just walk up to someone and ask for help. Alternate forms of communication must be established.
In case of an outage, this contingency plan needs to be done immediately.
An example of this could be equipping all employees with a local record of company contact phone numbers they can text or call when needed.
Communication is especially important as pandemic-related incidents escalate.
Incident Response, Business Continuity, and Disaster Recovery Planning
Hopefully you have an incident response plan in place, and hopefully it’s been practiced. It may be more likely to be to used given everything going on with this pandemic.
Incident response plans, business continuity plans, and disaster recovery plans are necessary for our industry. Knowing threats are out there and exacerbated in our current state, we need to prepare for them. Each business needs to know who is going to be involved, know what activities each person will be responsible for, know what kinds of backups are needed (technology, physical locations), and understand who externally they might need to elicit for help to get them back up and running ASAP if something were to happen.

The last thing businesses want is to do is wait until something happens. Prepare the plan preemptively, and consistently adjust it now that the environment is in a constant state of change.
Some major things to think about when working through the data side of your response plan are:
- Understand your insurance policy
- Someone needs to review it, and you need to know what’s covered and what isn’t.
- Define roles
- Assign tasks to people so they know what their responsibilities are.
- Include less obvious resources like external providers, public relations, and legal.
- Practice your plan
- You can’t know it works if you don’t test it.
- Continue to be proactive about security
- Annual risk assessments should be conducted, and you should at least have done a vulnerability scan.
- Understand how to classify incidents and what the proper response
based on classification is.
- What is it?
- What systems and assets does it affect?
- What legal requirements will we have to comply with?
- Just because your team is good at IT doesn’t mean they’re good at handling security incidents. Know when to ask for help and who to go to.
Finally, make sure your employees are aware of the scams we discussed earlier. With the rise of these and other scams, it’s important for your staff to know that incident reporting is the same at home as it is in the office. Remind your team that if a scam is detected or something seems off on their devices, it’s vital that they report it to the internal security team ASAP.
Staying attentive and sticking to our security plans will go a long way in mitigating the risk stemming from these virus-related threats.
Wrapping Up
There are three main things you should consider as this COVID-19 pandemic continues. Many workforces are moving to remote work, and new scams are concocted daily.
Focus on the security between your remote workers and your internal systems by running VPNs, MFA, and updating and/or vocalizing your policies and procedures around remote work.
Remind your employees to stay vigilant and attentive to the types of scams (in-person, email, and mobile app) we’ve seen stemming from the COVID-19 outbreak, and ensure they know what to do when they see one.
Finally, ensure that you have a disaster recovery plan, a business continuity plan, and an incident response plan that align with the changing environments we’ve seen throughout this pandemic. It’s incredibly important to have a way to bring logic and actionable steps into an otherwise emotional situation. Vet and practice those plans as things change in the world and as the plans are updated.
The world is an uncertain place right now, but it remains imperative that we protect information so that businesses and—more importantly—the people behind that information remain safe.
If you have any information security needs during this time, we are here for you. Don’t hesitate to reach out at frsecure.com/contact.







One of the best ways for stopping such occurrences is by making policies in your organization about the usage of internet while working. Also, businesses should also think about making sure that their employees are using the devices provided by the company and are updated regularly for the security purposes. It is tough to keep the security tight during this pandemic but one can define policies that can really help in keeping the business safe and secure.