Incident Response Plan Template
Incident Response Plan Template
Download your free copy now
Failing to prepare is preparing to fail.
With the world’s current state of connectivity and the sophistication of attackers, a cybersecurity incident is inevitable. Therefore, it’s no longer acceptable to only take preventative measures to our security—we need to know what to do when those fail us.
A thorough, trained, and tested incident response plan is the cornerstone. Without a plan in place, decision-making becomes easily muddled.
Many organizations struggle to create thorough plans, so we’ve templated an example version of what we provide to customers of our incident response services—no strings attached.
Free Resource
Download our free example Incident Response Plan Template now.
DOWNLOAD TEMPLATESample of Content
Incident Response Plan Template
The (Company) Incident Response Plan has been developed to provide direction and focus to the handling of information security incidents that adversely affect (Company) Information Resources. The (Company) Incident Management Plan applies to any person or entity charged by the (Company) Incident Response Commander with a response to information security-related incidents at the organization, and specifically those incidents that affect (Company) Information Resources.
The purpose of the Incident Management Plan is to allow (Company) to respond quickly and appropriately to information security incidents.
Event Definition
Any observable occurrence in a system, network, environment, process, workflow, or personnel. Events may or may not be negative in nature.
Adverse Events Definition
Events with a negative consequence. This plan only applies to adverse events that are computer security related, not those caused by natural disasters, power failures, etc.
Incident Definition
A violation or imminent threat of violation of computer security policies, acceptable use policies, or standard security practices that jeopardizes the confidentiality, integrity, or availability of information resources or operations. A security incident may have one or more of the following characteristics:
- Violation of an explicit or implied (Company) security policy
- Attempts to gain unauthorized access to a (Company) Information Resource
- Denial of service to a (Company) Information Resource
- Unauthorized use of (Company) Information Resources
- Unauthorized modification of (Company) information
- Loss of (Company) Confidential or Protected information
What's Included
-
SECTION TITLE PAGE NUMBER
-
Version History
-
Introduction 5
-
Contact Information 6
-
Roles and Responsibilities 7
-
Cyber Security Incident Handling Team (IHT) 7
-
Chief Information Officer (CIO/CTO) 7
-
Cyber Security Incident Response Team (CSIRT) 7
-
IR Commander 8
-
Incident Response Team Members 8
-
Recorder 9
-
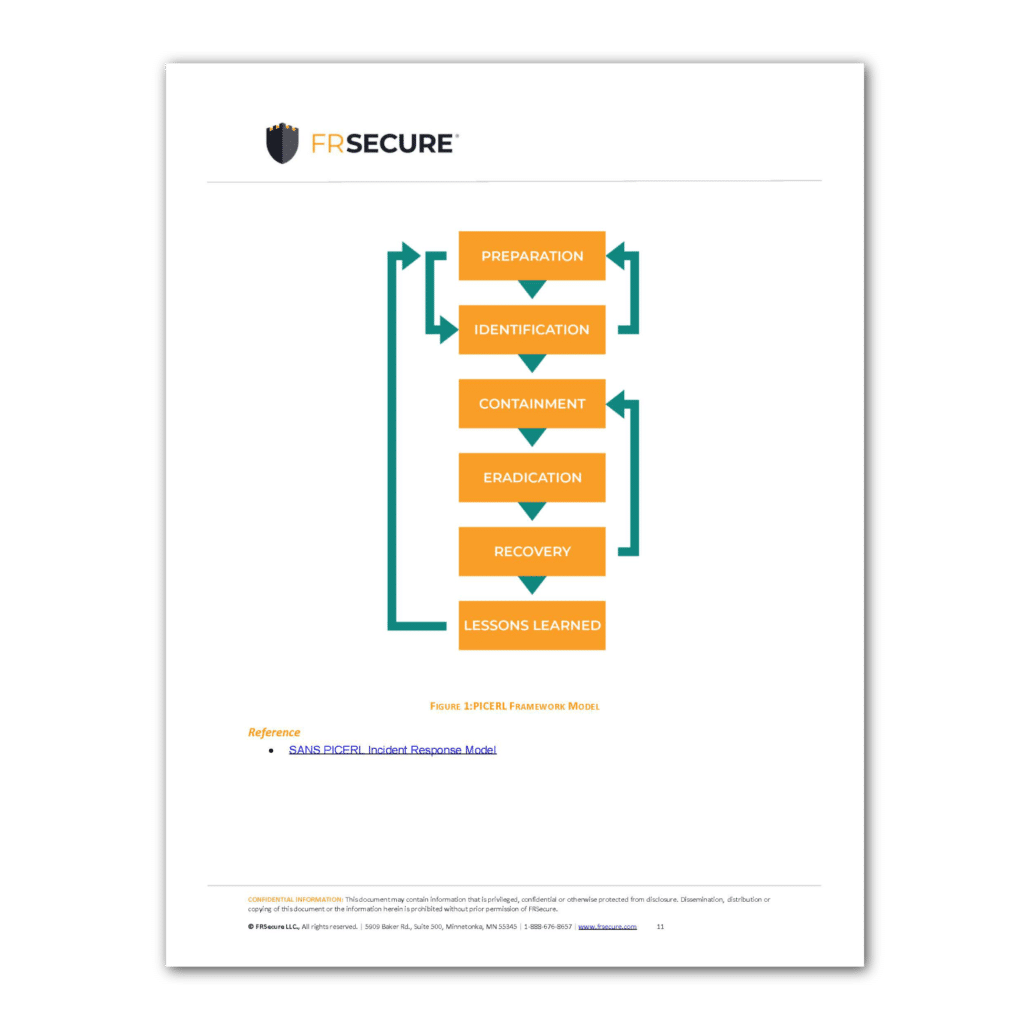
Incident Response Framework 10
-
Phase I – Preparation 10
-
Phase II – Identification and Assessment 10
-
Phase III – Containment and Intelligence 10
-
Phase IV – Eradication 10
-
Phase V – Recovery 10
-
Phase VI – Lessons Learned 11
-
Phase I – Preparation Details 12
-
Reporting Incidents 12
-
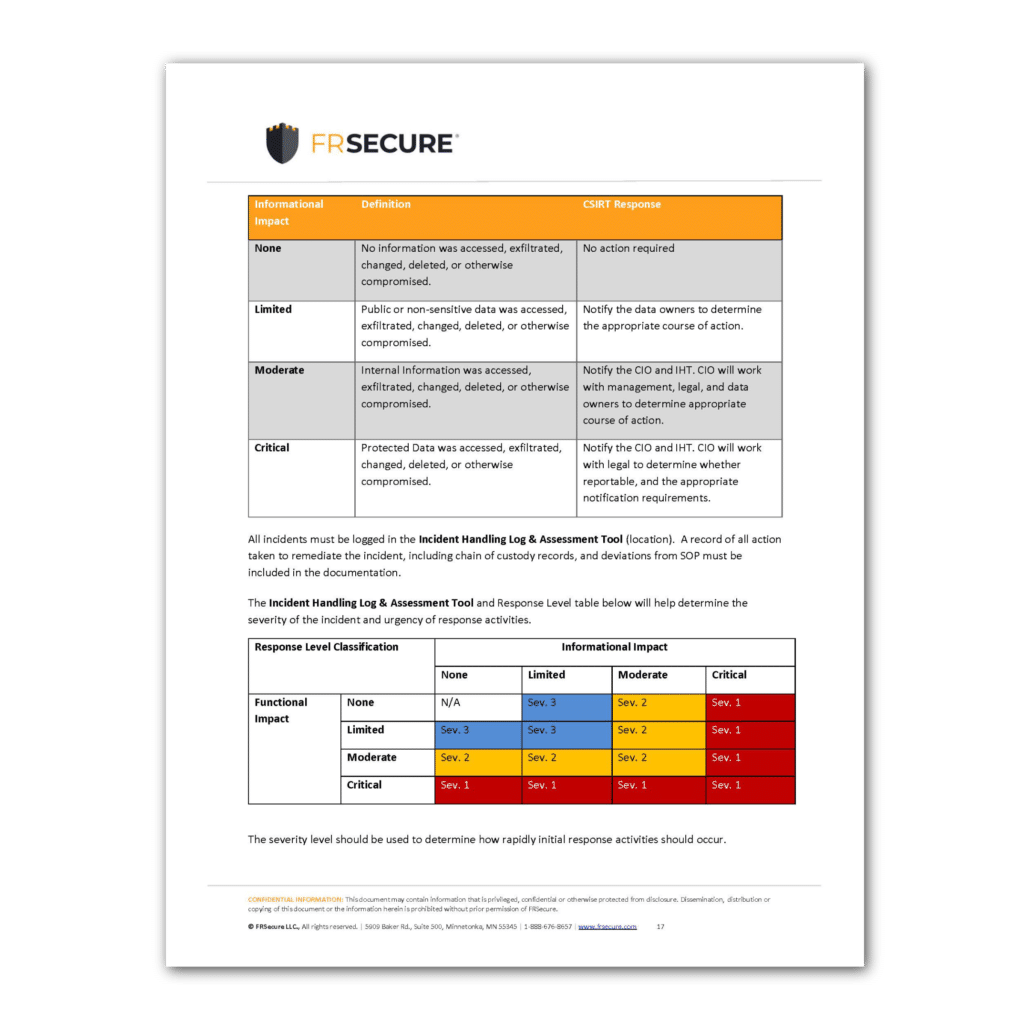
Phase II – Identification and Assessment 13
-
Identification 13
-
Assessment 14
-
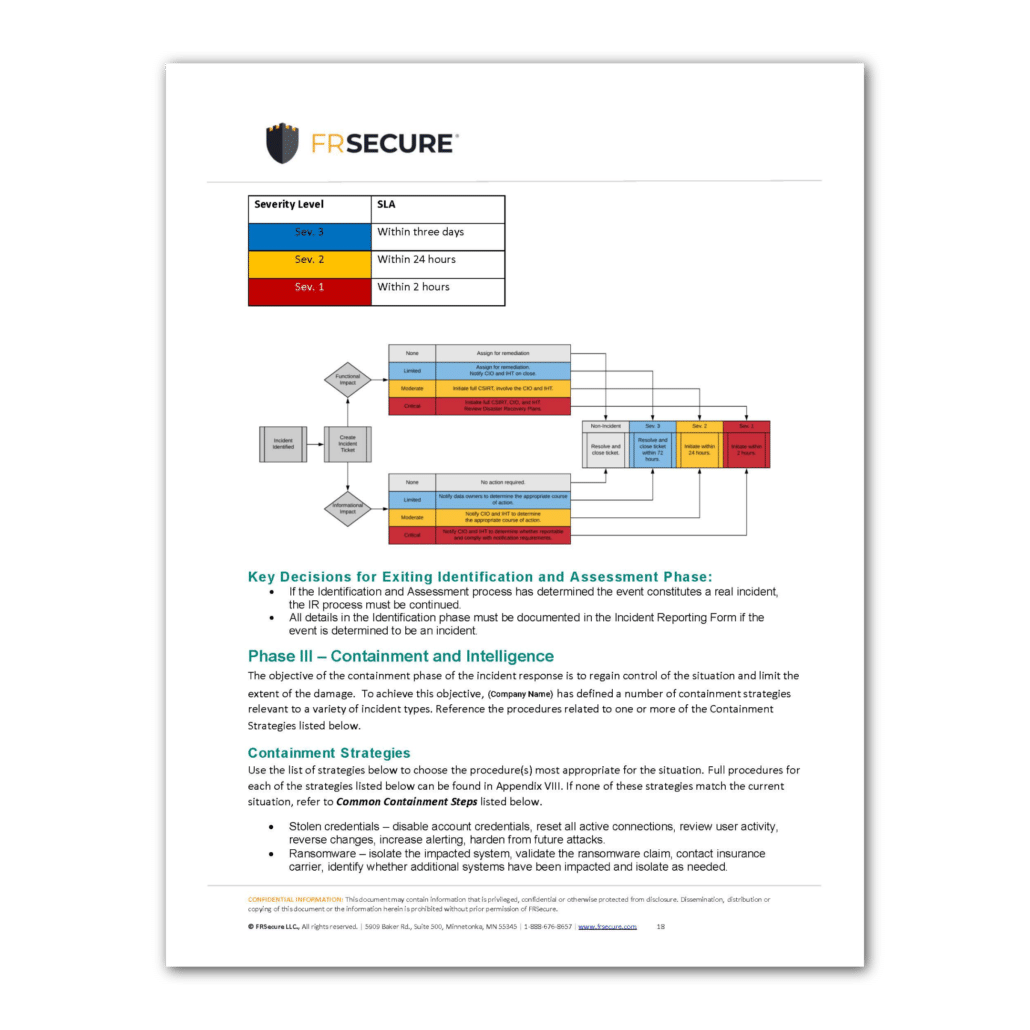
Key Decisions for Exiting Identification and Assessment Phase 17
-
Phase III – Containment and Intelligence 17
-
Containment Strategies 18
-
Common Containment Steps 18
-
Key Decisions for Exiting Containment Phase 18
-
Investigation 21
-
Initial Cause (“Root Cause”) Investigation 21
-
Phase IV – Eradication Details 22
-
Eradication 22
-
Key Decisions for Exiting Eradication Phase 23
-
Phase V – Recovery Details 23
-
Key Decisions for Exiting Recovery Phase 24
-
Phase VI – Lessons Learned 24
-
Documentation 24
-
Lessons Learned and Remediation 24
-
Forensic Analysis & Data Retention 25
-
Key Decisions for Exiting Lessons Learned Phase 25
-
Notification and Communication 26
-
Interaction with Law Enforcement 26
-
Regulatory Authorities 26
-
Customers 27
-
Public Media Handling 27
-
Plan Testing and Review 27
-
Appendices 28
-
Appendix I. Logging, Alerting, and Monitoring Activities List 29
-
Appendix II. Two Minute Incident Assessment Reference 30
-
Step 1: Understand impact/potential impact (and likelihood if not an active incident) 30
-
Step 2: Identify suspected/potential cause(s) of the issue 30
-
Step 3: Describe recommended remediation activities 30
-
Step 4: Communicate to Management 30
-
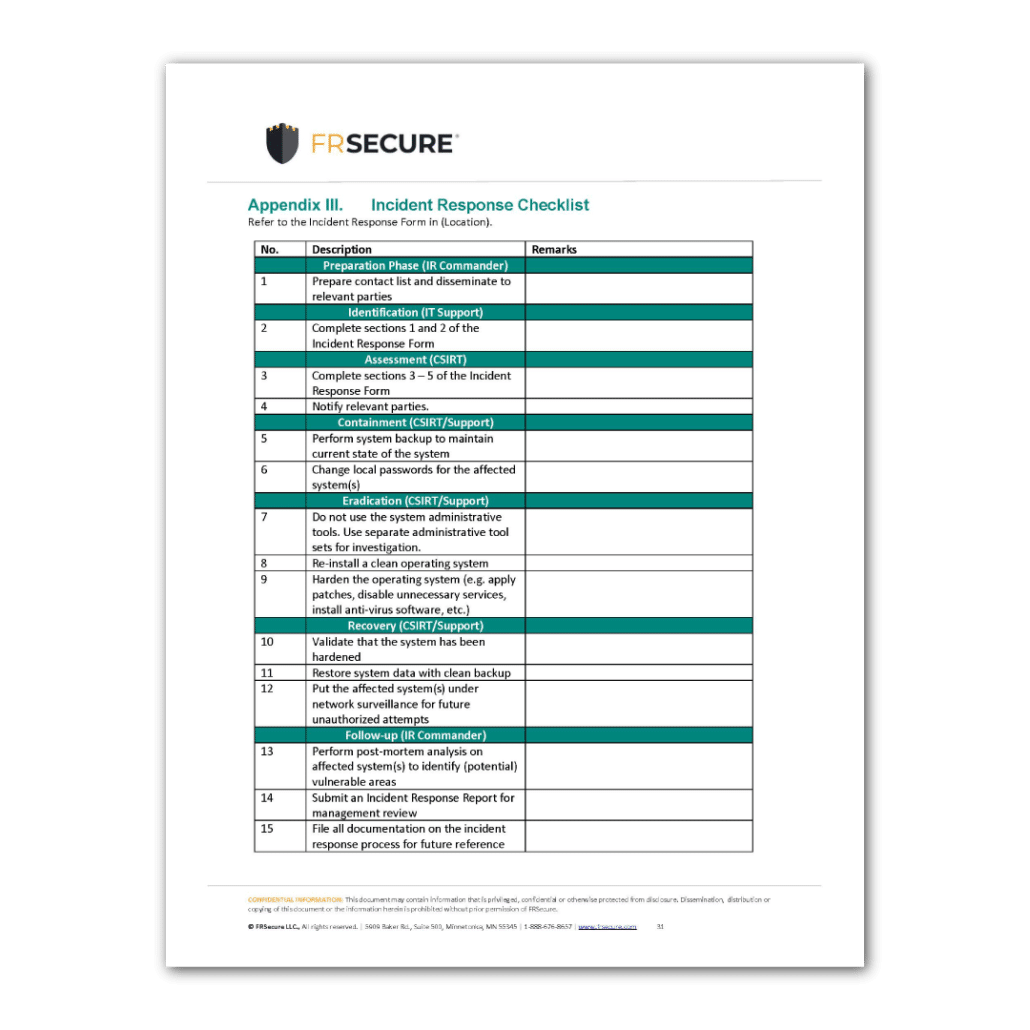
Appendix III. Incident Response Checklist 32
-
Appendix IV. Notification Requirements 33
-
PCI DSS 33
-
HIPAA 35
-
FDIC / OCC 37
-
State of Minnesota 38
-
CCPA 40
-
GDPR 40
-
Appendix V. Media Statements 41
-
Pre-scripted Immediate Responses to Media Inquiries 41
-
Pre-scripted Responses 41
-
Statement Writing Tips 42
-
Appendix VI. Customer Letter Template 45
-
Formal Email and/or Letter Template 45
-
Appendix VII. Incident Response Organizations 47
-
Appendix VIII. Containment Strategies 48
-
Stolen credentials 48
-
Ransomware 48
-
Virus Outbreak 49
-
Appendix IX. Cyber Insurance and Third-Party Service Agreements 51
-
Appendix X. Supporting Document List 52