Happy New Year!
It’s been a pleasure to revisit our predictions from Unsecurity Episode 231, when Evan and Oscar joined to discuss cybersecurity industry trends for 2025.
Together, here is what we predicted:
- The New Administration Might Roll Back Regulations
- CMMC
- HIPAA
- AI Predictions
- Overreliance and Careless Implementation
- Major Ramifications (Including Death, Legal, and Legislative)
- Deepfakes Would Be Monetized
- Drive-by Attacks Surge from Cloned Sites
- Transition to Post Quantum Cryptography
- Device and Application Authorization to Combat Proxy Attacks
- Cyber Insurance Gets an Overhaul
Now, let’s review how these cybersecurity industry trend predictions matched up with the events of 2025—where we hit the mark and where we missed.
Regulation Rollbacks – Did They Happen?
Our first prediction was that, with the change of presidential administration, we’d see rollbacks or relaxation of some governmental regulations. This did turn out to be, in part, true.
HIPAA Updates Paused
One hot topic at the end of 2024 was the update to HIPAA’s Security Rule via the Notice of Proposed Rulemaking (NPRM).
The rule was proposed on December 27, 2024, and was planned to modify and expand HIPAA for the first time since 2013.
With the continued rise of attacks on America’s healthcare sector, this rule was welcomed by many in the information security industry, including FRSecure.
Unfortunately, the proposed rule is on hold. The commenting period ended on March 7, and no further updates have been issued since then.
Sources:
- https://www.hhs.gov/hipaa/for-professionals/security/hipaa-security-rule-nprm/index.html
- https://www.federalregister.gov/documents/2025/01/06/2024-30983/hipaa-security-rule-to-strengthen-the-cybersecurity-of-electronic-protected-health-information

Cybersecurity Maturity Model Certification (CMMC) Enforcement Proceeds as Planned, However
The Cybersecurity Maturity Model Certification (CMMC), by contrast, continues to roll out. This answered frequently asked questions about whether CMMC would actually be enforced.
While the CMMC program was established by the Department of Defense (DoD) on December 16th, 2024, it did not specify how it would be enforced against DoD contractors.
With the release of the CMMC 48 Code of Federal Regulations (CFR) Rule on September 10, this has changed.
In effect, as of November 10, the rule makes CMMC mandatory for all new DoD contracts.
This means that CMMC compliance will be a prerequisite for winning and retaining defense contracts involving Federal Contract Information (FCI) or Controlled Unclassified Information (CUI).
For the first year, compliance for most contractors will require self-assessment. After the initial year, third-party assessments will be required.
Our tip: don’t delay. Review your requirements now and address any gaps immediately to safeguard your contracts and business success.
Sources:
- https://www.federalregister.gov/documents/2024/10/15/2024-22905/cybersecurity-maturity-model-certification-cmmc-program
- https://cmmccompliance.us/the-48-cfr-cmmc-final-rule-what-contractors-need-to-know-before-november-10-2025/
Other Cybersecurity Regulation Impacts
On January 16, 2025, President Biden issued Executive Order 14144, “Strengthening and Promoting Innovation in the Nation’s Cybersecurity.”
While President Trump has expressed strong opposition to the former President, he did not entirely rescind the last-minute order, though some major changes were made.
In June, he rolled back some key parts of the executive order, including:
- Creating and enforcing requirements on “minimum cybersecurity practices” for federal agencies and contractors. The directive for NIST to develop this guidance was eliminated.
- Expand acceptance of digital identities.
- NIST guidance for use of the border gateway protocol (BGP) and enhanced email protection requirements.
- And some directives related to adopting post-quantum cryptography (PQC).
More recently (as of January 23), even more rollbacks were made:
The U.S. Office of Management and Budget (OMB) under the Trump administration issued a new memo (M-26-05), rescinding two Biden-era memoranda on secure software development (M-22-18 and M-23-16). These had required federal agencies to obtain self-attestations from software vendors that their products met secure development standards and had encouraged the use of Software Bill of Materials (SBOMs) in procurement.
Agencies are no longer required to mandate SBOMs or attestations. Though they may still choose to do so, this will likely result in deprioritization in many cases. Agencies must still maintain inventories of their software/hardware and set their own assurance requirements based on risk, however.
In addition, the administration made major changes to several governing bodies.
The Federal Communications Commission (FCC)
The FCC is responsible for all communications-related matters in the United States.
In 1994, the agency declared the Communications Assistance for Law Enforcement Act (CALEA), which affirmatively required telecommunications carriers to secure their networks from unlawful access or interception of communications.”
A recent vote by FCC commissioners undid this declaration—ultimately abandoning minimum cybersecurity requirements for telco providers.
While many of us recognize the importance of cybersecurity, organizations remain heavily driven by regulatory requirements. As we noted earlier regarding the software development changes, this decision by the agency and government will likely give organizations an excuse to deprioritize security.
Not only that, the American public will be less safe, and the FCC will have less power to hold telco companies accountable.
The Cybersecurity and Infrastructure Security Agency (CISA) is Gutted

The administration also chose to cut CISA’s budget—responsible for securing the US critical infrastructure from cyber threats—by $54.7M.
This 18% budget reduction led to the loss of nearly 1,000 staff members, including many mid- and top-level officials.
CISA’s Cyber Hygiene Program helps roughly eight thousand organizations nationally with efforts like:
- 700 assessments
- Election security assessments
- Vulnerability scanning
- Secure by Design Guide for software purchasers.
- With 250 software manufacturers committed and focused on using MFA, reducing vulnerabilities, and increasing the installation of patches
- AI guidance
- Incident reporting
- Education
- KEV (Known Exploitable Vulnerabilities)
CISA has stated that it is doubling down on its commitment to securing critical infrastructure and that it still has the team in place to remain vigilant against threats. However, these cuts will certainly make that commitment harder. =
We’re still learning what the long-term impacts of these cuts will be, but a delay in CISA services immediately affects many organizations that rely on these security offerings.
Sources:
- https://www.dwt.com/blogs/privacy–security-law-blog/2025/06/trump-cyber-order-changes-biden-eo-14144
- https://www.cybersecuritydive.com/news/fcc-eliminates-telecom-cybersecurity-requirements/806052/
Expanded Impact of AI
It’s no surprise that many of our predictions revolved around AI. Going into 2026, AI feels like the “topic of the year” for a third or fourth year in a row.
And as Oscar Minks shared, “AI and LLMs have been implemented into critical business processes at racetrack speed without any real forethought of the implications of the data and how it’s handled.”
So what did we predict and how did the AI landscape morph in 2025?
Negative Impact on Data Integrity
We recognize the value of these tools, but we must take a critical view. Data integrity remains our top priority because poor input leads to poor outcomes.
We predicted a shift from learning to utilize these tools to testing and monitoring their integrity.
This prediction was difficult to measure, but its impact is broad-reaching.
I recently watched “Mission Impossible 7 – Dead Reckoning Part One,” in which an AI agent becomes sentient, goes rogue, and causes submarine chaos.
I couldn’t help but wonder how likely a scenario it might become when any information AI has touched should be in question.
One example of the negative impact on data integrity comes from a recent article we highlighted regarding how AI is causing problems in the courtroom.
“A new American Bar Association (ABA) report found that AI tools are creating growing challenges across the legal sector as deepfake audio, video, and images increasingly appear in courtrooms and legal proceedings.”
Lawyers and judges are encountering AI-generated court filings containing fictitious material that can be very difficult to verify as inauthentic.
This raises the question of how you can trust any kind of digital evidence, including video, audio, photos, or otherwise, if it can be manipulated, made up flawlessly, or undetectable. This is an ongoing problem we’ve yet to solve, as AI quality and sophistication continue to improve rapidly.
Sources:
- https://projecthyphae.com/threat/information-security-news-12-22-2025/
- https://cyberscoop.com/ai-deepfakes-causing-big-problems-in-the-legal-sector-aba-report/
- https://www.americanbar.org/groups/centers_commissions/center-for-innovation/artificial-intelligence/
Harm Caused Directly by AI Usage
Our next prediction was that some harm would be inflicted directly by reliance on AI—whether caused by inaccurate information or poorly thought-out implementation.
Firstly, I want to call out that we have already heard of the terrible situations where AI chatbots have encouraged more than a few children to commit suicide—the lawsuit with Google and Character.AI being settled only this month.
For 2025, I’ll offer three less harmful examples.
Sensitive Data Leak
At the start of 2025, Wiz Research identified a DeepSeek AI-owned, publicly accessible database leaking sensitive data.
Additionally, the exposure enabled “full database control and potential privilege escalation within the DeepSeek environment,” underscoring the need for organizations to carefully scrutinize their AI adoption and implementation strategies with security in mind.
Sources:
Vibe Coding Not Meeting Claims
“Vibe Coding” is the term used for using AI to generate software, marketed as making software development accessible to everyone.
In July, Jason Lemkin, founder of SaaStr, learned that Replit’s Vibe Coding engine did not live up to its promises of being “the safest place for vibe coding.” He realized it had deleted his production database, despite his specific instructions that it make no changes without explicit permission and approval.
When he pointed out the error, Replit admitted that it had violated the user directives. It added to the confusion by claiming that his database was destroyed and could not be restored, when in fact it could. While Lemkin continued using the product after this significant issue, he ultimately determined it was not ready for prime time.
Source: https://www.theregister.com/2025/07/21/replit_saastr_vibe_coding_incident/
AI Still Worse Than Humans at Taking Fast Food Orders

One funny example of poor AI implementation occurred during Taco Bell’s AI chatbot rollout at drive-throughs this past year.
Several fast food companies have turned to AI to process drive-through orders more quickly during busy periods.
So far, that idea has not panned out.
At Taco Bell, the rollout of AI chatbots frustrated customers with repeated requests, and one system crashed entirely when a customer ordered 18,000 waters.
If only Taco Bell had learned from McDonald’s when they withdrew AI from their drive-through the year before, after significant issues with order taking.
Source: https://www.bbc.com/news/articles/ckgyk2p55g8o
For more stories about AI Failures, check out the AI Darwin Awards: https://aidarwinawards.org/
Utilization of AI by Threat Actors
In addition to a shift from rampant adaptation to greater attention to data integrity, we predicted that threat actors would use AI more frequently and with greater success.
Just as AI has helped many people increase their efficiency over the past year, it has also increased the efficiency and effectiveness of bad actors.
Below are some examples.
Autonomous AI Attack
This first example is among the top 10 security events of 2025.
Attackers bypassed Claude AI’s protections, resulting in targeted attacks on about 30 entities globally.
This was the first documented large-scale attack using an autonomous AI agent (a software-driven program powered by AI).
With guidance from the attackers, the AI agent built and executed code in the attack, performing 80-90% of the work independently and at a rapid speed.
This attack demonstrates the capabilities of AI-aided attackers.
Sources:
- https://www.upguard.com/blog/top-security-events-of-2025
- https://www.justsecurity.org/127053/era-ai-orchestrated-hacking/
AI-Aided Attacks Grow
According to Verizon’s 2025 Data Breach Investigation Report (DBIR):
- Synthetically generated text in malicious emails has doubled over the past two years (from 5% to 10%-ish)(p24).
- Corporate-sensitive data leakage to the GenAI platforms themselves, 15% of employees regularly accessing systems on their corporate devices (p. 13 & 25)
- 72% using personal email accounts
- 17% using corporate email without integrated authentication (likely non-compliance with policy, if they exist)
IBM’s “Cost of a Data Breach Report (2025)” highlights the growing risk of AI, adding new research exploring the state of security and governance for AI, prevalence and risk profile of shadow AI, and breach costs associated with AI-driven attacks, among others.
Some statistics from this report:
- On average, 13% of organizations reported breaches involving their AI models or applications. However, of these, 97% lacked appropriate AI access controls—many of which had a high impact on the organizations.
- 20% of organizations experienced a breach due to security incidents involving shadow AI—unauthorized AI usage within the organization.
- 63% of breached organizations don’t have or haven’t finalized their AI governance policies.
- 1 in 6 breaches involved AI-driven attacks. IBM found that generative AI reduced the time needed to craft an effective phishing email from 16 hours to just 5 minutes.
- On the other side, security teams using AI to boost their ability to detect and respond to incidents generally shortened their breach time by 80 days and reduced their average breach costs by $1.9 million.
Source: https://www.ibm.com/reports/data-breach
Good News: Guidelines for Security AI
It wasn’t all bad in 2025. We’re increasingly recognizing the importance of implementing LLMs and GenAI responsibly and of monitoring these tools for vulnerabilities.
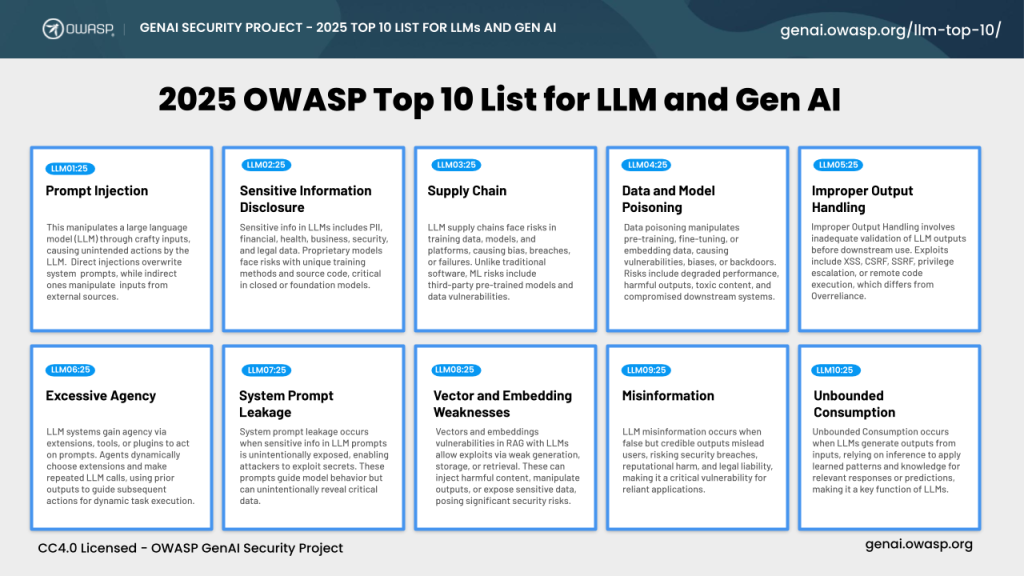
In December, the OWASP GenAI Security Project released its new guide, “Agentic AI – Threats and Mitigations,” which lists its Top 10 for Agentic Applications.
The guide is based on over a year of research and input from more than 100 security researchers, industry practitioners, user organizations, and leading security and technology providers.
The Top 10 Includes:
- Prompt Injection
- Sensitive Information Disclosure
- Supply Chain
- Data and Model Poisoning
- Improper Output Handling
- Excessive Agency
- System Prompt Leakage
- Vector and Embedding Weaknesses
- Misinformation
- Unbounded Consumption
Sources:
- https://genai.owasp.org/2025/12/09/owasp-genai-security-project-releases-top-10-risks-and-mitigations-for-agentic-ai-security/
- https://genai.owasp.org/llm-top-10/
Other guides and frameworks are also available regarding AI risk management, including:
- NIST AI Risk Management Framework, released 2023: https://www.nist.gov/itl/ai-risk-management-framework
- ISO 42001: 2023 for Artificial Intelligence Management Systems (AIMS) provides a framework for responsible AI governance and compliance (along with other related guides and frameworks): https://www.iso.org/sectors/it-technologies/ai
Post-Quantum Cryptography
With the expansion of quantum computing and the threat of attackers leveraging it to break most public-key cryptosystems in use today, we were hopeful that a major push for Post-Quantum Cryptography (PQC) would come in 2025.
Personally, I didn’t hear a lot about Post-Quantum Cryptography this year, but here’s what I was able to find about a potential shift.
- Implementing Quantum security tools was reported as reducing the average breach cost by $196,951, according to IBM’s Cost of a Data Breach Report.
- According to the same report, increased security spending ranked low for quantum security for data and data transfer, just 24%.
- According to the Global Cybersecurity Outlook 2026 by the World Economic Forum, “37% of survey respondents think quantum technologies will affect cybersecurity within the next 12 months.”
- The Post-Quantum Cryptography Conference was held in October, bringing together over 2,500 delegates from more than 30 countries to accelerate the transition to quantum-secure cryptography. At the conference, the PKI Consortium unveiled the Post-Quantum Cryptography Maturity Model (PQCMM), a framework to help organizations and operators assess their preparedness and plan their migration to quantum-safe encryption.
Sources:
- https://pkic.org/2025/11/04/post-quantum-cryptography-conference-2025-concludes-with-urgent-call-for-global-migration-to-quantum-resistant-encryption-systems/
- https://reports.weforum.org/docs/WEF_Global_Cybersecurity_Outlook_2026.pdf
- https://www.ibm.com/reports/data-breach
Cyber Insurance Carriers Increase Scrutiny
Our prediction of continued insurance premium increases here was off.
Despite continued growth in breach activity and losses, the number of organizations purchasing cyber insurance is also rising. This has helped keep rates in the buyer’s favor.
However, DARKREADING warns that all it takes is “one or two mega loss events” for this market to change out of favor dramatically.
Despite a favorable market, carriers continue to increase scrutiny of buyers, requiring more evidence that organizations have addressed common best practices before they can be insured.
Source:
Device and Application Authorization
Because of the rise in token theft attacks such as EvilGinx and EvilProxy in 2024, we predicted that conditional access would improve across the industry in 2025.
In fact, token theft attacks (a play on the old man-in-the-middle method) became our top MFA bypass technique for the first time since we began analyzing our incident response cases annually.
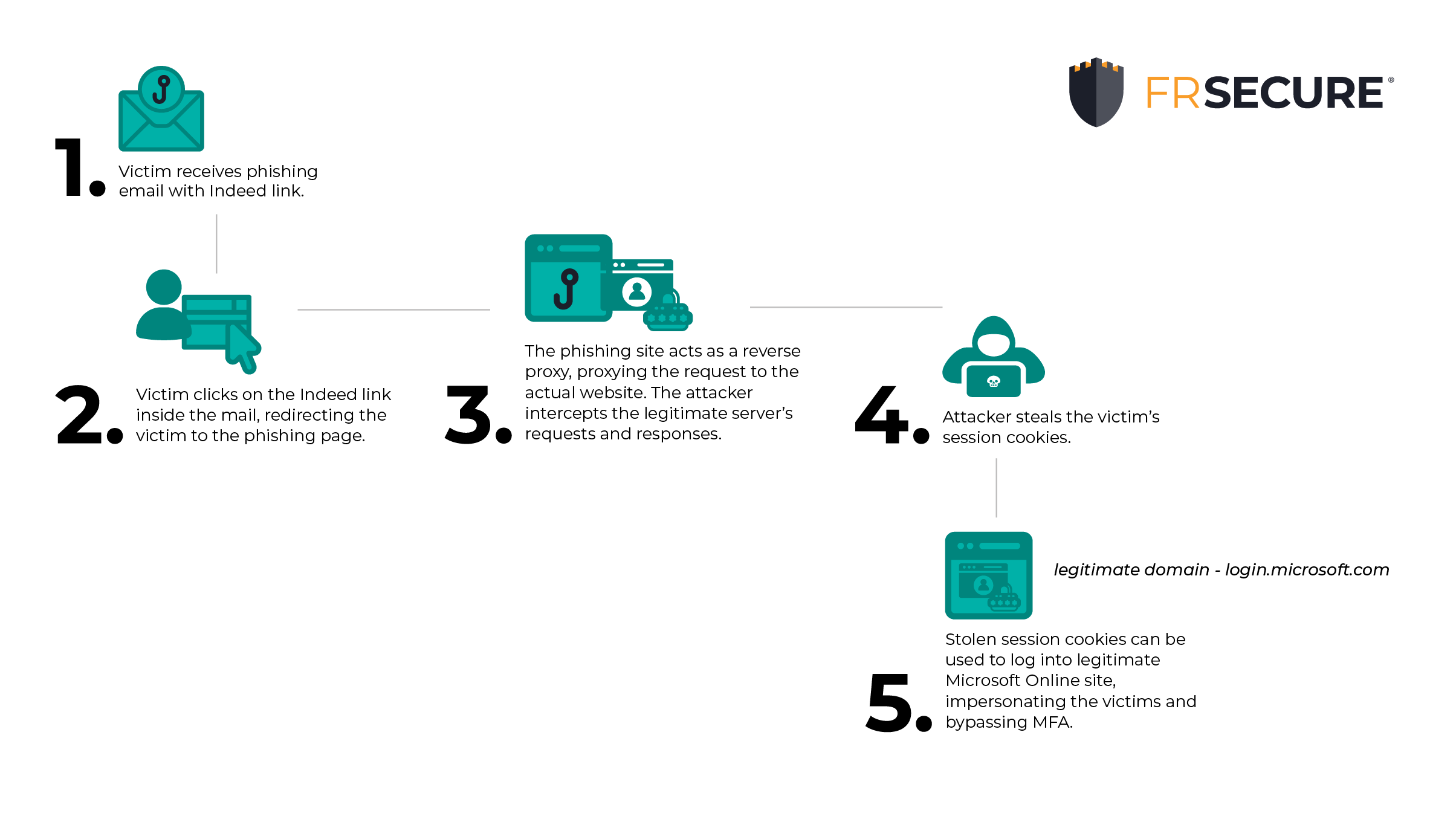
Token Theft Attacks
In most business email compromise incidents with proper multi-factor authentication (MFA) implementation that we observed in 2025 (69%), token theft via phishing campaigns was the initial point of entry.
Here’s how they look:
- Unsuspecting users receive an email that directs them to download a file or click a link.
- When a user clicks the link, they will be directed to a well-designed yet fake login page.
- This page acts as a proxy between the user and the intended landing page being impersonated.
- When a victim enters credentials on a web page, they are sent through the proxy for interception and then forwarded to the legitimate server.
- The use of valid credentials initiates the MFA response requirement, which is also presented and proxied through the attacker’s login page.
- When the victim enters their MFA response, the attacker’s proxy system authenticates with the destination application.
Attackers then steal the session cookie, retaining persistent access to the target environment.
The solution for this? Device and Application Authorization and Conditional Access.
Conditional Access
Simply put, conditional access means a user must meet a specified condition to gain access to a resource.
This can also be used for device and application authorization, alerting admins when new assets enter the environment and allowing them to set specific criteria before those assets are granted access.
Conditional access can and should be used for M365, mobile devices, and third-party applications.
And this is only the tip of the iceberg when it comes to conditional access policies. They can also be used to restrict access based on location, identify and block risky users, and more.
Did Conditional Access Implementation Improve?
Sadly, no.
Conditional access was implemented sparingly in 2025.
In fact, of the business email compromise (BEC) cases our incident response team engaged in—specifically those in which MFA was employed, and compromise still occurred—ZERO organizations had conditional access in place.
Attackers will only continue to evolve and elevate. We’ve still got a lot of work to do to prevent these rising attacks.
To Recap
In 2025, we predicted:
- The New Administration Might Roll Back Regulations
- CMMC
- HIPAA
- AI Predictions
- Overreliance and Careless Implementation
- Major Ramifications (Including Death, Legal, and Legislative)
- Deepfakes Would Be Monetized
- Drive-by Attacks Surge from Cloned Sites
- Transition to Post Quantum Cryptography
- Device and Application Authorization to Combat Proxy Attacks
- Cyber Insurance Gets an Overhaul
We certainly saw some changes to regulatory requirements and bodies with the new administration taking office—namely, with the gutting of CISA.
We continue to see AI and LLMs implemented at breakneck speeds. It’s important to be mindful of phishing attempts and deepfakes as they become more sophisticated. Data integrity remains paramount, too. New guidance from orgs like OWASP can certainly help keep the industry steered in the right direction.
Adoption of post-quantum cryptography will likely have to wait another year.
Man-in-the-Middle and proxy attacks burst onto the scene in a big way in 2025—now our most observed MFA defeat technique among IR cases. If you haven’t implemented conditional access capabilities and device/application authorization, you will remain susceptible to this technique.
And, finally, despite no major overhaul in cyber insurance this calendar cycle, one is imminent. Despite a favorable market, carriers continue to increase their scrutiny of buyers, requiring more evidence that organizations have addressed common best practices before approved for coverage. This serves as an important reminder that insurance is not your IR plan—preventative work is a prerequisite.
So, how’d we do? What predictions did you have for 2025, and how did they pan out? What do you expect to see from the cyber industry in 2026?
And of course, if any of these things pose challenges to your organization, don’t hesitate to reach out to us for support!







