Phishing in Healthcare
Welcome to part two of our series with CCI, where we break down the five most common causes of security incidents within the healthcare industry.
If you missed the introductory post, go back and give that a glance to get an idea of what the series is going to take a look at and how it’s structured.
Here, I’ll be discussing phishing.
Phishing has been a widely used tactic for attackers for quite some time, and we haven’t seen the technique’s usage wane because it continues to prove successful. Especially given the distractedness that has come with a global pandemic, and the prioritization hospitals and other healthcare providers had to give to it, phishing remains a major cause of breaches in the industry.
To combat this issue, we need to avoid that distractedness. Education becomes a critical component of this. If we know what we’re looking for, we can more easily spot it—even when our minds and focus are elsewhere.
So, let’s dive into what phishing is, the types of phishing attacks that exist, and some examples and statistics as it relates to the healthcare industry specifically.
What is Phishing
On its face, the methods of cyber attackers are all the same: find a weakness and exploit said weakness to gather information or access.
Phishing is no different. The vulnerability is just us.
Rather than exploit a system or program, phishing exploits humans.
The practical application and execution of a phish vary, but all types of phishing attacks stem from the same basic principle—that principle being social engineering.
Social Engineering
Social engineering is human hacking. The same way an attacker can manipulate the code of a program to get it to do something malicious, an attacker can manipulate the trustingness of the human brain. And, frankly, it’s probably easier.
Social engineering is the practice of having a deep understanding of human behavior and psychology—and then using that knowledge to get something out of it.
It’s human nature to be both trusting and helpful. Social engineers (the malicious ones, anyway) bank on that.
How Social Engineering Translates to Phishing
A phish is essentially the practical application of social engineering. Using manipulation techniques, an attacker hopes to persuade you to take action in a way that benefits them.
Social Responsibilities
Phishing is extremely common in a workplace environment. And most of us try to be as helpful as possible when it comes to our coworkers and employers.
So, we often see that attackers will pose as someone within that person’s same company. There are a variety of methods for doing so, but generally, if an attacker can do a good job making you think a request is from your coworker, you’ll probably try to help in some capacity.
Especially when a favor has already been done for you, if you’ve already committed to something, or if you simply like the person asking, the want to follow through on that request goes way up.
Urgency
Speed leads to carelessness. The less time you have to act on something, the less thinking you can do about it.
If the CEO of a multimillion-dollar business partner of yours tells you they need something immediately or if your bank alerts you that $6,000 had been stolen from your personal account, you will act on those right away.
But, by immediately taking action, you may fail to recognize that the action requested by the partner is weird or that your bank’s communication looks slightly different than normal.
Often, social engineers will mimic authority, expiring opportunities, scarcity, or a potentially harmful situation in their attempts to decrease the likelihood that we take the time to vet it.
Types of Phishing Attacks
So, we know the goal of a phish and we know the emotional responses they try to trigger to succeed in their phishing attempt.
But how do they enact these various types of phishing attempts?
Email Phishing
By now, I actually assume everyone understands what an email phishing attempt is. They’re routinely the number one most common attack vector in the social engineering realm.
The problem? Even if people know what email phishing is, we still struggle to avoid phishing scams.
The FBI reported that Business Email Compromise (BEC) attacks cost organizations $1.77 billion in losses in 2019, and they received a total of 23,775 complaints related to BEC threats.
It’s working, and until it stops working, it’s not going anywhere.
The End Goal
Typically, we see these phishing attacks attempt to do one of two things.
The first is getting you to click a link you shouldn’t have. Links can either have something malicious caked in or they can take you somewhere that looks like an account screen and try to get you to log in.
In both instances, the goal is typically to harvest credentials.
Below is an example of a legitimate phishing attempt where everything looks normal on the surface, but then if you were to go through to the ACESS Wet Design link, you’d be taken to a spoofed credential site. Should you put in Microsoft Office credentials, Gmail credentials, or something similar, the attacker would have captured that information for later use.
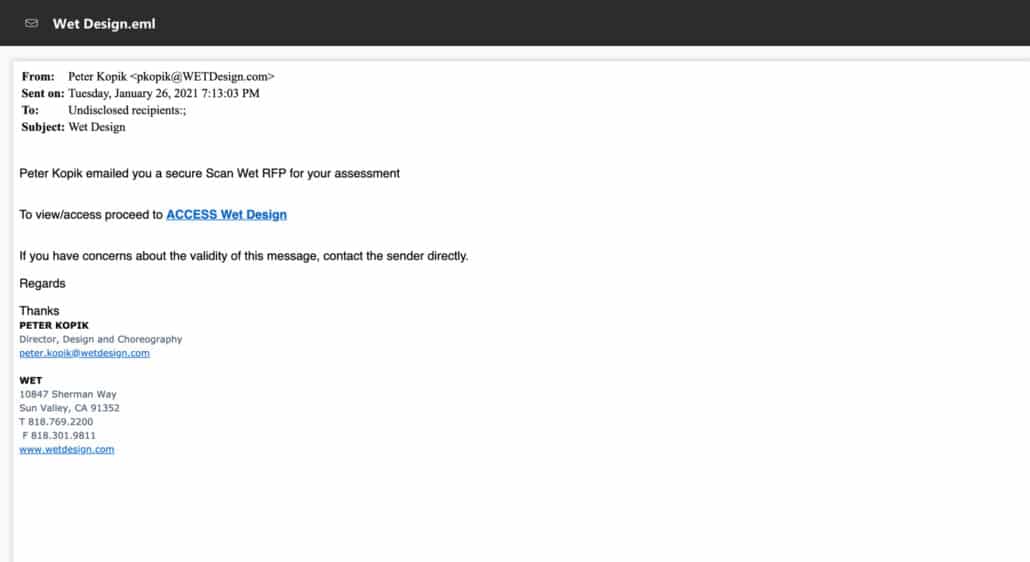
Spoofed attachments are also common. In this effort, we may see a PDF that looks like a purchase order or new nursing hour rotation for the month. In these documents malicious payload is built into the file.
Because of this, it could give an attacker reign to anything from sensitive documents, to admin access, to a recording of every stroke that the user made on a keyboard.
The Healthcare Implications
It’s scary to think about what kinds of information could be obtained by phishing a healthcare organization.
Healthcare records include important information about patient history, family history, financial implications, medications, insurance, and more. Having those leaked is an easy way for someone’s identity to be stolen or their medical benefits taken advantage of. And with staff having access to patient portals, one lucky stolen credential could be enough to gather a ton of patient information.
An attacker gaining admin access is a scary proposition as well. Not only would an attacker be able to gather this same sensitive information, but they’d also have an easier time accessing some of the systems and information about how the hospital runs. Things like supply chain, payroll information, and internet-connected medical devices would all be more likely to be accessed and abused.
With every incident, reputation, business uptime, and finances are all at risk of being impacted. In healthcare, this impact is magnified because an incident has the potential to physically harm people. That’s why we must take phishing especially seriously in the healthcare industry.
Spear Phishing
Spear phishing is another type of phishing attack, but they target a narrower audience—hence the spear.
Typically, these attempts target someone with authority.
These attacks are more coordinated. They usually involve detailed intel gathering on the target subject and are not attempted until things like job title, email address, and specific information about their role are obtained.
And there’s a good reason for this.
The End Goal
If I can gain access to the account of someone with authority at a business or hospital, I can more easily manipulate people into helping me out.
Remember how we said that phishing attacks rely on social responsibility and urgency?
Well imagine you’re in finance for an organization, and you get an urgent request from your boss to wire money to a third-party entity. If they asked you in person, that’s probably something you’d take on immediately.
The attackers are hoping the same is true via email.
If they can gain access to a leader’s credentials, they now gain the access to whatever systems that person is using (and it’s fairly often that people with power at organizations have special access privileges). It’s easier to coax an employee to do something on your behalf.
The Healthcare Implications
Reputation, business uptime, financials, and patient safety (human lives) will always be concerns when it comes to healthcare incidents.
Now, imagine how that’s amplified when the affected users are ones with a great deal of power, control, and access within the organization.
Whaling
Whaling is a variation of spear phishing that targets the highest of powers at an organization.
C-level executives, board members, presidents, and founders are all targets in whaling attacks.
It is less likely to be used as a tool to coerce and gain access—more a direct information-gathering exercise.
As we round out spring each year, attacks relying on tax season become more common. If I can gain the Social Security information or bank account information of a healthcare executive through a tax scam, my return is a lot higher. They’ll have more economic impact than someone working an entry-level position for example.
The Healthcare Implications
This tends to have a more personal impact, but it can pose danger for the organization as well. Gaining information about leaders within an organization could lead to more access.
And we already know what C-level access might be able to accomplish at a hospital.
Smishing and Vishing
Smishing is the text message version of email phishing. Vishing is the phone call version.
You likely see these all the time in your personal life—text messages asking you to fill out a survey or telling you you’ve won something, or phone calls telling you your bill is overdue.
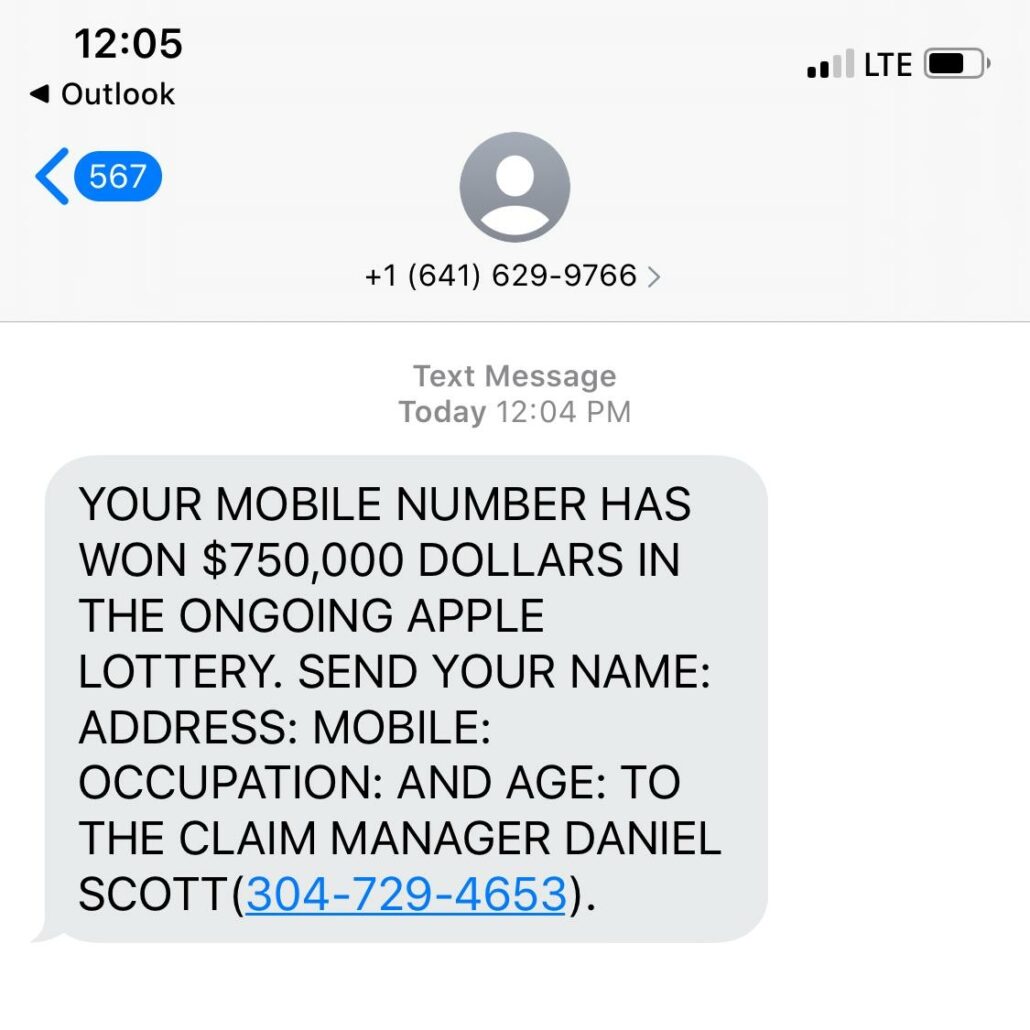
Yeah, sure I did.
The efforts are the same for businesses. The motivation is just different.
Typically, these attempts are used to glean information that can then be used to create an advantage.
When FRSecure conducts these exercises for clients, we have the most success when we impersonate their IT service provider. By acting as a trusted business confidant, it’s more likely the person on the other end of the phone will give sensitive information.
In fact, a lead social engineer on the FRSecure team suggested that they see a near 80% success rate when calling targets.
And the problem exists because it’s harder to train, and it’s harder to verify. It’s easier to look at an email and poke holes in things like language, sender emails, link structure, etc. But how do you prove someone on the other end of the phone is who they say they are—especially when you have to think and react in real-time?
Healthcare Implications
The same information that can be gleaned from a phishing attempt can be gained from a smish or vish. An employee releasing sensitive information or credentials could pose problems down the line for all the reasons we’ve already discussed here.
Employees must know what to look out for with these types of attacks the same way they should with email attacks.
Social Media
Social media is an often-overlooked attack vector in social engineering but can be used in multiple ways to an attacker’s benefit.
Just like smishing and phishing, social media can be used to push bogus links for credential gathering or malware downloading, message people about divulging sensitive information, and more.
Not to mention, company and employee use of social could implicate the organization as well. Posting photos of desk setups, employees with badges on, office layouts, and more are all additional ways attackers can gather information
Healthcare Implications
If employees access personal social media on their work devices, any attack success could directly impact your internal assets.
And the information gathering I just mentioned is not commonly considered. If you post an image on Facebook profiling one of your fantastic nurses or share an all-physician picnic you hosted and their badges are showing, an attacker can take the image of the badge and recreate it to make a fake one look more legit.
Now they may not even be questioned when trying to access a supply closet, server room, or worse.
Social media needs to be considered the same as all other attack vectors when combatting social engineering attempts.
The Concern by the Numbers
Phishing is the number one attack vector among healthcare organizations of late. In a 2019 survey conducted at HIMSS (a large medical conference), nearly 80% of respondents had experienced a significant security incident the year prior. And phishing was a big reason.
Phishing appeared in 59% of significant security incidents across all organizations, and 69% of incidents at hospitals according to the same survey.
And the culprits were most often bad actors in these scenarios. “Online scam artists” accounted for 28.6% of leaked information—with negligent insiders coming in second with 20%.
You can see how these two things work hand-in-hand.
Attackers continue to probe vulnerable employees, and vulnerable employees continue to unintentionally leak sensitive information.
And, despite how common knowledge these types of phishing attacks have seemed to become, they continue to work at a high rate. Therefore, we have to continue to find ways as organizations to combat phishing attempts.
—
To learn more about how to combat phishing attacks, feel free to contact us with questions.







