If you’ve been following along with our State of InfoSec series this year, you’ll know that we have been reviewing 162 incident response cases over the last two years to provide a snapshot of the InfoSec industry in the SMB market. In this edition of the series, we examine trends in business email compromise payloads.
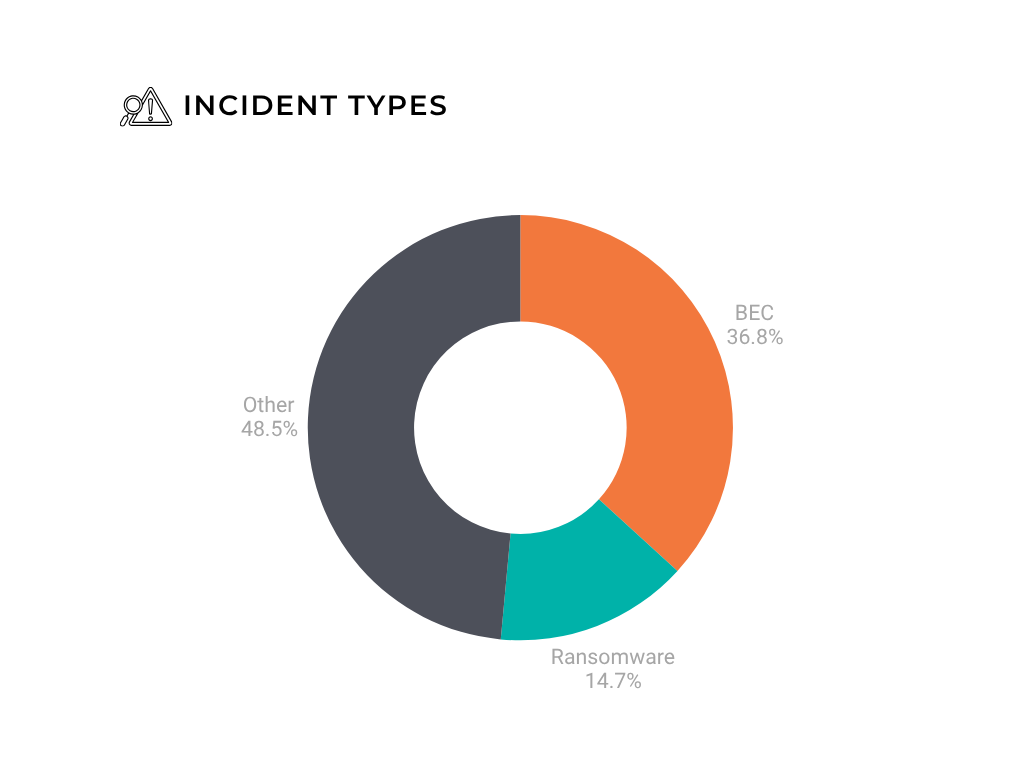
In the exercise overall, we broke the incident categories down into three buckets:
- Business Email Compromise (BEC): Instances where attackers compromised email accounts used for business purposes.
- Ransomware: Cases where client environments were compromised, with attackers encrypting (scrambling data into secret code) systems and/or exfiltrating (withdrawing) data to demand a ransom for its return.
- Internal Compromise: Situations involving compromised systems that had not yet escalated to more damaging events. Some investigations resulted in no system compromise and have been classified as false positives.
By providing you with this inside look at what’s happening in the industry, we believe you can better protect yourself against attackers’ methods.
A Quick Recap: Token Theft Attacks
In our previous breakdown, we examined token theft attacks. These attacks, which deliver malicious downloads to bypass Multifactor Authentication (MFA) through phishing emails, have surpassed MFA fatigue as the top observed MFA bypass technique.
We must note that this shift in attacker methodology does not negate the need for MFA for all publicly accessible and internal logon systems. However, MFA implementation is only effective when done correctly.
For more details on our recommendations, reference the intro post of the series.
Summary: Token Theft Attack Prevention Recommendations
- The number one defense against these types of attacks is education.
- Validate all devices and applications that have the authority to access your environments through conditional access policy processes.
- Maintain or establish a comprehensive vulnerability management program that includes an asset inventory and a thorough new system/application approval process, with detailed documentation.
Even with widespread use of defensive techniques and conditional access controls against token theft, attackers will find new ways to compromise accounts and environments.
Educating our user base will continue to be our first line of defense!
Most importantly, continue to train your users and upskill everyone.
Conduct regular and interactive information security training that focuses primarily on how to identify phishing emails. Ensure that users understand they will not be shamed if they are a victim; rather, focus on what to do when they become one.
Key Training Efforts for Token Theft Attacks and BEC
- Reporting incidents right away so the damage can be minimized.
- Including regular social engineering testing, like simulated phishing exercises, of users to determine if your education efforts are working.
- Knowing what your current risk level and tolerance are, and utilizing this baseline to continue to mature your education initiatives.
Other Business Email Compromise Causes
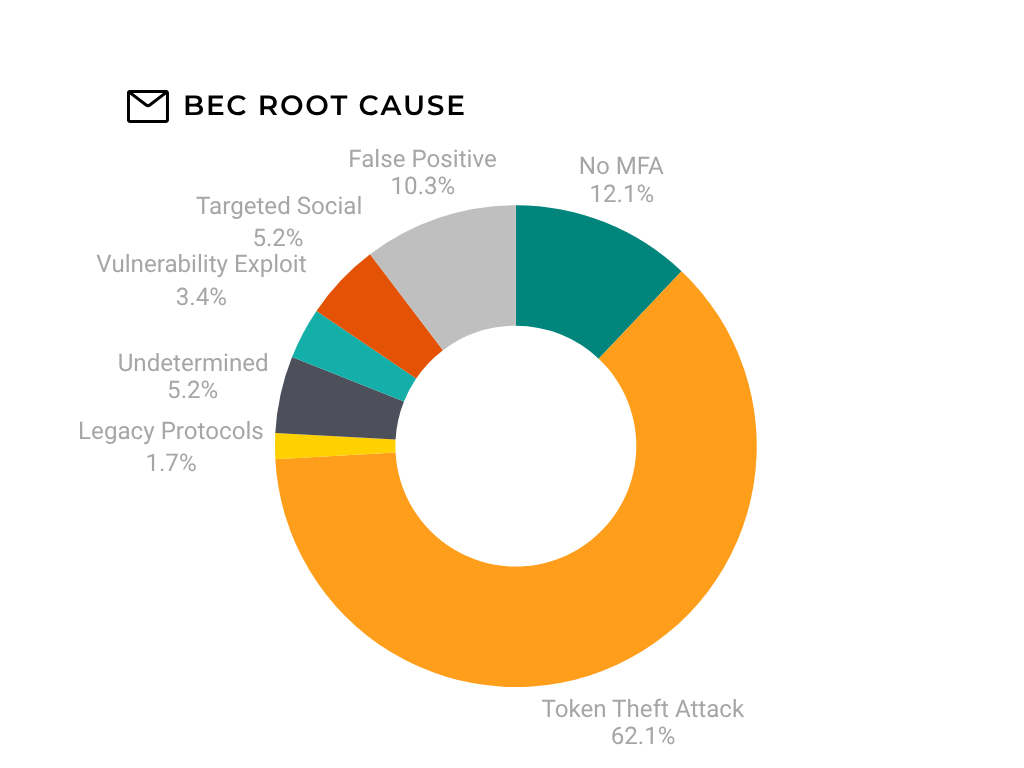
Token Theft Attacks certainly aren’t the only method for compromise in our email environments. In the incidents we’ve observed over this period, we saw the BEC root causes of:
- No MFA: 12%
- Token Theft Attacks: 62%
- Legacy Protocols: 2%
- Vulnerability Exploit: 3%
- Targeted Social: 5%
- False Positive: 10%
- Unknown: 5%
Overall, business email compromise (BEC) accounted for 36.8% of incidents we observed over this period.
Onto Business Email Compromise Payloads
What is a Payload?
A payload is the component of the attack that executes the malicious activity after initial compromise, ultimately deployed as a result of the initial attack vectors.
Common types of payloads include data theft, ransomware, remote access trojans, and crypto miners, to name a few.
What Business Email Compromise Payloads Did We Observe in Our Incident Cases?
Let’s review the specific business email compromise payloads we encountered during our analysis of incident cases.
Consistent with last year’s report, the payload of these attacks remains the same.
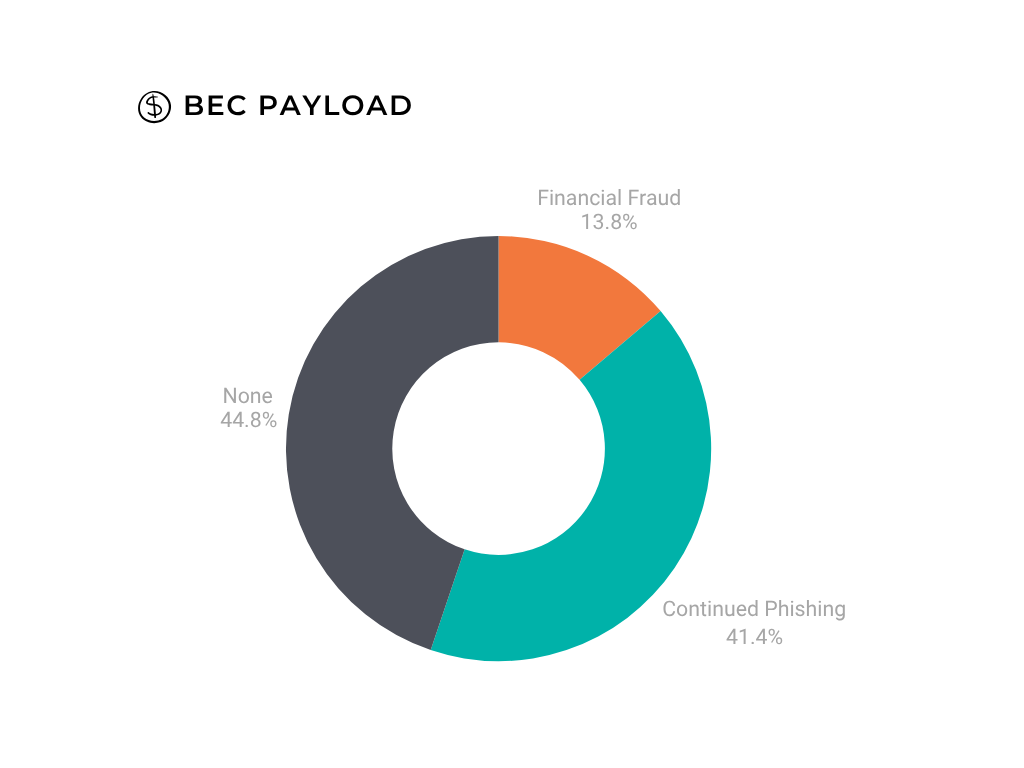
Continued Phishing or Internal Pivot
41% of cases resulted in continued phishing.
Attackers continue to utilize their initial foothold to identify and target other high-value users within the organization—typically, executives and other individuals with financial decision-making and spending authority.
These users are targeted because they can either immediately execute ACH fund transfer requests or because their authority makes it easier to trick another unsuspecting victim in the chain into executing the transfer on their behalf.
We observed that attackers also continue to utilize initial access to identify and infiltrate other businesses (clients, suppliers, etc.) that are associated with the victim.
ACH Transaction Fraud Attempts
14% of the cases resulted in attempted ACH transaction fraud.
I am happy to report that none of these were successful in our observed cases! All victims had implemented secondary control for ACH transactions, and they were able to identify and stop the attempt quickly.
This is excellent news, and a win for the good guys!
No Further Actions
45% of our cases resulted in no further action. This is ideal, and encouraging that this was the result for so many of our cases.
In all these cases, the compromised account was quickly discovered, and the incident response plan was immediately executed.
Being prepared with plans and knowing how to execute them are our most effective tools in preventing damaging attacks.
We have all either been or will be a victim, so let’s make sure we are diligent and confident in our response capabilities.
Ransomware
After reading this, you may be wondering, “What about ransomware?”
Yes, as mentioned, ransomware is a notable business email compromise payload and in cyberattacks in general. In the last two years, FRSecure incident responders have observed 27 cases of ransomware.
However, the ingress methods we observed for ransomware cases varied greatly. Additionally, ransomware attacks pose a greater threat than continued phishing attempts.
For these reasons, we’ll provide a more detailed breakdown of ransomware separately from this business email compromise payload discussion.
To explore this in detail, our next post will break down motivations, ingress methods, and ethical considerations around ransomware.
As always, if you’d like support from the FRSecure team on any of the topics discussed in this post or series, don’t hesitate to reach out!
And, to hear more about the State of Information Security, join us in Minneapolis at Hacks & Hops on October 16 for Oscar’s full presentation on our findings!







