If you’ve been interacting with FRSecure for a while, you may recall our State of Information Security report. Published in 2023, it provided a detailed look at security in the SMB space based on statistics gathered from our risk assessment control data and incident response cases.
As is often the case at FRSecure, we’re shifting things just a bit.
We’re still going to provide you with detailed breakdowns of attack measures and their subsequent fixes from our internal incident response team—but instead of a statistic-heavy report, this will be a series of stories.
Over the past two years, our team has managed over 125 incident response cases, dealing with incidents that have affected small, medium, and enterprise-level entities alike.
Through our analysis of these incident response cases, we’ve discovered and documented the tactics, techniques, and protocols attackers use to compromise and damage organizations.
The goal of this series is to offer you a peek behind the curtain and expose the realities of attacker operations while also providing actionable insights to lower your risk and minimize the impact if (or when) you become a target.
A Review of 2023
As we look at our recent incident response cases, it’s important to consider where we were two years ago. Shifts in the industry can tell us quite a bit about the surging attack methods, businesses’ priorities, and how the cat-and-mouse game evolves with them.
Incident Types
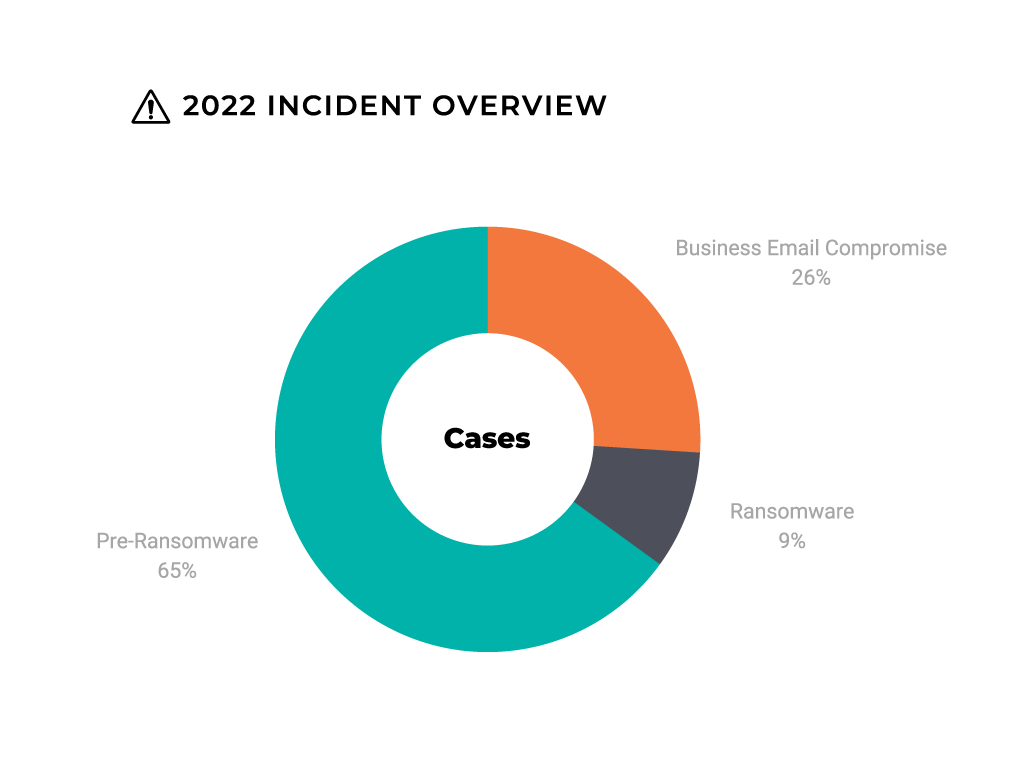
In our last report, we observed that the most common incident types were:
- Pre-ransomware: 65% of incidents observed
- Business Email Compromise: 26% of incidents observed
- Ransomware: 9% of incidents observed
To break this down even further, we observed 14 incidents resulting from business email compromise. Of those, 64% came from a social engineering campaign. Despite attack types and vectors constantly evolving, social engineering remains king.
The most common method of social engineering utilized was phishing emails, including links to malicious websites designed to harvest email credentials or authentication cookies.
And two things remain true—social engineering continues to prove successful, but we also recognize this as an industry and are working to combat it.
What we had to show for it was this:
- 68% of organizations studied had deployed proper malicious code protections for all applicable transmission methods.
- 80% of organizations observed tested users periodically on their susceptibility to common attack vectors like downloading dangerous files and following malicious links in emails, documents, or web pages.
MFA Is a Good Solution, But Not a Perfect One
We know that MFA can limit access to information and systems if attackers can harvest credentials. However—and we’ll touch on this in the series—there are certainly workarounds.
Similarly, MFA is only effective when implemented appropriately and has buy-in. Of the fourteen business email compromise cases we worked on, only four organizations had fully implemented multi-factor authentication controls.
- 70% of organizations protect administrative login pages with multi-factor authentication.
- 60% of organizations protect general-user login pages with multi-factor authentication.
Notice how I didn’t just call out implementation but also buy-in and training. MFA defeat will be a category of this year’s incident recap. There are ways for attackers to circumvent MFA—especially if users aren’t aware of the attacks or trained how to spot them.
MFA fatigue attacks occurred in 50% of the BEC incidents we observed in the last report—either by overwhelming a user with a slew of push notifications or guessing an appropriate MFA push time based on the users’ habits.
Legacy protocols and good old-fashioned social engineering also contributed to MFA defeat in our last incident breakdown.
The most consistent fix? Log everything and create an environment normalization process.
Ransomware and Vulnerability Exploits
For simplification and the ability to effectively communicate our observations, we classified all observed incidents and potential incidents that did not involve business email systems or ransomware deployment into the category of internal compromise.
These engagements involved a wide variety of compromise events including vulnerability exploit, vendor compromise, social engineering, insecure protocol exposure, physical attack, DDOS, and false positives.
The breakdown was as follows:
- Vulnerability Exploit: 33% of incidents observed
- Social Engineering: 28% of incidents observed
- False Positive: 20% of incidents observed
- Vendor Compromise: 8% of incidents observed
- Insecure Protocol: 8% of incidents observed
- DDOS: 3% of incidents observed

Vulnerability exploits were the most common root cause, yet just one vulnerability exploit was the result of a vulnerability published in the 12 months prior. All others had been published the previous year or before. One even dated back to 2017.
Some Suggestions Based on the Findings
Based on what we learned from the incidents we observed, as well as the data compiled from our risk assessments, we found these to be the suggestions that the industry needs to hear the most:
- IR Preparedness: Every organization needs to have developed and tested an incident response plan—and trained their employees on it. A quick and efficient response can mitigate damage. Oh, and your cyber insurance is not an IR plan.
- Vulnerability Management: Managing vulnerabilities goes beyond static scanning. Simply put, this is something we expect every organization to have in place or be working toward—but many fall short. In fact, because of this study, we created a vulnerability management service offering to help with process structure, enhancing exposure awareness, management of vulnerabilities, guiding remediation activities, and providing appropriate reporting.
- MFA Everything… Right Away: We recommend getting away from push notifications and focusing on revolving access tokens. All users must be properly trained on MFA defeat attacks to identify when and if they have been compromised.
- Logging and Monitoring: Log and store data to the highest financially acceptable level for the organization. Implement a program that focuses on log correlation and truly using the logs. Normalize your environment and then identify malicious activity through anomalous activities.
- Develop a Security-Focused Culture: Train users regularly and implement special training for managers and those with added privilege levels. Focus on security as a life skill and not just good for business. Oh, and don’t forget to include phishing exercises!
A Look Ahead to This Year’s Stories
So, that’s what we were seeing within the infosec landscape at the time of our last report. As we explore the incidents we’ve observed more recently, consider these statistics and suggestions. They will provide important context as to how far—or little—we’ve progressed as an industry since then.
Now, let’s dive into our incident breakdowns.
Like last year, we have categorized our cases into three major categories:
- Business Email Compromise (BEC) – Instances where attackers compromised email accounts used for business purposes.
- Ransomware – Cases where client environments were compromised, with attackers encrypting systems and/or exfiltrating data to demand a ransom for its return.
- Internal Compromise – Situations involving compromised systems that had not yet escalated to more damaging events. Some investigations resulted in no system compromise and have been classified as false positives.
We’ve anonymized all the information and logged data about incident causes and exploit tactics and techniques. The following series combines our analysis, interpretation, and recommendations to improve your internal incident response capabilities.
Here are some of the specific things we’ll be covering:
- EvilProxy MFA Defeat
- Conditional Access
- Application Allowlisting
- BEC Payload
- Ransomware Ingress Types & Exfiltration
- Planning & Cyber Insurance
- MDR =/= IR
- C2 Usage Decreases: LOTL
- Backup Destruction Decreased
- All Encryption Cases
- Malware Drive-By Download Attacks
We hope you can use this information to better educate yourselves and as a guide to staying one step ahead of attackers. Stay tuned for more.







